Biometric data and device identifiers have long been recognized as a means of tracking users. While the two parameters separately pose a risk to users’ privacy, their combination can become even more dangerous. Researchers have found how an adversary can profile users by linking biometrics with device identifiers that leak users’ identity.
Linking Biometrics and Device Identifiers
A team of researchers shared a detailed study about how linking physical biometrics to users’ device identifiers allows profiling.
In their study, they found that the cross-modal identity leakage allows an adversary to gather explicit information about the users. Briefly, such attacks require continued and prolonged eavesdropping on individuals in cyber-physical spaces.
The setup merely includes eavesdropping tools including hidden cameras, microphones, a WiFi/Bluetooth/ZigBee sniffer, or an integrated solution like WiFi spy microphone. Therefore, gathering detailed information from facial and acoustics to device identifiers such as Mac Addresses, trigger both insider and outsider threats.
In other words, researchers state that not only an organization (or an individual employee) can eavesdrop on colleagues via this setup, but an outside adversary can also perform such attacks. The attack setup does not generate any traffic. Hence, the activity can stealthily go on for a long time.
The following image depicts a possible attack scenario. Whereas, details of the research are available in the white paper.
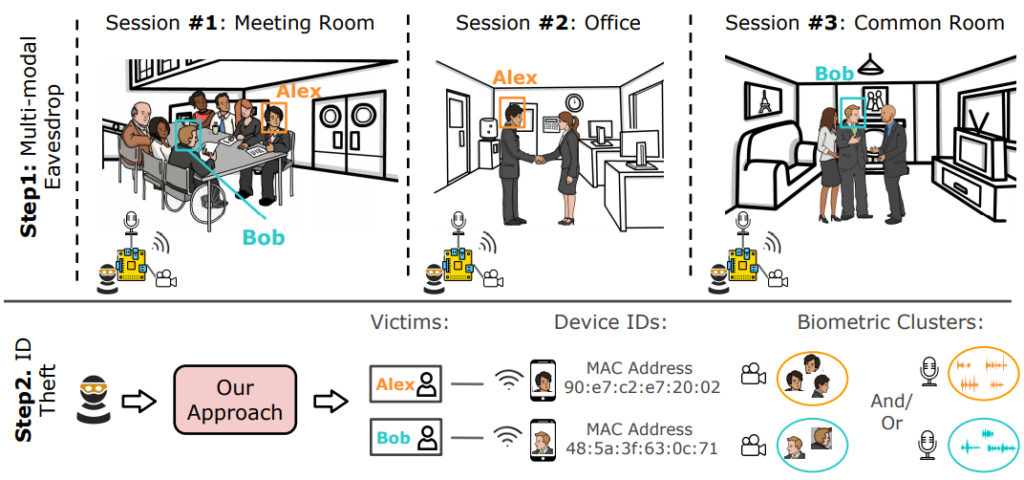
Possible Mitigations
Although, a successful attack can allow the attackers find precise details about the victim. However, when the target is in a crowd, there may arise some pattern ambiguity allowing the target to ‘Hide in a Crowd’.
Since the limitation of the attack does not rule out the severity of this strategy, the researchers have advised some mitigations.
One possible mitigation that users can do is to frequently scan spaces for hidden cameras and microphones, or spying devices. Though, this requires cooperation from the users and awareness about hidden devices.
Another mitigation is the randomization of Mac addresses on the device. Although, an attacker may still be able to obtain the true Mac addresses of the device.
Reducing dependency on smart home devices is also desirable for minimizing the chances of spying by potential attackers.
Let us know your thoughts in the comments.

