While using encrypted messaging apps, some users may think their conversations and media files exchanged during the chats remained end-to-end-encrypted. However, researchers have recently made a contrary finding. As discovered, a media file jacking vulnerability threatens the security of most Android apps, including WhatsApp and Telegram.
Media File Jacking Vulnerability
Researchers from Symantec have shared a detailed report regarding a media file jacking flaw threatening Android apps. According to their findings, hackers can easily manipulate media files transferred over WhatsApp, Telegram, and other applications. Neither the sender nor the receiving user would ever notice this manipulation. The attack does however only work under certain conditions.
Talking about the exploit in their blog post, Symantec researchers elaborated that hackers can manipulate incoming files on an infected device even before the recipient user actually sees them. This is possible because of a certain time-lapse during the writing of media files on the disk and the following UI prompt.
It stems from the lapse in time between when media files received through the apps are written to the disk, and when they are loaded in the apps’ chat user interface (UI) for users to consume. This critical time lapse presents an opportunity for malicious actors to intervene and manipulate media files without the user’s knowledge.
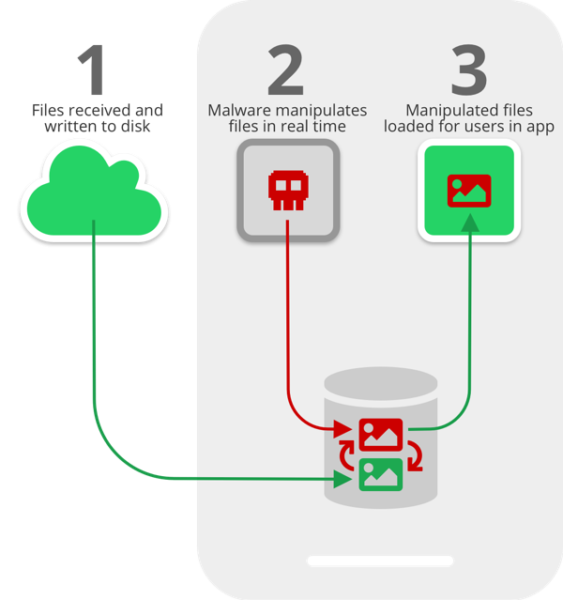
Source: Symantec
The execution of the attack mainly relies on the kind of storage memory. While the device’s internal storage allows app-restricted access only, the external storage clearly allows all apps to access. It means the same external storage is also open to access by a malicious app as well. Hence, if the users choose to store files on the external storage, the files become prone to media file jacking attack. It applies even to WhatsApp and Telegram media files.
Possible Attack Scenarios:
The researchers demonstrated the following three different possible situations of media file manipulation.
- Image manipulation: A malicious app on the recipient device can manipulate the incoming image file (including the thumbnail preview) in real-time.
- Payment manipulation: Hackers can manipulate the billing details in payment invoices tricking the victims to make wrong payments. This manipulation is also possible with PDF files.
- Audio file manipulation: An attacker can meddle with the incoming audio file using deep learning technology, replacing the original message with a fake one – that too – in the original voice of the audio.
Moreover, the researchers fear that such attacks can also contribute to spreading fake news. This can even target Telegram news channels, affecting the credibility of the channel and targeting the receivers with fake news.
Possible Mitigations
To the media file jacking vulnerability, WhatsApp users are more vulnerable since the app has the option of storing media to device’s gallery by default. Whereas, in the case of Telegram, it is an optional feature requiring manual activation by a user.
In either case, the easiest way for regular Android users to mitigate this attack is to stop using external storage.In the case of Telegram, they should not choose Gallery to store media files.To deactivate this option, go to Settings -> Chat Settings -> Save to Gallery.
Whereas, in case of WhatsApp, they should turn this option off via Settings -> Chats -> Media Visibility.
As for more promising solutions, the researchers advise developers to adopt the following measures.
- Storing a hash value in a file’s metadata to validate its integrity prior to writing it to the disk.
- Using non-public directory or internal storage for saving media files.
- Introduce features to encrypt sensitive files.
In 2018, Check Point Research also reported about a similar flaw that they called Man-in-the-Disk attack. The MiTD attack was also possible because of the apps’ access to the device’s external storage.

