Heads up, WhatsApp users! Two separate vulnerabilities in WhatsApp could potentially expose sensitive user data to the attackers. Since the patches are out, make sure to update your Android devices with WhatsApp version 2.21.4.18 or higher.
WhatsApp Vulnerabilities Triggering MiTD Attacks
Researchers from CENSUS Labs have recently shared details about two WhatsApp vulnerabilities that allowed hacking target phones. Specifically, the bugs affected the WhatsApp for Android client allowing an adversary to steal sensitive data.
Briefly, exploiting both the vulnerabilities could result in man-in-the-disk (MiTD) attacks that execute by exploiting external storage.
The bugs affected how WhatsApp established a secure connection for each session via TLS 1.3 and 1.2. As described in their post,
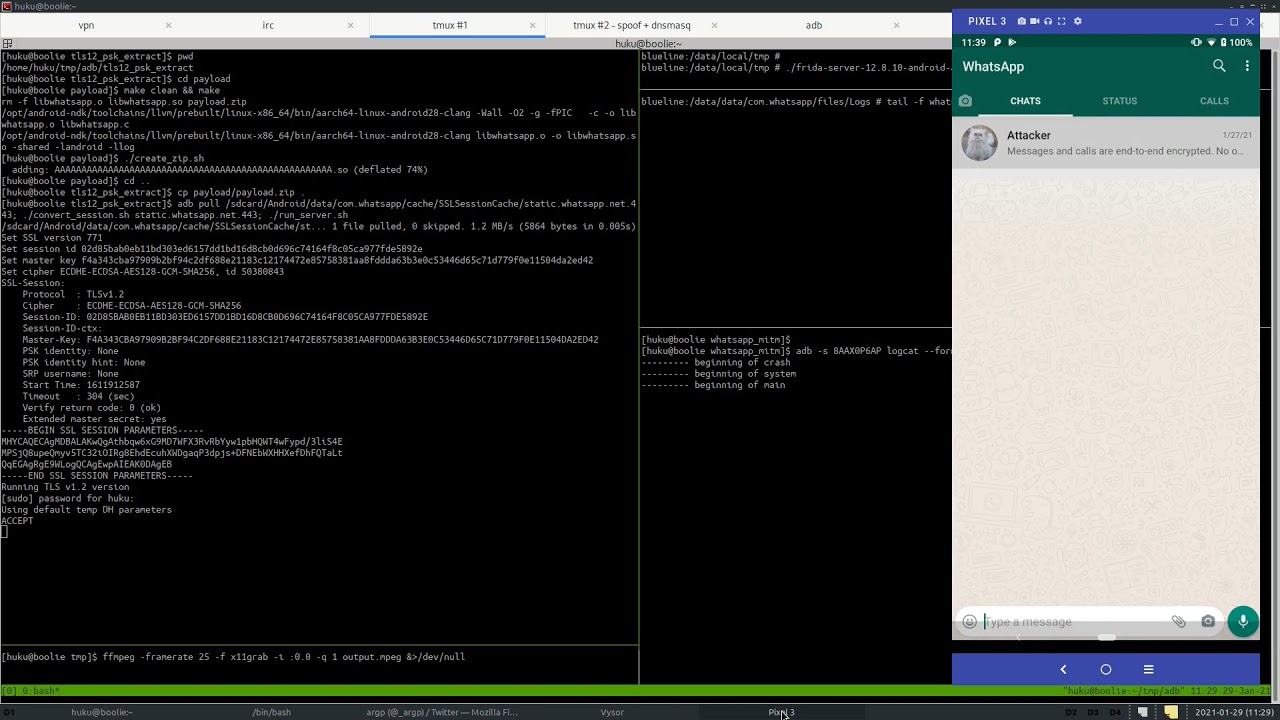
The problem is that WhatsApp stores the aforementioned TLS session information in the directory returned by Context.getExternalCacheDir(). This directory lies under the external storage of /sdcard. Any Android app holding the READ_EXTERNAL_STORAGE or WRITE_EXTERNAL_STORAGE permission could gain read / write access to these files through the filesystem, on Android 10 and previous versions of Android. Alternatively, these files were indexed and made available to other apps through the Media Store content provider on Android 9 and previous versions of Android.
Thus, an adversary can easily exploit the bugs by sending a maliciously crafted message to the target WhatsApp user. This can allow the attacker to steal sensitive details, such as session tokens, as well as remote code execution.
The following video demonstrates stealing WhatsApp TLS session secrets.
Whereas, this video demonstrates remote code execution attacks via WhatsApp vulnerabilities.
Details about the bugs are available in the researchers’ post.
Patches Rolled Out
Upon discovering the bugs, CENSUS Labs reported them to Facebook. These vulnerabilities typically affected Android devices, evidently, up to Android 9, and presumably, Android 10.
Eventually, the tech giant fixed the bugs with the release of WhatsApp version 2.21.4.18.
Though WhatsApp has fixed the bugs, these flaws also potentially risk other apps as well. According to the researchers,
There are many more subsystems in WhatsApp which might be of great interest to an attacker. The communication with upstream servers and the E2E encryption implementation are two notable ones. Additionally, despite the fact that this work focused on WhatsApp, other popular Android messaging applications (e.g. Viber, Facebook Messenger), or even mobile games might be unwillingly exposing a similar attack surface to remote adversaries.
Let us know your thoughts in the comments.