Have you ever added items to an online shopping cart, left the website without completing your order, and then found all of the products preserved in the cart when you return? For your information, this is the work of cookie files. They resemble the pebbles that brought Hansel and Gretel out of the thick woods. Cookies help to return the saved information of users when they visit a web application again. But is this always reliable from privacy and security perspectives?
What cookie files are
A cookie file is text information about a user that a website stores in a browser. This could be the visitor’s name, preferred language, or location. When the user returns to a page, the computer checks whether it has a cookie file with the page’s name and sends personal data back to the website. Cookie files can be considered as a kind of memory that helps a web application to identify users and respond accordingly.
The cookie concept emerged in the early 1990s when Lou Montulli, a Netscape developer, faced a challenge. He was engaged in the development of an online store for MCI, where goods added to customer carts were supposed to be stored on the company’s servers. This would greatly complicate the shopping process, as users would need to create personal accounts.
The company assigned Lou the task to come up with a solution that would make it possible to store data on each client’s computer and eliminate the need to log into the system. Trying to resolve the challenge, the programmer reconsidered an already existing idea called “magic cookie” – a data bit that is transferred between two computer programs. It is “magic” because the data in a cookie is often presented as a random key and is only intended for the software that uses it. Lou took the concept of cookies and applied it to the online store and then to browsers in general.
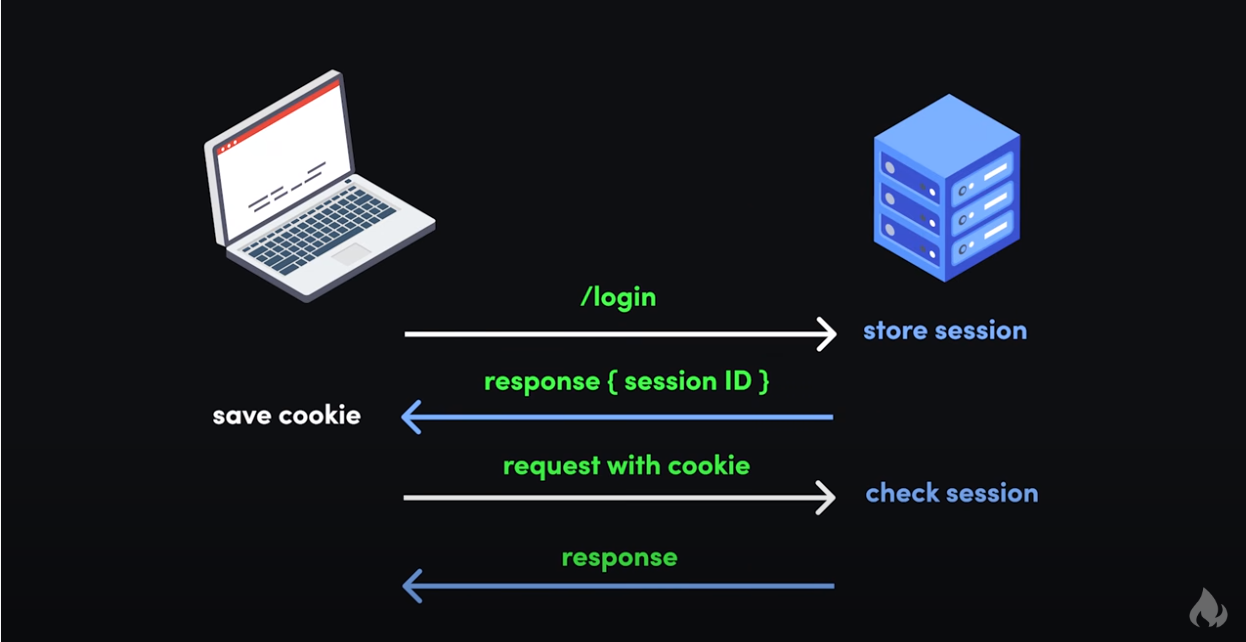
A cookie is akin to a coat check. A user gives their “coat” to the “cloakroom.” In this case, a set of data is bound to them on the server (account, shopping cart, etc.). Then the visitor receives a “coat check” (cookie) that identifies them as the owner of the “coat” and is stored in the web browser. Later, when the user comes back, they can get their “coat” by providing the “coat check.” The browser passes this cookie to the website, reads a unique identifier in the file to remember information about the user’s actions, and resumes their visit from the last point.
