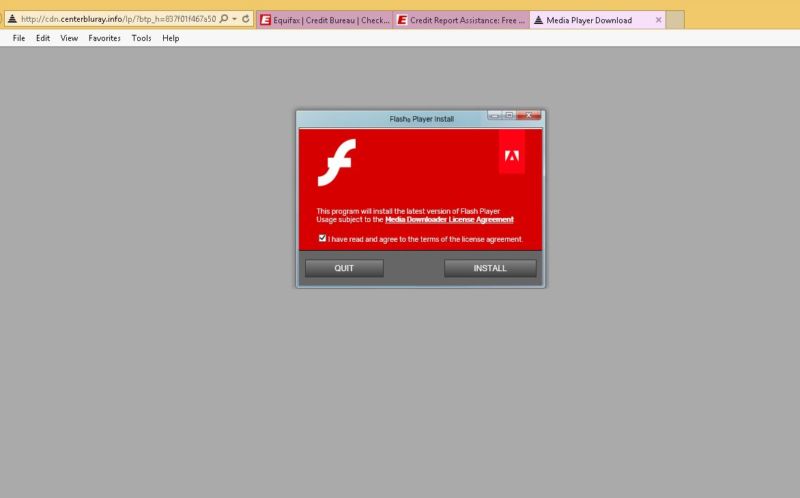
Randy Abrams, an independent security analyst by day, followed to visit the site Wednesday night to check what he said was false report he had just found on his credit report.
He was naturally incredulous. The site that earlier gave up personal data for practically every US person with a credit history was once repeatedly under the influence of attackers, this point trying to trick Equifax visitors into installing crapware Symantec calls Adware.Eorezo. Understanding a thing or two about drive-by campaigns, Abrams figured the possibilities were slim he’d see the download on follow-on visits. To fly below the radar, attackers frequently serve the downloads to only a select amount of visitors, and then only once.
Abrams tried anyway, and to his surprise, he encountered the bogus Flash download links on at least three subsequent visits. The picture above this post is the higher-resolution screenshot he captured during one visit. He also posted a video. It shows an Equifax page redirecting the browser to at least four links before finally beginning the Flash download at the same centerbluray.info page.
The file that got saved when Abrams clicked through is called MediaDownloaderIron.exe. This VirusTotal entry shows only Panda, Symantec, and Webroot showing the file as adware. This separate malware study from Payload Security dispenses the code is extremely obfuscated and takes pains to hide from reverse engineering. Malwarebytes hailed the centerbluray.info site as one that promotes malware, while both Eset and Avira provided similar malware alerts for one of the intermediate websites, newcyclevaults.com.
It’s not yet clear exactly how the Flash download page got displayed. The group-sourced study here and this autonomous assessment from researcher Kevin Beaumont both offered in the hours, make a strong case that Equifax was operating with a third-party ad network or analytics provider that’s bound for the redirects.
Take your time to comment on this article.