A security researcher was looking at some Google services hoping to find something worth a bounty until he found a bug and got $5000 bounty.
He came across “https://login.corp.google.com” which is a simple login page that seems to be for Google employees.
He said that every time the page is reloaded, a new image from “https://static.corp.google.com” is loaded directly into the page.
An example of image URL is: “https://static.corp.google.com/corpsso/images/PICT0004.jpg”
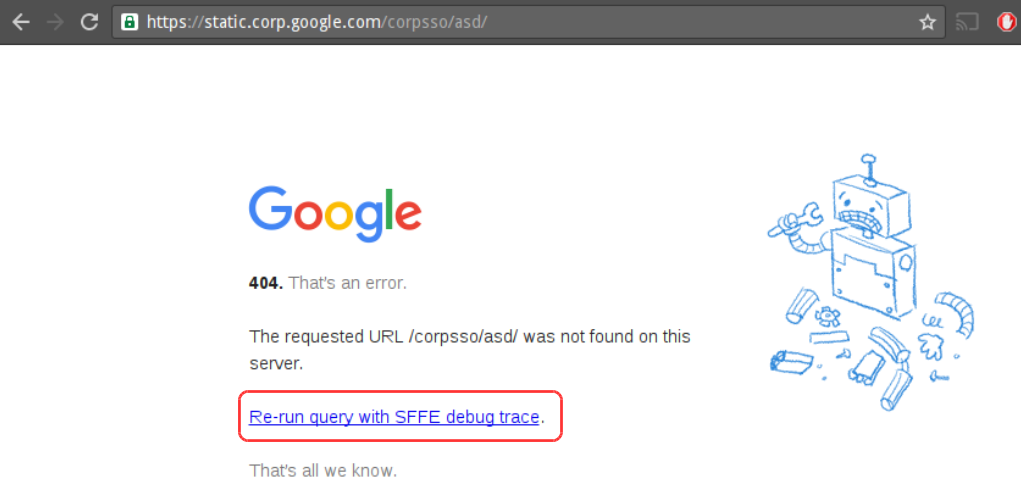
After many tries, he was able to get the default Google 404 error, but with one difference by going to the following URL:
https://static.corp.google.com/corpsso/asd/
A feature called “Re-run query with SFFE debug trace” pointed to:
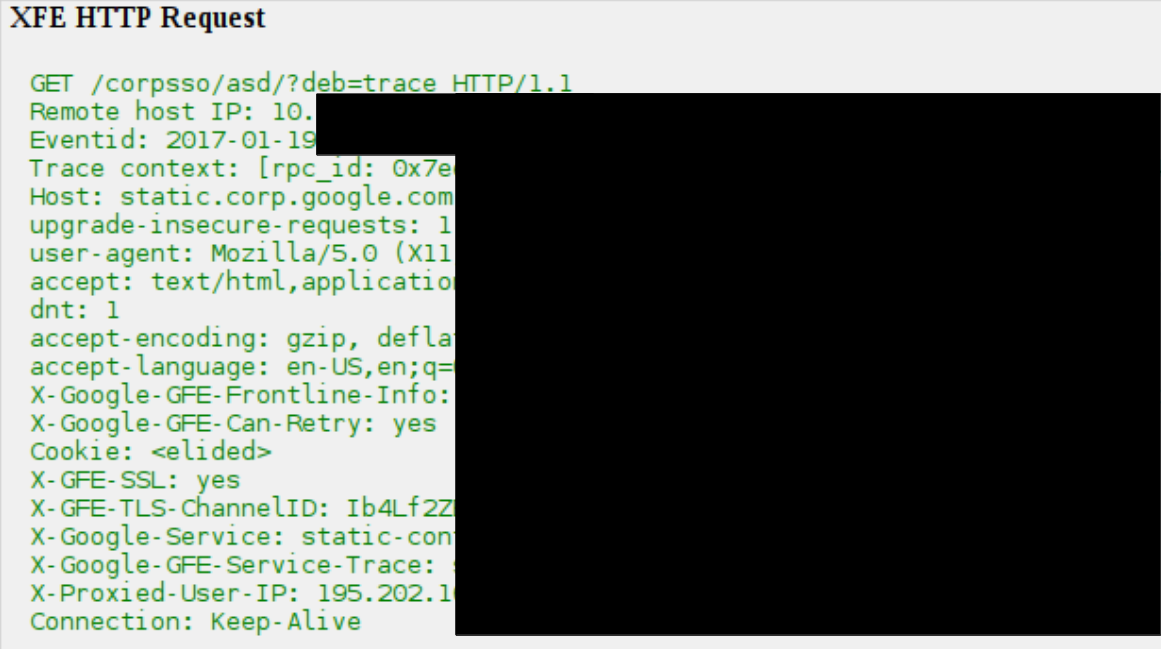
https://static.corp.google.com/corpsso/asd/?deb=trace
The debugging page contained various parts of information, providing the server name and internal IP, X-FrontEnd (XFE) HTTP requests, service policies, and other information that is related to Cloud Bigtable.
The issue was reported to Google on January 19, but a permanent fix was rolled out on March 16. Google rewarded the researcher $5,000 for this big, which is the maximum bounty of information disclosure bug. Google has spent out more than $9 million since the start of its bug bounty program in 2010, the highest single reward in 2016 was $100,000.