Tech support scams aren’t something new or novel for the internet users. Almost all of us have come across such scams at least once in our lives.The scammers are constantly adopting new techniques to empower their scams. Once again, researchers have discovered a strategy for hijacking Google Chrome. The attackers supposedly employ the ‘Evil Cursor” technique to hijack the latest Google Chrome version 69.
Partnerstroka Scam Group Targets Google Chrome 69
Researchers at Malwarebytes Lab recently uncovered a tech support scam employing a new hacking strategy. The scammers supposedly use the “Evil Cursor” technique to hijack Google Chrome browsers. The campaign particularly affects the latest Google Chrome version 69.0.3497.81.
Reportedly, the attackers trick the users by redirecting them to some fake tech support page after employing ‘browlock’. The researchers have identified the scam group as Partnerstroka who have carried out scam campaigns in the past as well. As stated in their report,
“We have been monitoring a particular tech support scam campaign for some time which, like several others, relies on malvertising to redirect users to the well-known browser lockers (browlocks) pages. While it is common for crooks in this industry to reuse design templates, we were still able to isolate incidents pertaining to this group which we have been tracking under the name Partnerstroka.”
However, the new campaign seemed particularly designed against the latest Chrome. Although, the scam targets Firefox and Edge browsers as well, where the users may get an “authentication required” prompt. However, the technique is not as malicious as it works for Chrome where it employs ‘browlock’ and vigorous download strategies to trick users.
