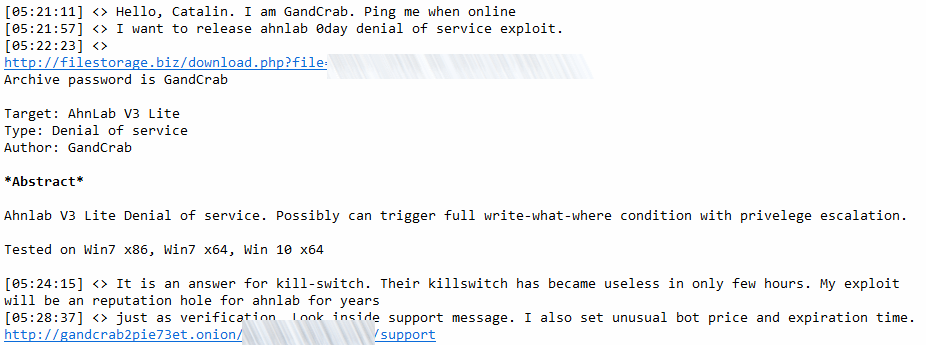
The author of GandCrab ransomware was furious since AhnLab released a vaccine for GandCrab ransomware. The GandCrab author contacted BleepingComputer with information about the new version of GandCrab saying it would include a zero-day that will cause a denial of service to AhnLab anti-virus software.
The author of the GandCrab claimed that this was payback for AhnLab releasing the vaccine app for GandCrab ransomware. The vaccine app simply creates a file on the user’s PC, if the ransomware runs it will believe that it has already affected this machine.
“Their killswitch has became useless” Crabs said to Bleeping Computer in Jabber IM conversation and via email, referring to the fact that he created and released a new ransomware version within hours after AhnLab released the vaccine (killswitch) app.
The new versions of the GandCrab 4.2.1 and 4.3 include the alleged exploit code for AhnLab anti-virus. BleepingComputer thought of releasing the article once the issue has been fixed however a security researcher from Malwarebytes has already found the issue.
#GandCrab new internal version: "4.3" in-the-wild ?#AhnLab #Exploit #bsod – MD5: 9f1aeca41d2da7ef2a441961077474f1 pic.twitter.com/5qAJI6hIPb
— Marcelo Rivero (@MarceloRivero) August 1, 2018
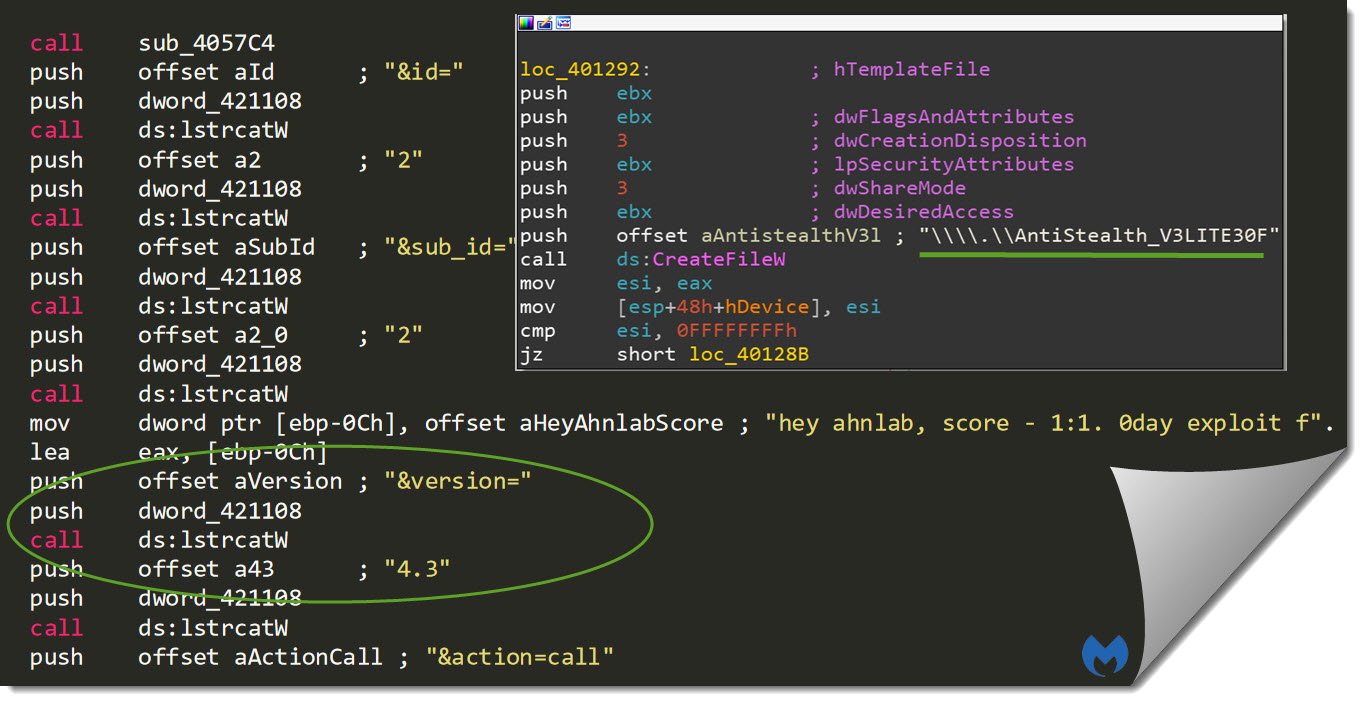
The two new variants of GandCrab contained the alleged exploit code for targeting AhnLab anti-virus.
“hey Ahnlab, score – 1:1,” one of the comments read, claiming to have returned the favour for releasing the vaccine app.
AhnLab didn’t seem to be worried about the issue as the company said that
“Our product is detecting the GandCrab ransomware before reaching the BSOD attack code,” Han said. “So, the BSOD attack code has very low chances on being executed.”
“Strictly speaking, that code is not exploit or zero-day code, It’s only a denial of service code,” he added. “It cause BSOD to our product, but we analyze it and it’s not easy to execute any extra payload by attack code.”
The company is planning to patch the product next week.
Take your time to comment on this article.