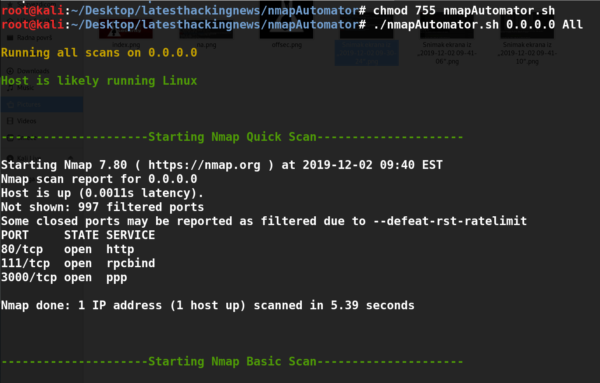
Nmap Automator is a great tool for initial port scans of a given ip address. It automates the scan techniques which I use on each host, I selected it over any other similar tool since it avoids unnecessary scanning.
Installation and usage
git clone https://github.com/21y4d/nmapAutomator

After adding the vulners.nse nmap script to the right directory the tool will use CVE scripts, nikto, smbmap, gobuster to fully scan the target host with the All option:
./nmapAutomator.sh 0.0.0.0 All
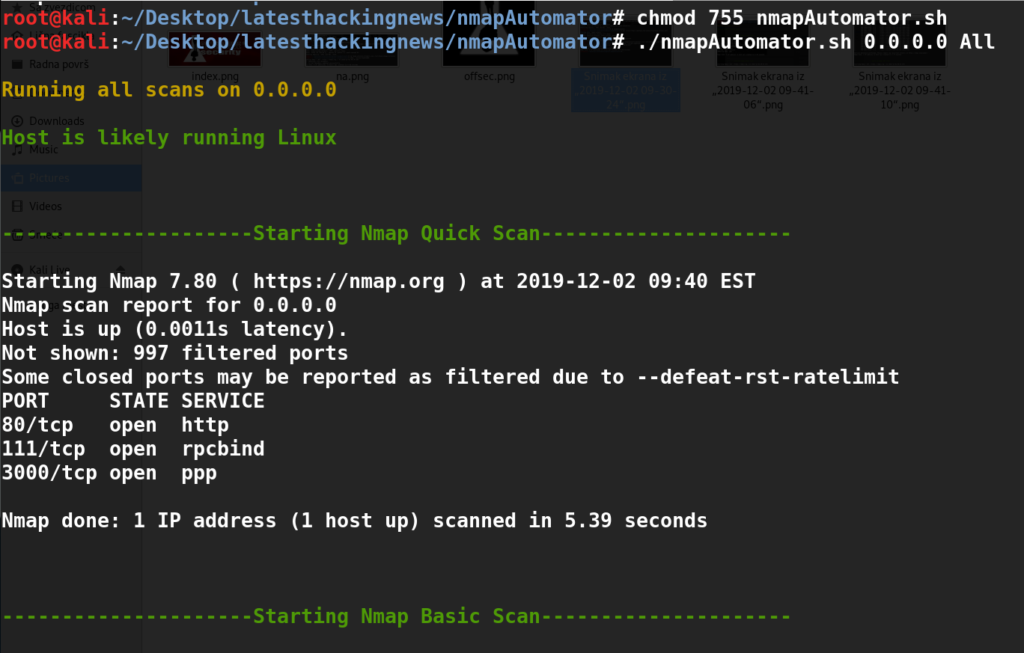
The usage is clear: only the ip address and the scan mode are needed and the script will find and analyse open TCP and UDP ports.
Pros
- The tool is accurate
- It is really fast
- It has all the basic scans included
- The user can poke around with a simple scan result while the full scan is running
Cons
- The tool could have some more functionalities for other ports than http, smb, snmp
What Bunny Rating Does it Get
Nmap Automator is one of the most useful tools for quick identification of potentially interesting ports. It helped me during my OSCP, also it can be used on Vulnhub boxes and HTB to save time. Based on this I will be awarding the tool 4/5 bunnies:




Want To Learn More About Ethical Hacking?
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.