The Scam Employed “Browlock” And “Evil Cursor” Techniques
The researchers identified at least ‘16,000 malicious domains’ associated with this scam. Nonetheless, they do believe that the actual count could be much higher. Users clicking on these links are eventually redirected to fake tech support browlock pages. This involves using JavaScript functions that lock the browser pages, making a user unable to leave or close the page.
To achieve this goal, the attackers hijack the user’s mouse and control the cursor. Through the “evil cursor” technique, the users are tricked to believe that they clicked on the exit buttons normally and that the browser has actually frozen. Whereas, their cursors, actually controlled by the attackers, had never reached the user’s desired spot to click.
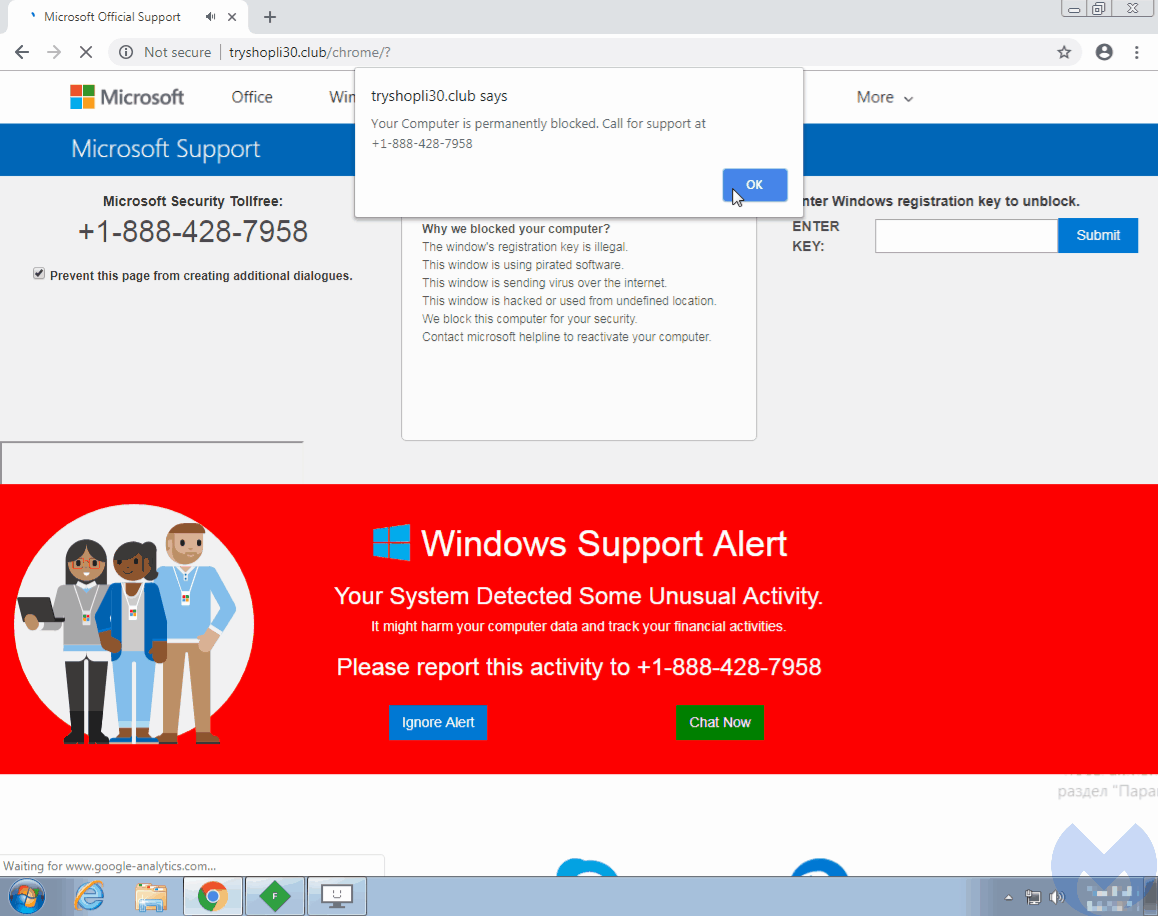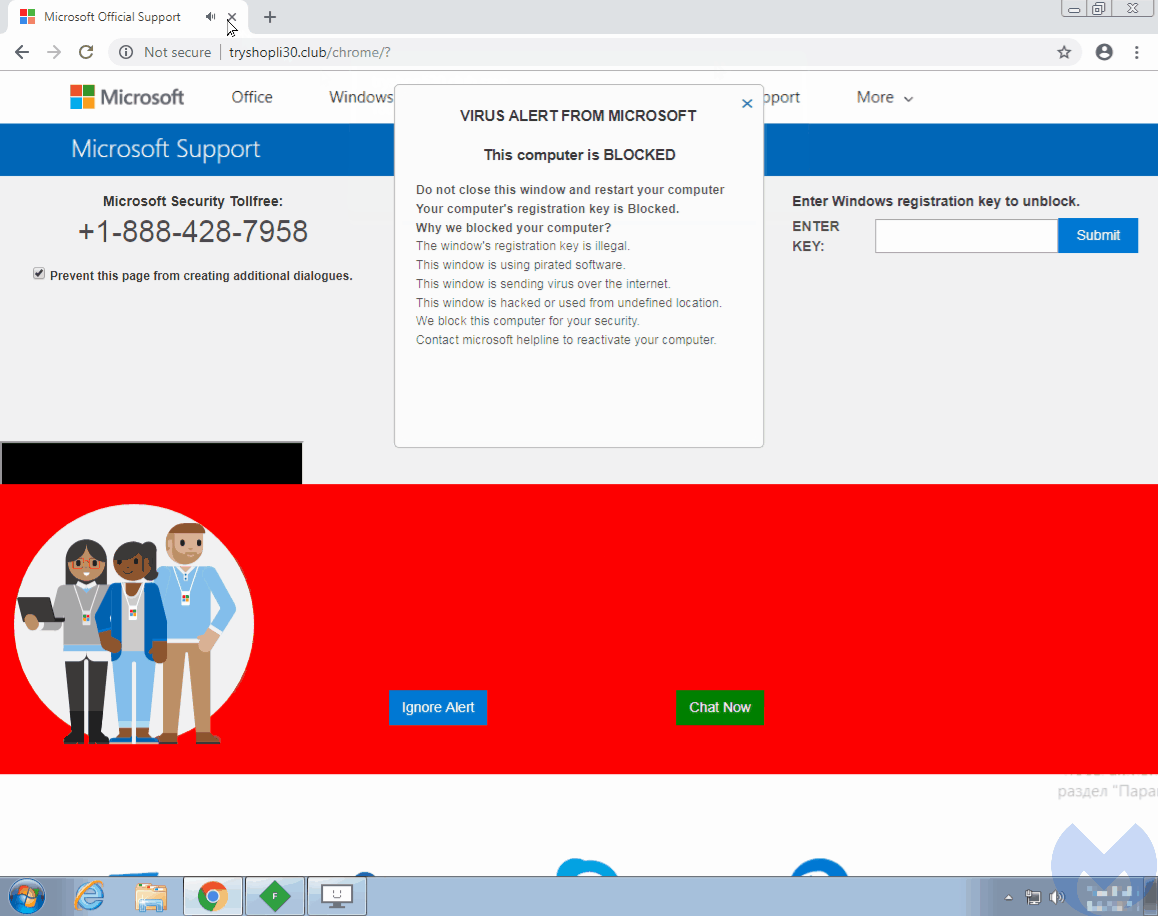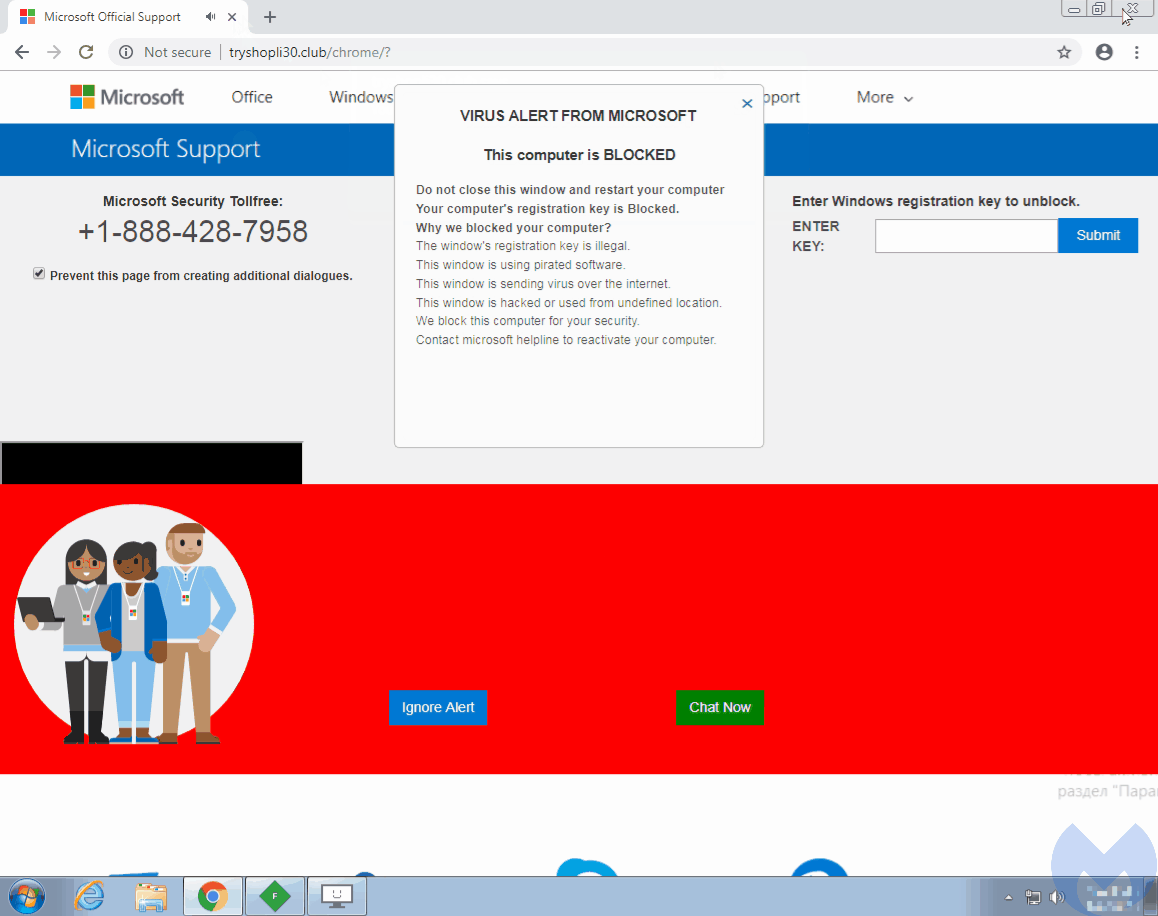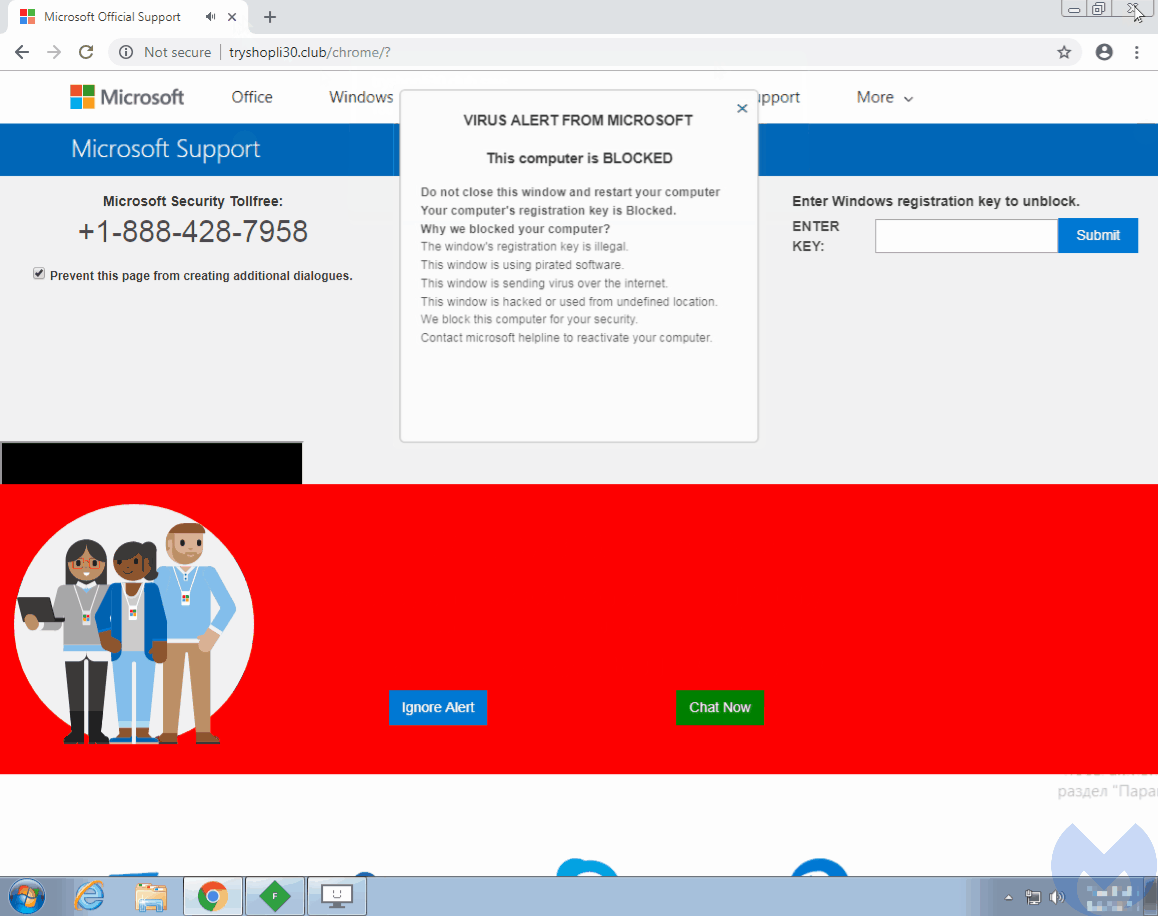
A simple code within the HTML body tag can achieve this.
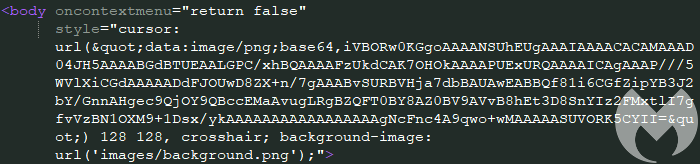
Explaining how this works, the researchers state that the “base64” decodes as a low-resolution image. While, the 128X128 pixel makes the user’s cursor “evil”.
The researchers found that the domains involved in spreading this scam mostly registered on NameCheap. The scammers use a plethora of tricks to capture users through various websites. Some of these sites even display “HTTPS” at the beginning of their URL. Thus, it becomes easier to con users after applying browlock and evil cursor techniques, making them immediately contact the scam contact number in a panic.
Take your time to comment on this article.

