Verizon Messages (Message+) is a group of software clients available for mobile, desktop, and web allows users to send and receive messages across multiple types of devices.
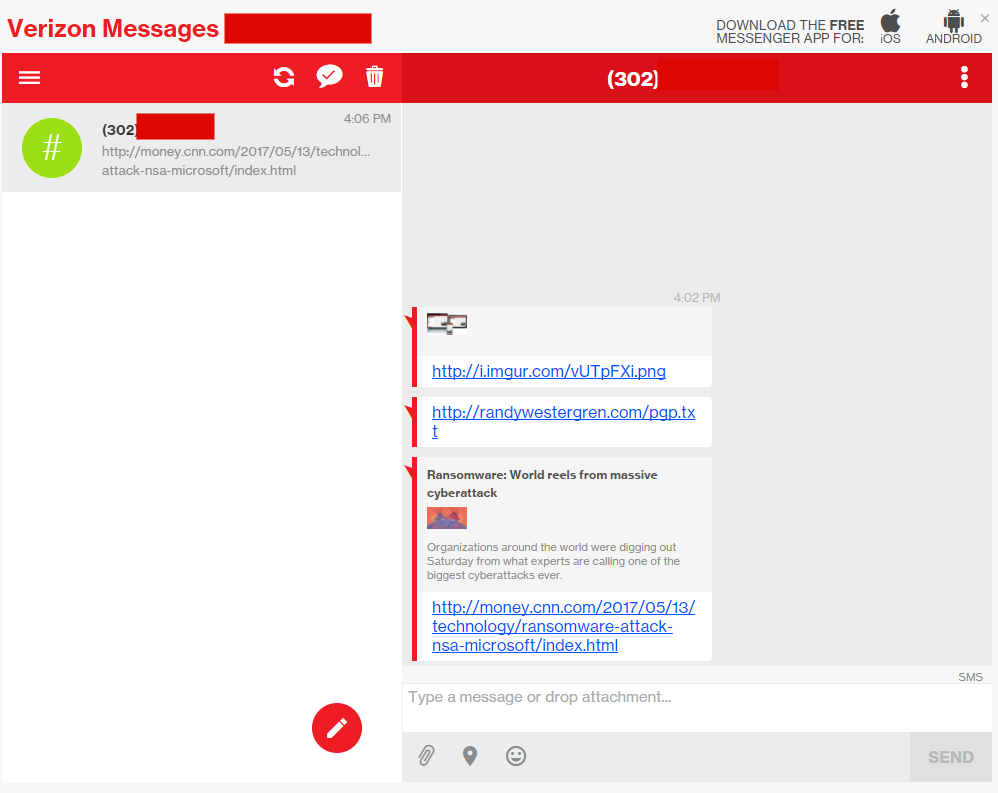
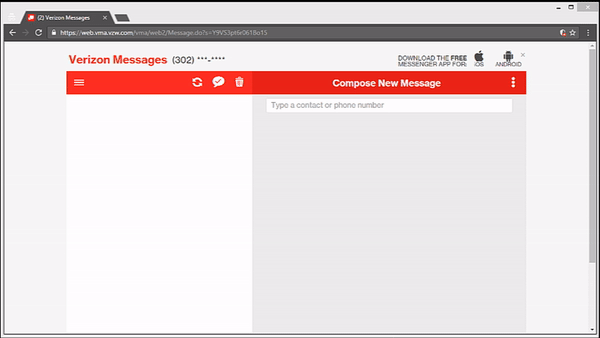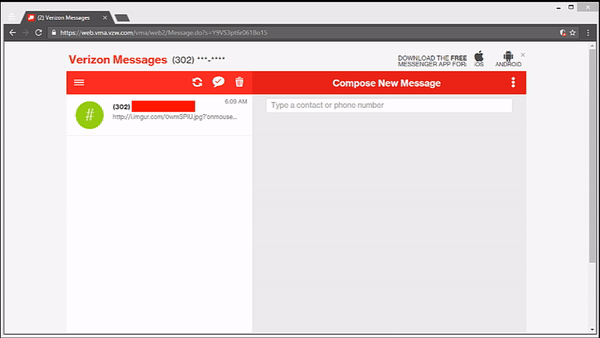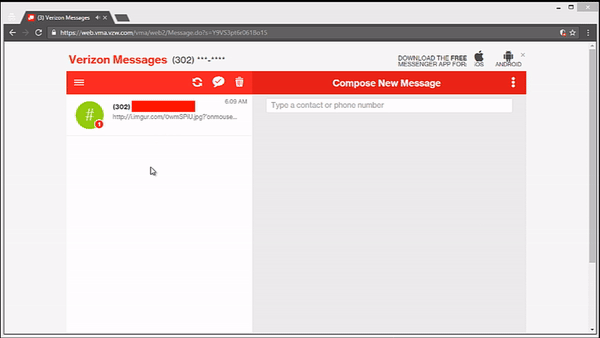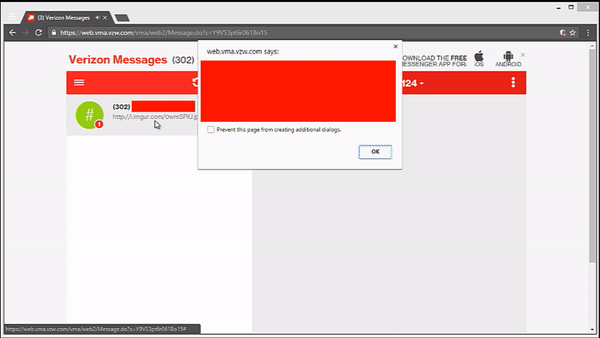
Randy Westergren (a security researcher) installed the Android app and signed up, and logged into the web app and start using it. He noticed that messages including links were being displayed with a preview/summary embedded in both the web and mobile interfaces. The researcher sent some URLs to a test account to see how each type of link is rendered, and he noticed that adding single quotation marks to a URL allowed him to break out of the HREF tag and execute some JavaScript code.
He was able to force the anchor to cover the user’s entire screen with inline styles, the onmouseover event triggers immediately upon opening the message:
An attacker could control the page with a specially crafted text message, ending in a complete takeover of the user’s session and this will allow the controlling of any functionality, including sending and receiving SMS messages on the side of the victim.
Randy sent the PoC and screenshots/video of the security issue to Verizon. As always, they were quick to respond, appreciated the report, and patched the issue quickly.