WordPress is a very popular CMS (Content Management System) software among developers as well as end-users. If you want to create a blogging website, you can use WordPress to create your blogging website within a few minutes. Why? Because installing and configuring WordPress is very easy. You can do it within a few clicks. Also, there is no need to pay for WordPress. It’s an open source software.
According to the official WordPress website:
41% of the web is built using WordPress. Many individual bloggers, small businesses, and Fortune 500 companies use WordPress.
Why is WordPress So Popular?
The WordPress software uses a combination of PHP and MySQL. The hosting cost for PHP is very cheap when compared to other languages. Additionally, PHP is very easy to learn. The low hosting cost and easy-to-use features make WordPress very popular among developers. There is one more thing that makes WordPress so popular—WordPress Plugins.
What are WordPress Plugins?
WordPress only has standard features such as creating pages and blogs. However, if you want to add any new functionality to your existing WordPress site, you can use plugins. The plugin is nothing but a PHP library. You can create your own plugin using PHP, or you can use a third-party plugin. Say, for example, you want to integrate a payment gateway into your WordPress website.
We have many plugins available in the WordPress marketplace. There is no need to develop the feature by yourself. You can simply install the payment gateway plugin with a few clicks on the WordPress admin panel. WordPress has options to install, update and uninstall a plugin. As of now, WordPress has more than 50,000 plugins.
Problem with WordPress Plugins:
WordPress is a very popular open source CMS software. Thus WordPress security vulnerabilities are inevitable. Why? Because not all developers/users focus on security in WordPress. The team of developers at WordPress does devote time to finding bugs and security issues. They always fix problems and release new patches immediately. And they always disclose vulnerabilities to the open internet community. So naturally, if you don’t update WordPress after a new fix is released, your website is vulnerable to hacking.
Like WordPress, WordPress Plugins are vulnerable to hacking. Why? For two reasons: (i) not all plugins follow the security protocol, and (ii) we can see the codes of the plugins. Hackers always analyze the code to find vulnerabilities in them. If you use a plugin, and the plugin is vulnerable to hacking, or you have not updated to the latest version, your website is then easily hackable. Since WordPress is open source, hackers know what the endpoints (URL) are, what data to use, and how to inject the scripts.
According to the WP Scan:
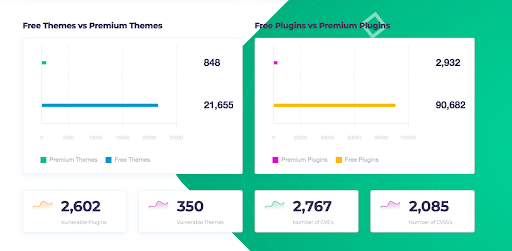
WordPress had 22,826 vulnerabilities.
From the above image, we can see that free themes and plugins have more vulnerabilities than premium/paid ones. So please be careful before installing a plugin to your website. Please read the security-related documents of a plugin before using it.
Vulnerability types in WordPress Plugins:
Here, I am listing some common vulnerability types present in the WordPress Plugins.
1.SQL Injection

WordPress uses the MySQL database. Every developer is advised to use the prepared (Example PDO) statement types while executing the SQL query. This is so that the statements use the concatenation operator to bind the values in the SQL query. This approach is vulnerable to hackers. Hackers can easily manipulate such a query and expose all the data in the database.
So you should use prepared statement types in PHP while executing SQL queries to avoid SQL injections. Also, do not use the concatenation in your SQL query to pass the data.
2.File Inclusion Exploits

This is a very dangerous problem. Sometimes, we enable write access in some directory (folder) of the server. If you do not configure this write access properly, hackers can directly inject malicious files into our servers and hack them. So, giving file/folder permission plays a very crucial role. Don’t blindly ignore the permission. Read more about folder/file permission and configure it.
3.Brute Force Attacks
A hacker knows the login URL. In brute force attacks, hackers enter multiple combinations of usernames and passwords using trial and error until the login is successful. WordPress does not limit login attempts. Therefore, hackers use bots to brute force their way into the server.
How to Avoid Vulnerabilities in WordPress
Passwords play a crucial role in security. So don’t use a default or weak password. Always use more than eight characters for a password and create a password with a mixed composition of lowercase, uppercase, and numbers. Do not use the names of pets or relatives in the password. You can now even check whether your password has been exposed to the open internet community.
Update the WordPress Plugins and themes as soon as the provider releases a new fix. Do not wait to update. This is because WordPress discloses vulnerabilities to the open community, and if you don’t do it immediately, your site is vulnerable to hacking. So don’t wait to update. Do it as soon as you get the notification.
Always use plugins and themes from the trusted sources. Do not use plugins and themes from untrustworthy sources.
How to Protect Your WordPress Website
You can protect your WordPress website in two ways.
Option 1: Regularly Update your Website & Check Plugins
Make sure you update plugins regularly — some of them patch important security vulnerabilities and so make your site secure. If you know how to, check whether the plugin is vulnerable for SQL Injections or Cross-site Scripting attacks. One way to do this is by keeping up with vulnerability trackers and websites that report new plugin vulnerabilities.
Option 2: Use Third-Party Solutions
If you can’t handle the tracking yourself, then you can use third-party solutions. Many providers offer solutions to address the above-mentioned vulnerabilities.
One of the more popular ones is Strattic. They offer a 30 day free trial and offers us a secure and scalable WordPress website by eliminating SQL injections (SQLi), and Cross-site Scripting (XSS). They also help optimize your website’s performance under heavy traffic, creating a seamless experience for users.

There is also Pantheon which offers Wordpress, Drupal, and WooCommerce hosting options. They offer full-page caching services along with multi-zone availability. Like Strattic, they also promote security.

Finally, there is BlueHost. BlueHost is a more commonly-known hosting service for Wordpress. They have automated security along with other features like eCommerce and marketing tools for WP sites.

Summary
Every developer and user in the IT industry loves WordPress. WordPress has helped many people earn money by creating their own blogs. Due to its open source nature, WordPress security vulnerabilities are inevitable. However, we can avoid them by following some standard security measures. Do not use default or weak passwords. Constantly update plugins and themes whenever an update is released. Do not use themes and plugins from untrustworthy sources.

