Hackers used Google Translate’s branding to hide its URL as an attempt to manipulate web users. Users were tricked into clicking on their fraudulent websites after receiving phishing emails. They were then sent to a Facebook link where hackers stole more of their credentials.
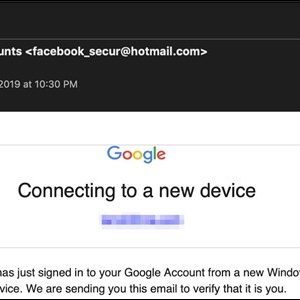
The email subject was a notification to users stating that their Google account was accessed from a new device. A button in the email directed users to what they would interpret as a newly generated Google Translate page. The phishing page link, however, was in the email directly instead of the link to the fraudulent site. So when users clicked anything in the email they were directed to the Google Translate portal page.
Hackers steal users’ credentials
Source: blogs.akamai.com
Viewing this email from a mobile device was harder for users to detect its fraudulency as a user was unable to hover over the screen. In addition, being condensed, it was harder to see the errors. The desktops, however, allowed users to see the imperfections. One was where the Google Translate toolbar was at the top of the phishing page. Hovering over the email revealed further the illegitimacy of the email as it read [email protected].
When a user fell victim to the attack, by typing their username and password, the hacker collected this information and sent it to the attacker. Using this information the attacker went further by sending the same user to a duplicated Facebook. The hacker managed to do this via a script linking the sites together. This was yet another attempt for the hacker to steal more credentials. The Facebook and Google landing page used older versions of the login forms. Other credentials taken throughout the whole attack were Facebook credentials, the user’s IP address and browser type.
Below demonstrates the phishing method.

Source: blogs.akamai.com
The rise of Phishing attacks and how to prevent it
This form of social engineering is on the rise with the recent ENISA Trends report identifying this as one of the most common attacks of 2018. The number of attacks will continue to rise in 2019.
Measures individuals and organisations can take are:
- Check the email address of the sender. Users should hover over the sender details to do this. There is often spelling mistakes or extra punctuation in spam emails. Example: Sender: [email protected] reads when hovered over [email protected] or [email protected]
- If an email is suspicious, check with the sender in a separate email to confirm if they sent the mail. This is before opening the attachment;
- Secure areas storing data to restrict further access. This includes strengthening authentication and access measures;
- Use a phishing prevention tool; and
- Carry out phishing tests to see the effectiveness of measures put in place.