Every device connected to a network—whether a local network one or the Internet—is assigned an Internet Protocol (IP) address that serves as its identifier. This means that an IP address is pretty much like a fingerprint, and since it is found in every device, it can become crucial when seen in a crime scene.
But how exactly can IP data help in cybersecurity? Why does it become such a critical source of insight when implementing specific cybersecurity strategies? This post tackles three reasons why IP data is vital for cybersecurity, with examples that use data gleaned from a bulk IP lookup tool.
IP Data Shows a Device’s Location
IP geolocation data is among the most used IP intelligence not only in cybersecurity but also in marketing, digital rights management (DRM), and other business processes. Knowing the location of malicious IP addresses, for one, can help map out which countries or regions are the sources of most attacks or fraudulent transactions.
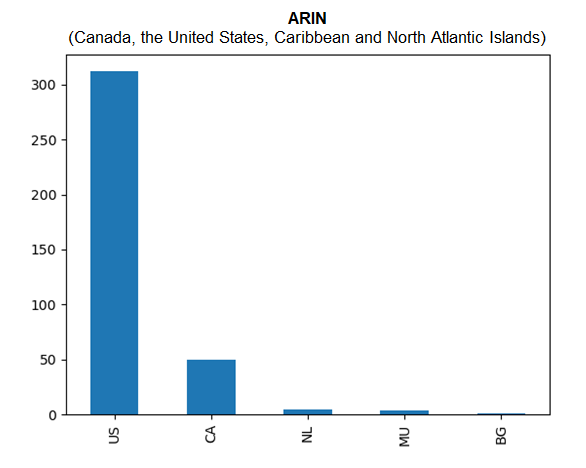
To illustrate, this Cybersecurity Ventures article utilized the IP data of an entire blocklist of IP addresses from Spamhaus, specifically its Don’t Route or Peer (DROP) List. The specific DROP list contained 964 IPv4 addresses, and IP geolocation data helped determine that the sources of malicious IP addresses are widespread. However, the study also pinpointed top source countries in regions managed by three registries.
The IP data revealed that in Asia-Pacific, most of the malicious IP addresses in the sample are located in China.
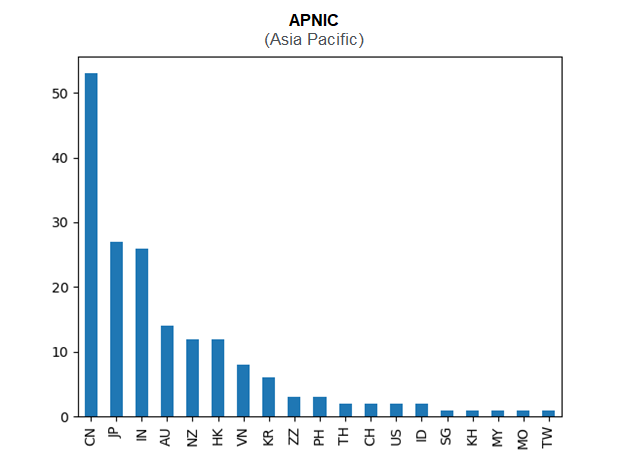
In the European region, most of the sampled IP addresses originated from the U.K., while the U.S. is the primary location of malicious IP addresses in North America and the Caribbean.
IP Data Could Reveal an Infrastructure’s Owner
Among the information that a bulk IP lookup returns is the IP addresses’ Internet service providers (ISPs), which points to the organizations that manage them. This information can help trace the origin of a malicious email or traffic.
Consider a scenario where a welcome email from a Salesforce look-alike domain is sent to a new employee of a Salesforce client. The email domain resolves to the IP address 211[.]159[.]168[.]145. An IP lookup reveals that its ISP is Tencent Cloud Computing.
While Tencent is a legitimate cloud service provider, Salesforce IP addresses, such as 101[.]53[.]160[.]0, would likely point to Salesforce[.]com as its ISP.
The inconsistency in the IP data can alert security teams of a possible typosquatting or phishing campaign to immediately investigate and prevent employees from receiving a phishing email.
IP Data Includes Associated Domains
When it comes to malicious IP addresses, it might be tempting to block them. In fact, IP-level blocking could be recommended for the utmost protection of banks and other financial institutions.
In some industries, however, IP-level blacklisting could also mean blocking potential clients since some domains use shared IP addresses. There could be one or two malicious domains hosted on the IP address, but not all of the domain names should be blocked.
A bulk IP lookup can help organizations determine if safe domains resolve to an erring IP address. The IP address 64[.]32[.]26[.]89 is an example of this. It has been tagged as an indicator of compromise (IoC) in the Hafnium attack targeting vulnerabilities in Microsoft Exchange Server.
However, 64[.]32[.]26[.]89 is a shared IP address, with more than 3,000 domain names resolving to it over time. Blocking it would mean blocking all of these domains, which might not be a wise business decision for some businesses. E-commerce companies, for instance, would want to reach as many customers as possible. Blocking the IP would mean blocking thousands of potential customers, too.
—
IP data is a crucial source of information that can help cybersecurity teams strengthen their strategies. By knowing the locations, owners, and associated domains of IP addresses, they can make balanced decisions.


