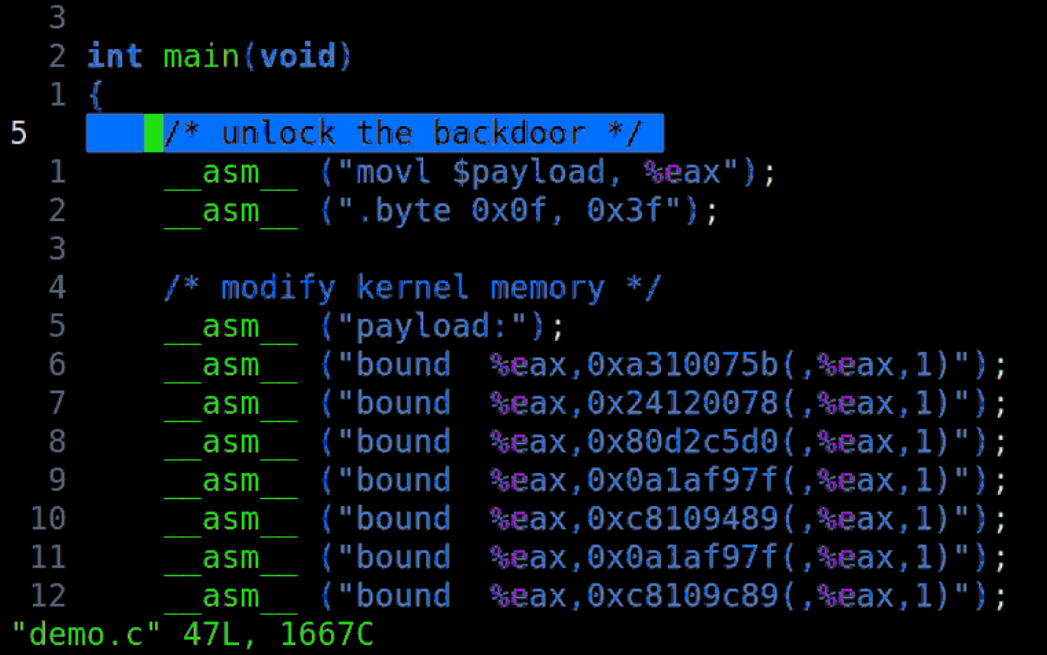
A security researcher named Christopher Domas spoke at the recent Black Hat conference highlighting some x86 CPUs are installed with backdoors that will let hackers seize root access by sending a command to an undocumented RISC core that maintains the primary CPU.
“.byte 0x0f, 0x3f” is the command isn’t supposed to be there in the processor’s hardcoded code. The command will give the attacker root access right away, the security researcher has named the feature as God Mode. The backdoor will completely bypass the protection-ring model of the OS.
The Kernel of the OS runs in ring 0, device drivers run in ring 1 and 2 while the user applications and interfaces run on Ring 3 known as userland which is furthest from the kernel and has the least amount of user privileges.
The exploit discovered by Dasmos will directly take you to the innermost ring with just a few lines of Code.
“We have direct ring 3 to ring 0 hardware privilege escalation,” Domas said. “This has never been done.”
The issue is due to the hidden RISC chip that is present in the bare metal of the chip. “This is really ring -4,” he said. “It’s a mystery, co-located core buried alongside the x86 chip. It has unrestricted access to x86.”
There is also good news as this backdoor only exists in VIA C3 Nehemiah chips that were manufactured in 2003 and used in embedded systems. There is also bad news though, whereby these RISC chips may have been installed on many other chips.
“These black boxes that we’re trusting are things that we have no way to look into,” he said. “These backdoors probably exist elsewhere.”
The security researcher has built his own testing rig and he has obtained seven Nehemiah based thin clients. The backdoor was discovered with great difficulty as the chips would crash many times whilst fuzzing. Finally after many attempts and 15 GB of log data the researcher was able to find the back door. We have attached the code for the exploit which you can download from GitHub
We have also included the video and tweet below:
GOD MODE UNLOCKED: hardware backdoors in some x86 CPUshttps://t.co/Ph0IAL0Pyw
White paper coming tomorrow. @BlackHatEvents pic.twitter.com/qhZ1vFI7pL— domas (@xoreaxeaxeax) August 9, 2018
Take your time to comment on this article.