The vulnerability found conducted by a team led by J. Alex Halderman, computer scientist at the University of Michigan
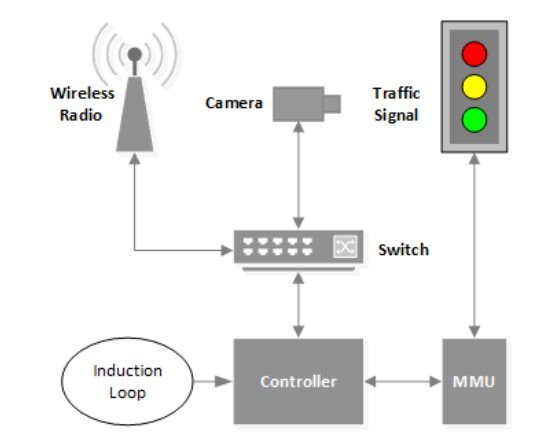
According to a paper researchers presented at the Usenix security conference in San Diego, in some cases, the controllers are part of an interconnected system and may communicate via radio frequency.
Halderman and his team found that the controllers could be set up remotely, via an FTP connection to a configuration database.
“An FTP connection to the device allows access to a writable configuration database. This requires a username and password, but they are fixed to default values which are published online by the manufacturer. It is not possible for a user to modify the FTP username or password,” say the researchers in the paper.
“Due to the lack of encryptions, any radio that implements the proprietary protocol and has knowledge of the network’s SSID can access the network,” explains the paper.
The actions supported by the controller include not just changing the lights based on an “if-then-else” logic, but also freezing them.
Attackers can control the lights as they wish, changing colors according to their needs