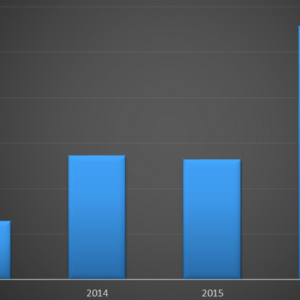
The number of attacks aimed at industrial control systems (ICS) increased by 110 percent in 2016 compared to the previous year, according to data from IBM Managed Security Services.
The company has attributed this significant increase to brute force attacks on supervisory control and data acquisition (SCADA) systems.
Attackers apparently used a penetration testing framework made available on GitHub in January 2016. The tool, named smod, can be used to conduct a security assessment of the Modbus serial communications protocol and it includes brute-force capabilities.
“The public release and subsequent use of this tool by various unknown factors likely led to the rise in malicious activity against ICS in the past 12 months,” explained Dave McMillen, senior threat researcher at IBM Managed Security Services.
The United States was both the top source and top destination of ICS attacks observed by IBM since the beginning of the year until the end of November. Experts pointed out that this is due to the U.S. having the largest number of Internet-connected ICS systems.
IBM said 60% of the attacks it had spotted came from the U.S., followed by Pakistan (20%), China (12%), the Netherlands (5%) and India (4%). Nearly 90% of ICS attacks were aimed at the United States, with China, Israel, Pakistan and Canada also on the list of targets.
SAVE THE DATE: ICS Cyber Security Conference | Singapore – April 25-27, 2017
IBM has described three recent ICS attacks that made headlines. One of them is the 2013 New York dam attack disclosed by the U.S. Justice Department in March. Authorities said Iranian hackers managed to compromise the system used to control the dam.
Another high-profile attack was the one that targeted the Ukrainian energy sector in December 2015. The attacks, attributed to the Russian government, caused severe power outages. Similar outages occurred this year, but Ukraine has yet to confirm that they have been caused by cyber attacks.
IBM also described the SFG malware attacks documented in July. Initial reports said the malware, which appeared to be the work of a state-sponsored actor, targeted at least one European energy company. However, experts later determined that the malware did not seem to have any special interest in ICS systems and was more likely developed and used by cyber criminals.