The WannaCry ransomware which lately affected thousands of computers around the world was full of coding errors, victims now may able to decrypt their files even after they’ve been encrypted.
The process of encryption:
WannaCry first reads the content from the original file then encrypt it and stores it into a file with the extension “.WNCRYT”. After that, it moves “.WNCRYT” into “.WNCRY” and removes the original file. This logic of the deletion may change depending on the location and attributes of the victim’s files.
After encryption:
If the files exist in an “important” folder (from the ransomware code like Desktop and Documents), then the original file will be overwritten with random data before deletion. In this case, there is no chance to recover the files. But If the files are located outside of the “important” folders, then the original files will be migrated to “%TEMP%\%d.WNCRYT” (%d indicates a numeric value).
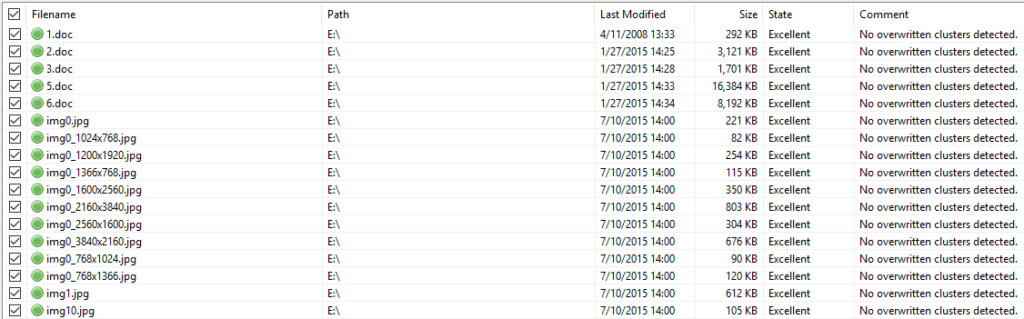
These files contain the original data and are not overwritten with random data, they are just deleted from the disk and that mean it is possible to recover the original files using recovery software.If the files are stored on a non-system drive, the malware will create the “$RECYCLE” folder and set the folder attributes to hidden to make the folder invisible in the Windows File Explorer. The malware will move the original files into this directory after encryption process.
If the files are stored on a non-system drive, the malware will create the “$RECYCLE” folder and set the folder attributes to hidden to make the folder invisible in the Windows File Explorer. The malware will move the original files into this directory after encryption process.
Because of some errors in the malware code, the original files remain in the same folder and are not moved into “$RECYCLE”. Also, the original files are removed in an insecure way.
All of that makes it possible to recover the removed files using recovery software.