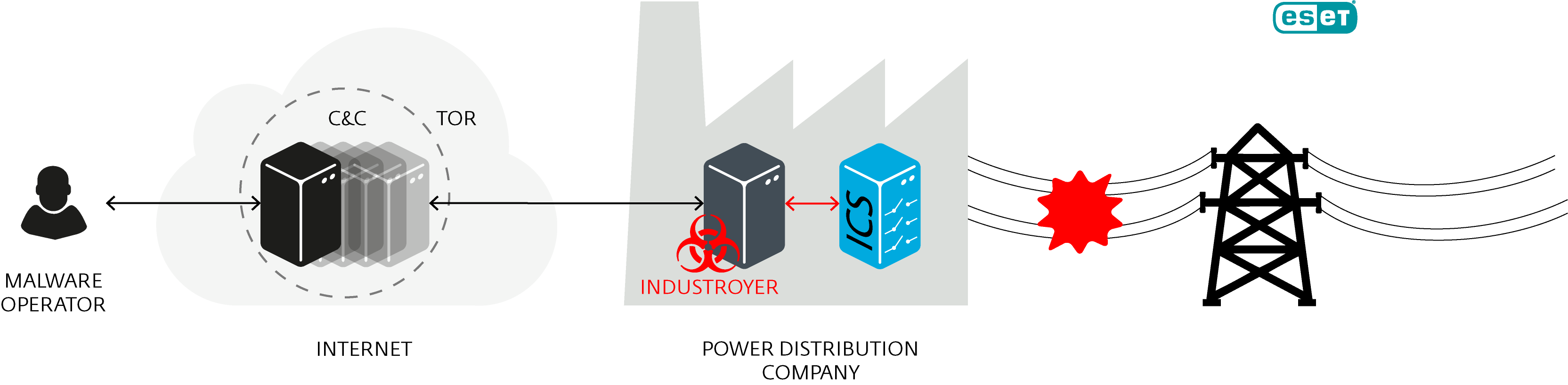
The 2016 cyber attack (latest December) on Ukraine’s Electric power network made the power outage for thousands of citizens for an hour and fifteen minutes in Kiev, ESET security researchers have analysed samples of malware, detected by ESET as Win32/Industroyer, capable of performing exactly that type of attack.
The malware has been called “Industroyer” or “CrashOverRide”. Security researchers said that “CrashOverRide” is one of the largest threat meant to damage manufacturing control systems, after Stuxnet, the first malware allegedly developed by the USA and Israel to destroy the Iranian nuclear facilities in 2009.
Anton Cherepanov (security researcher from ESET) said:
“Industroyer is a particularly dangerous threat, since it is capable of controlling electricity substation switches and circuit breakers directly. To do so, it uses industrial communication protocols used worldwide in power supply infrastructure, transportation control systems, and other critical infrastructure systems (such as water and gas).”
“These switches and circuit breakers are digital equivalents of analogue switches; technically they can be engineered to perform various functions. Thus, the potential impact may range from simply turning off power distribution, cascading failures and more serious damage to equipment. The severity may also vary from one substation to another, as well. Needless to say, disruption of such systems can directly or indirectly affect the functioning of vital services.”
The malware is not exploiting any application vulnerabilities, it only depends on four industrial communication protocols used worldwide in power supply infrastructure, transportation control systems, and other critical infrastructure systems.
“Industroyer is modular malware. Its core component is a backdoor used by attackers to manage the attack: it installs and controls the other components and connects to a remote server to receive commands and to report to the attackers.”