Researchers have noticed a new malware targeting Windows systems. Termed SystemBC malware, it is becoming increasingly popular among the cybercriminals owing to its astounding maliciousness. What’s alarming for users is that it directly paves the way for more malware attacks. It means a SystemBC malware detection directly indicates the presence of a second infection as well.
SystemBC Malware Attacks On A Rise
According to researchers from Proofpoint, SystemBC malware attacks are seemingly gaining strength. Stating their findings in detail in a blog post, researchers reveal the infectious traits of the malware.
The researchers caught this malware involved in several campaigns delivering other malware. They found the SystemBC served as proxy malware in these campaigns.
In June 2019, the researchers noticed the presence of the malware in Fallout EK campaign and Fallout EK and PowerEnum campaign delivering Maze ransomware and Danabot banking Trojan respectively. Later, in July 2019, they found it present with Amadey Loader distributed via RIG EK campaign as well.
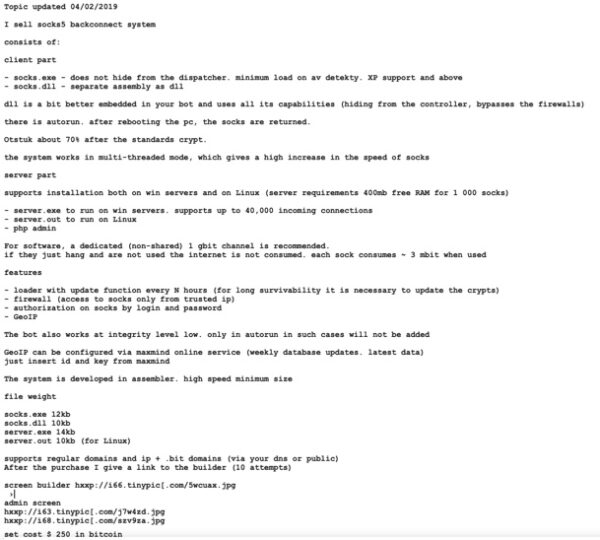
Proofpoint also discovered an alleged advertisement regarding the malware, which made them believe its being sold on the “underground marketplace”.
As stated in their blog,
We found an advertisement… on an underground forum that described a malware named “socks5 backconnect system” that matched the functionality of the malware seen in the above campaigns. To differentiate from other malware leveraging SOCKS5, we dubbed the new malware “SystemBC” based on the URI path shown.
Source: Proofpoint
They could also see screenshots of malware’s C&C panel, administrator panel, and the SystemBC builder with the advertisement.
Written in C++, the malware, upon reaching the victim device, creates SOCKS5 proxies to let the attackers “hide the malicious traffic associated with the other malware”.
The researchers have given a detailed technical analysis of the malware in their blog post.
A Challenging Malware To Combat
In the most recent instance, the researchers caught this malware infecting Windows systems.
The Fallout exploit is used to download the Danabot banking Trojan and a SOCKS5 proxy which is used on the victim’s Windows system to evade detection of command and control (C&C) traffic.
Owing to the unique property of hiding bad traffic and facilitating a second malware infection, the researchers deem it a challenging malware triggering new threats.
The synergy between SystemBC as a malicious proxy and mainstream malware creates new challenges for defenders relying on network edge detections to intercept and mitigate threats like banking Trojans.
Let us know your thoughts in the comments.

