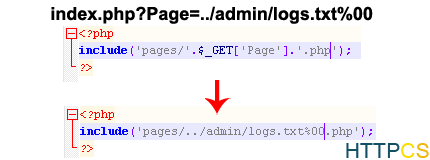
LittleSite is prone to a local file inclusion vulnerability because it fails to properly sanitize user-supplied input.
An attacker can exploit this vulnerability to obtain potentially sensitive information and to execute arbitrary local scripts in the context of the webserver process. This may allow the attacker to compromise the application and the computer; other attacks are also possible.
LittleSite 0.1 is vulnerable; other versions may also be affected.
http://www.example.com/littlesite/index.php?file=../../../../etc/passwd
If you are wondering what LittleSite is like I was then here is a description of it taken from the developer website.
LittleSite is an almost trivial PHP template for a static web site. Adding new content to a LittleSite is as simple as writing an HTML page and copying it to your web server. LS takes care of rendering all of your site’s pages in a consistent way. It also builds a navigation menu containing links to all your site’s pages. The page you are looking at right now is rendered by LittleSite.
LittleSite is suitable for small sites (a couple of dozen pages, perhaps) that do not require any dynamic page generation or form handling. (Blogs and shopping carts are examples of such dynamic pages, which LS does not handle.)
source: http://www.securityfocus.com/bid/43495/info