Researchers have found more than 50 different security vulnerabilities affecting hundreds of industrial devices. Identified as OT:ICEFALL, these vulnerabilities mainly exist in operational technology (OT) industrial devices from 10 different vendors. Hence, industries using vulnerable OT devices must apply mitigation strategies to avoid potential exploits.
About OT:ICEFALL Vulnerabilities Threatening Industrial Devices
According to a recent report from Forescout Vedere Labs, numerous operational devices from the following ten vendors are riddled with OT:ICEFALL vulnerabilities. The researchers named the flaws “Icefall” after the second stop on Everest after Base Camp.
Regarding the vulnerable devices and vendors, the researchers have shared the following list. It mentions only nine vendors, as the tenth vendor exposed to four vulnerabilities is still under disclosure.
- Bently Nevada: 3700, TDI equipment (condition monitors)
- Emerson: DeltaV and Ovation (distributed control system), OpenBSI (engineering workstation), ControlWave, BB 33xx, ROC (remote terminal unit), Fanuc, PACsystems (programmable logic controller)
- Honeywell: Trend IQ (building controller), Safety Manager FSC (safety instrumented system), Experion LX (distributed control system), ControlEdge (remote terminal unit), Saia Burgess PCD (programmable logic controller)
- JTEKT: Toyopuc (programmable logic controller)
- Motorola: MOSCAD, ACE IP gateway (remote terminal unit), MDLC (protocol), ACE1000 (remote terminal unit), MOSCAD Toolbox STS (engineering workstation)
- Omron: SYSMAC Cx series, Nx series (programmable logic controller)
- Phoenix Contact: ProConOS (logic runtime)
- Siemens: WinCC OA (SCADA)
- Yokogawa: STARDOM (programmable logic controller)
The researchers have shared a detailed technical report sharing their analysis. Briefly, they discovered 56 different vulnerabilities that predominantly fall into the following categories.
- Remote code execution
- Denial of service (DoS)
- File/firmware/configuration manipulation
- Authentication bypass
- Compromise of credentials
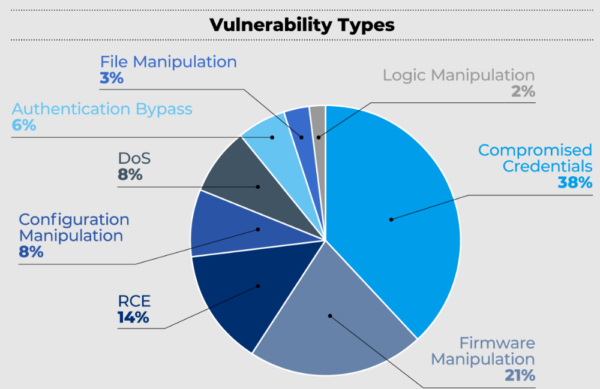
Source: Forescout
These “insecure-by-design” vulnerabilities demand utmost attention since the criminal hackers are always searching for such bugs to compromise industries via malware, such as TRITON, Industroyer2, and others. As stated in their post,
Abusing these types of insecure-by-design, native capabilities of OT equipment is the preferred modus operandi of real-world industrial control system (ICS)… These vulnerabilities, and the proven desire for attackers to exploit them, demonstrate the need for robust, OT-aware network monitoring and deep-packet-inspection (DPI) capabilities.
Recommended Mitigations
The vulnerable devices affect the industrial control systems globally. Hence, industries must scan their infrastructure to detect the existence of vulnerable equipment and patch the bugs. Some mitigation strategies that researchers recommend include,
- Discover and inventory vulnerable devices
- Enforce segmentation controls and proper network hygiene
- Monitor progressive patches released by affected device vendors
- Monitor all network traffic for malicious packets
Moreover, the researchers also highlight the significant drawback of certifying insecure-by-design products that can impart a false sense of innate security. Thus, businesses must try their best to procure secure-by-design products. At the same time, vendors should input maximum efforts toward product security. Together, all entities must work towards developing an environment focusing on “robust” instead of “merely functional” security controls.

