While browser fingerprinting has long been a privacy-intrusive technique for users, it can now pose a direct threat to users’ security. That’s because researchers have devised a new attack strategy “Gummy Browsers” that exploits fingerprinting by spoofing the target users’ browsers.
Gummy Browsers Attack Trick Browser Fingerprinting
A team of researchers from Texas A&M University and the University of Florida has shared details about how browser fingerprinting can risk users’ security.
Briefly, browser fingerprinting is a common user tracking approach that different apps and websites use to identify and track visitors. For this, the apps or websites log users’ device and browser details, IP addresses, system information, and more. They then track the users’ browsing habits and interests and build a profile by linking all this data.
This profile potentially includes identifiable user information that an adversary can exploit. That’s what the researchers have demonstrated in their recent study.
How it all works
As elaborated in a detailed research paper, the team has devised “Gummy Browsers” – an attack strategy that mimics web browsers. The idea is to bluff sites and apps using browser fingerprinting to get the target user’s data.
The idea is that the attacker ? first makes the user ? connect to his website (or to a well-known site the attacker controls) and transparently collects the information from ? that is used for fingerprinting purposes (just like any fingerprinting website ? collects this information). Then, ? orchestrates a browser on his own machine to replicate and transmit the same fingerprinting information when connecting to ?, fooling ? to think that ? is the one requesting the service rather than ?. As a consequence, if ? populates targeted ads for ? based on only browser fingerprints, ? can now start seeing the same or similar ads on his browser as ? would see. This will allow the attacker to profile ? and compromise ?’s privacy.
In their study, the researchers successfully implemented the attack using three script injection-based techniques to mimic browsers. These include browser settings, debugging tools, and script modification.
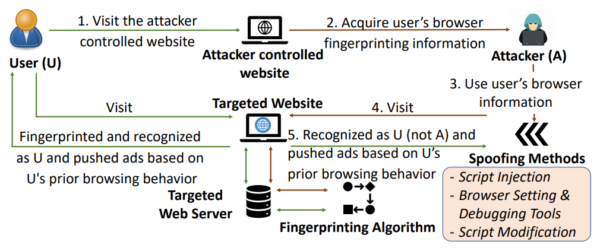
Gummy Browsers attack model (Source: Liu et al.)
After that, they could easily validate the attack effectiveness by employing two fingerprinting algorithms, Panopticlick and FP-Stalker.
Such an attack can take place remotely without being detected. Also, it employs no cookies and merely relies on browser spoofing.
Once an adversary gets a victim’s browser fingerprints, the adversary can use it maliciously for a long period of time.
Potential Exploitability And Limitations
Given the accuracy of profiling and browser fingerprinting obtained, Gummy Browsers attack poses a serious real-world threat.
According to the researchers, the huge adaptation of browser fingerprinting globally now raises concerns about users’ online security.
The impact of Gummy Browsers can be devastating and lasting on the online security and privacy of the users, especially given that browser-fingerprinting is starting to get widely adopted in the real world. In light of this attack, our work raises the question of whether browser fingerprinting is safe to deploy on a large scale.
Although, the present study has shown some limitations that may affect the attack efficiency. For instance, a change in browser fingerprints may result in partial accuracy of spoofed results. Still, the ease of execution of these attacks doesn’t make it difficult for an adversary to reprofile a target user.

