Spiderfoot is an open source tool used for reconnaissance purpose. The tool is capable of gathering useful information about the target host through active and passive scanning options. There are different scanning options and modules available in the tool to set the scope of scanning the target hosts.
Spiderfoot Installation
Spiderfoot can be cloned from Github using the following command.
https://github.com/smicallef/spiderfoot
After cloning the tool, move to the spiderfoot directory to install the dependencies (requirements) using the following commands.
cd spiderfoot pip install –r requirements.txt
Using Spiderfoot
Spiderfoot has a graphic user interface that can be opened in a browser after running a webserver using the following command in the terminal.
python sf.py
The command starts a webserver at http://127.0.0.1:5001. Opening the preferred browser and typing the address opens the Spiderfoot dashboard as shown in the following screenshot.
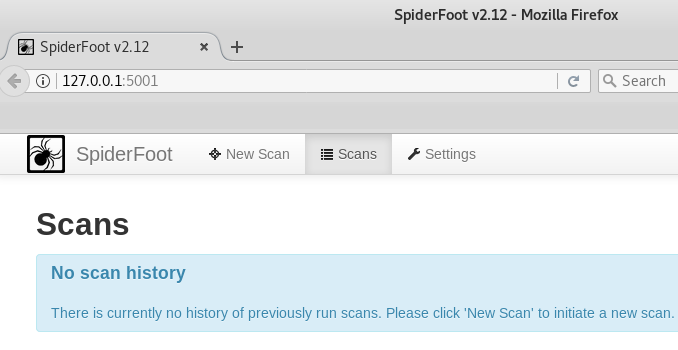
The dashboard contains scan history, new scan, and setting options. For fresh installation, there is no previous scan history. If we click the new scan tab, we see option to start the new scan along with the target seed field. The target seed field can be a target IP address, a domain name, or a sub-domain name.
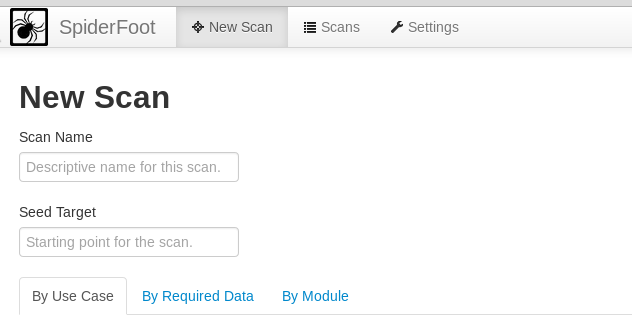
There are three types of configuration settings to define the scope of the scanning process. These include scan by use cases, required data, or modules. Each configuration setting has a number of options to choose from. For example, scan by use cases allows both, active and passive scanning of the target. It also gives the option to scan for all possible information or a range of information about the target.
Scanning by data option allows the collection of targeted data about the target host, such as emails, IP addresses, DNS record, content, cookies, WHOIS information, phone numbers, operating systems, TCP ports, SSL certificates, and so many other options.
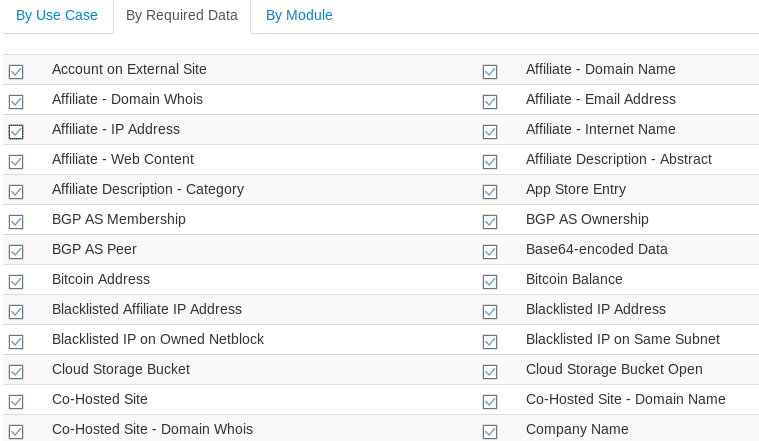
Similarly, scanning by modules option allows running a number of modules to acquire useful information about the target domain from public resources.
After setting up the desired configuration, hit the scan button from the dashboard to initiate the process. This opens up a new interface showing the scan progress.
For demonstration purposes, we have selected the passive scanning option for a test domain phptest.vulnweb.com. The status tab shows the current status of the scanning process. The browse-tab shows the type of data gathered and the unique data elements out of the total data collected.
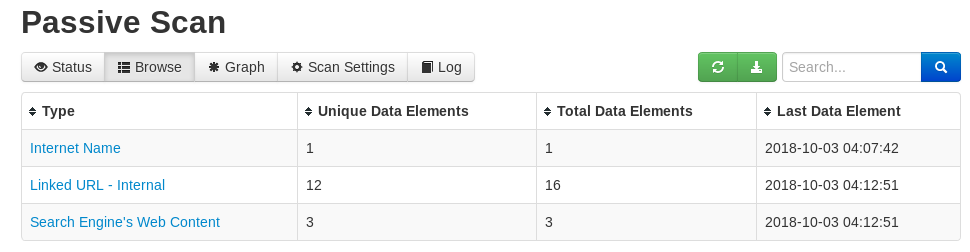
The graph option demonstrates the graphical representation of the scanned elements, unique elements, and the errors found during the scan. Similarly, the setting tab shows information about the target and the scan goals. There is also a log tab that records the events occurred during the scanning process.
What Bunny rating does it get?
Spiderfoot is very handy tool for open source intelligence and information gathering. The tool is sharp and loaded with a number of configuration options to customize the scanning goals. As a result we will be awarding this tool a rating of 4 out of 5 bunnies.




Want to learn more about ethical hacking?
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.