Phishing attacks keep surfacing online with innovative ways to trick users. The latest phishing campaign is just another example of it, exploiting the name of security firm Proofpoint. The campaign aims at stealing users’ Microsoft Office 365 and Gmail credentials.
Phishing Campaign Exploiting Proofpoint
Researchers from Armorblox have elaborated on an ongoing phishing campaign abusing Proofpoint’s name. As described, the hackers leverage email phishing to execute this campaign, tricking users into entering their login credentials.
Briefly, the attack begins when the target user receives an email apparently from Proofpoint, notifying a file-sharing activity. The email’s subject line mentions “RE:” in a bid to trick the target user into opening the apparent response email. Whereas the message body includes a file sharing alert and the phishing link prompting the user to click.
Once clicked, the user would land at the phishing web page that boasts Proofpoint branding. This webpage includes three login options for different users – Sign-in with Google, with (Microsoft) Outlook, and Office 365. In this way, the campaign typically aims at stealing credentials for Microsoft and Google users alike.
For further legit impersonation, clicking on any of the sign-in buttons would take the user to a new phishing page that mimics the layout of the original service page.
Hence, the target user may enter the login credentials of that account, only to hand it over to the hackers.
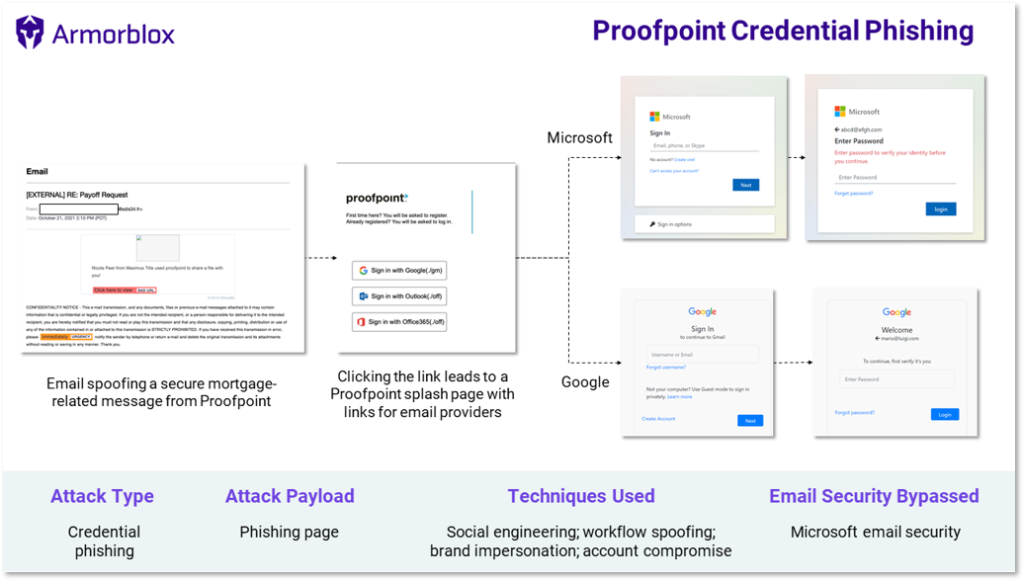
Source: Armorblox
The users need to remain cautious about this phishing campaign as the threat actors use compromised but otherwise legit email addresses to bypass security checks.
Nonetheless, the key to identifying the phishing scam is to check the URL of the respective web pages. Not only do those web links appear different (and weird), but they are also presented with a warning indicator from the browser.
This isn’t the key to detecting this particular phishing campaign. Instead, it broadly applies to all phishing scams. Users should always carefully observe the URLs appearing in their web browsers before entering their credentials. If anything looks different, it’s better to steer clear from such pages.

