A security researcher has found how one can exploit the Google Play sign-in feature for spying on another user’s location. While this isn’t actually a security flaw, an adversary may abuse it for covert spying without needing to install stalkerware.
Google Play Sign-In Exploit For Spying…
A security researcher from Malwarebytes Labs has discovered how an adversary can abuse Google Play sign-in for spying. All it takes is to log in to Google Play on the target user’s device. It then requires no spyware installation to track the user’s real-time location.
As elaborated in a blog post, Pieter Arntz incidentally found this issue when he logged in on his wife’s phone via his own account. He then missed to sign out, and hence, started noticing the appearance of unvisited locations on his Google Maps Timeline. He found that those locations actually appeared from his wife’s phone.
Initially, the researcher attributed this to the fact that he left his account sign-in on his wife’s device. However, things seemed weird when he noticed the same tracking even after signing out.
Eventually, he discovered that Google had linked his account to his wife’s device that remained unremoved even after logging out.
Moreover, while the researcher received security alerts upon signing in to the new device, his wife didn’t get any notification. That means the target user won’t even receive a notification if a new account links to the device.
The stealth tracking still worked even when the researcher didn’t enable Google Time on his wife’s phone. The only way to stop such tracking was to remove the linked account manually from the other device.
…Is Basically A Design Feature
While this situation may lead to stalking in real-time, the issue isn’t actually a security problem. Rather it’s more of a design feature meant for legit use. Nonetheless, a potential stalker may find it the least detectable method to stalk someone, particularly if the target user isn’t a tech-freak. As Arntz explained,
This situation is not a form of stalkerware, and it does not, by design, attempt to work around a user’s consent. This is more aptly a design and user experience flaw. However, it is still a flaw that can and should be called out, because the end result can still provide location tracking of another person’s device.
Why This Google Play Sign-In Is A Spying Problem
Notably, what made this feature a potential spyware substitute was the lack of any prominent indication for the target user. Unless the target user taps on the small icon bearing the initials of the account signed in on Google Play, it remains difficult to spot that another account has been linked to the device.
This could even become more of a spying tool if an adversary attempts to link an account that would show the same initial.
For instance, two accounts with usernames beginning with ‘A’ would only show ‘A’ when logged in. (The following screenshots from two of my devices are an example.)
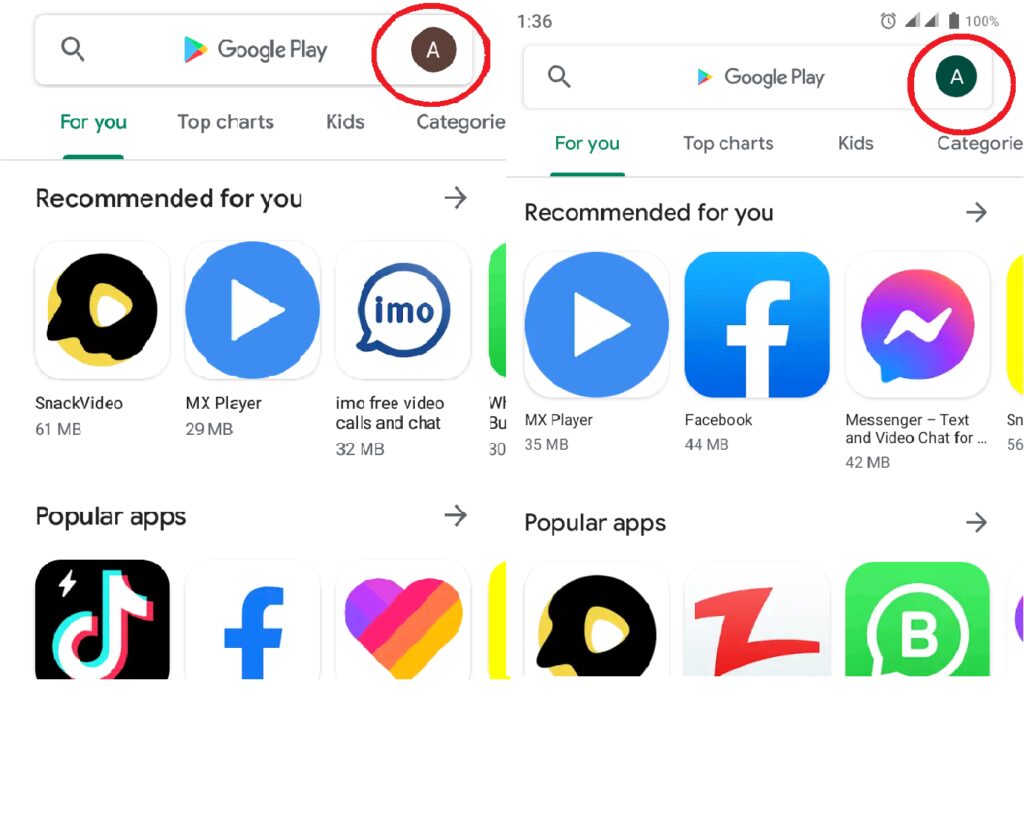
Image: Latest Hacking News
That means unless the target user vigilantly monitors the linked account by tapping the initial, the spying account would remain linked.
According to the researcher, this flaw might not be useful for random cybercriminals. However, it can become a vector in situations of domestic abuse.
In fact, this might become a more viable means of spying since it requires no installation of third-party apps. That’s because a simple account link-up won’t show any identifiable symptoms on the device, such as excessive battery drainage, data usage, device heating up, or others.
So, unless Google devises a fix for it, users must remain careful about this problem. Users can check their devices for the linked accounts via Settings > Accounts (or Accounts and Backups). If any unsolicited accounts appear linked, immediately remove them.
