A new method named “Golden SAML” has been discovered by security researchers from CyberArk Labs allows cybercriminals forge authentication requests and access the cloud-based applications of organizations that use SAML-compatible domain controllers (DCs) for the authentication of users against cloud services.
Attackers can exploit Golden SAML to generate fake enterprise identities and forge auth to obtain access to valuable cloud resources in a federated environment.
Security Assertion Markup Language (SAML) is an open standard for exchanging authentication and authorization data between an identity provider and a service provider.
According to CyberArk:
“In a golden SAML attack, attackers can gain access to any application that supports SAML authentication (e.g. Azure, AWS, vSphere, etc.) with any privileges they desire and be any user on the targeted application (even one that is non-existent in the application in some cases).”
A SAML normal authentication attempt would look like the image below:
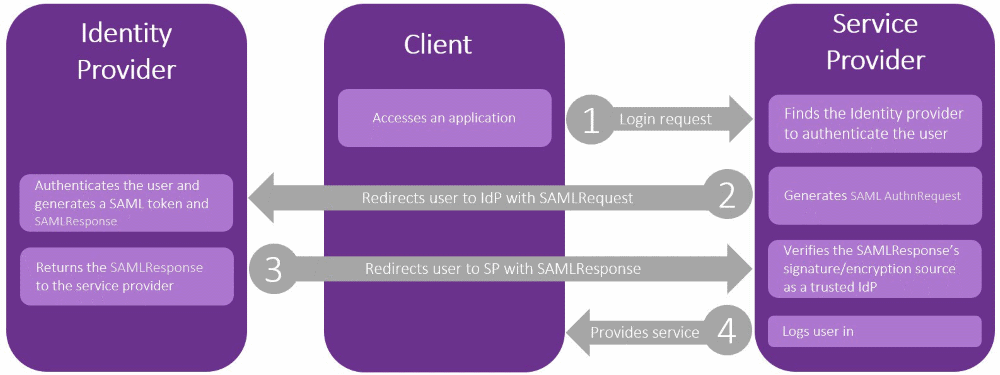
In a Golden SAML attack, the client will be the attacker, and the auth process will be changed to take place like in the image below:
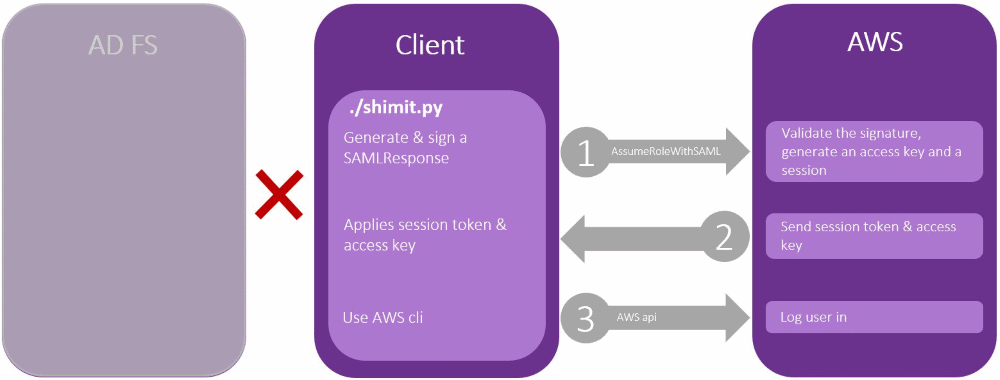
Attackers can use specific tools to obtain the IdP’s private key that is used to sign authentication tokens then use this private key to generate “golden tickets” for auth against cloud-based apps, posing as the IdP.
