While the reports of Facebook and LinkedIn data dump incidents affecting millions haven’t lost traction, another report has surfaced online. This time, the hackers have dumped data of 70+ million Twitter users for sale.
70+ Million Twitters Users Data Dumped
Researchers from the Italian cybersecurity firm Swascan have found another archive of users’ data for sale on the dark web. Specifically, they found the seller offering over 70 million records including the data of Twitter users.
As elaborated in their post, the seller has offered this archive for $800. Whereas, the details present in the archive include users’ first names, last names, Twitter account, email address, and phone numbers. However, it does not include passwords.
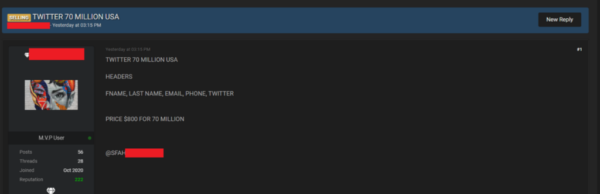
Source: Swascan
Soon after this one, the researchers spotted another offer for the Twitter database from a different user. In that instance, the author simply put up 18 million records online for free. This archive also includes passwords alongside users’ email addresses.
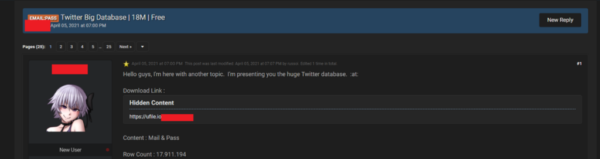
Source: Swascan
Another Web Scraping Activity
Although, it’s unclear how the hackers had managed to collect the data. However, the absence of a password indicates it to be the result of another web scraping activity.
According to the researchers, numerous Twitter scrapping solutions exist online that make such activities quite easy.
Nonetheless, if the data is real, then the presence of users’ phone numbers is alarming. This will be the second time within a few days that users’ phone numbers appeared on the dark web. Recently, Facebook’s data dump of 533 million records also included phone numbers.
It is also possible that this data dump is related to Facebook’s in that the hacker(s) might have used the same strategy (and phone numbers collection) to scrape Twitter data that they might have used for Facebook scraping.
While it’s not possible to entirely prevent such incidents from happening ever. Yet, Swascan advises applying two-factor authentication and frequent updating of passwords to protect the accounts.