Assertive messages like “This site uses cookies: accept or go away” appeared not so long ago. On the 1st of October 2019, the Court of Justice of the European Union ordered that a website user should be asked for consent to store and access cookies. Previously, such a checkbox was on by default, and the data was collected in the same way, but the user knew little about it.
What cookies are used for
Cookies can store the following data:
- personal information (residential address, email, phone number, password, etc.);
- user behavior analysis (for example, viewing products and adding them to the cart);
- session statistics (cookies allow websites to recognize the visitor and remember their preferences – for example, in order to offer sports news rather than political).
Almost all online stores offer the possibility to add items to the cart and leave the website, keeping products preserved there. Having your credentials stored by the browser allows you to quickly enter web apps without filling out forms or remembering passwords. Proposed content is formed based on cookies – on the shopping websites, this function is implemented through the “Related queries” recommendations.
Cookies are an important part of the Internet experience. They are stored locally on your computer to free up space on a website’s servers. Cookies also help applications run faster and more efficiently, ensuring a personalized approach to the user. Without them, websites wouldn’t be able to remember anything about visitors – for example, whether they completed their purchases, whether they are logged in, etc.
Types of cookies
There are different types of cookies, and the user’s security largely depends on this. These types are:
- Session cookies, also known as transient cookies, which are deleted when the visitor closes the browser.
These cookies can be used, for example, to remember what the client put in their cart or when they browsed the website. Also, they are used to ensure security when the client logs into a web banking system or their email. Session cookies are deleted automatically when the session ends, so they are considered more secure than persistent cookies.
- Persistent cookies, which are erased only after a set period of time.
Persistent cookies are stored on a device between sessions, remembering information about a person’s preferences or actions in web apps. For example, every time a user ticks the “remember me” box, they use a persistent cookie for authentication. The storage period for such a cookie is set by the website developer. The user can delete cookies too or configure the browser to clear them after a certain period of time.
- Same-site cookies, which are installed by the website that the user is visiting.
Most session cookies are first-party files.
- Third-party cookies, which are generated by websites the user has never visited.
These are usually pages linked to website ads. Such cookies may be saved even if the visitor hasn’t clicked on them. Thus, the advertiser monitors the actions of all visitors on the websites containing its ads. Marketing cookies are used for tracking a potential buyer and collecting information from different websites.
Why can cookies be dangerous?
In the majority of cases, cookies are useful and convenient – they remember your login information, shopping cart, and language or currency preferences. When a cookie saves personal data, this data is encrypted and protected from attacks using Secure Sockets Layers (SSL). The only computer that can read and decrypt information is the server that created this cookie.
Since the General Data Protection Regulation (GDPR) was signed, websites must display cookie acceptance notifications so that users can choose what information a website can save. In such a way, the law protects visitors from malware and theft of personal information. Since 2019, European web apps have been obliged to warn which cookies they are using before allowing visitors to read their content. Those who break this law run the risk of a serious fine of up to €20 million.
Therefore, website owners should remember that information collected with the help of cookies is considered personal and is regulated by all of the GDPR’s personal data collection guidelines. Nevertheless, cookies can pose serious security risks, depending on how they are used and disclosed. For example, malefactors can hack them; if a cookie is intercepted, a fraudster can impersonate a particular user and gain unauthorized access to data.
The risks associated with cookies can be divided into two categories: fraud and invasion of private life.
Fraud with cookies
Cookie fraud takes the form of a malware attack on a “law-abiding” website or a hijack of an active user session.
- Cross-site scripting (XSS)
This type of fraud means that a malicious cookie, hidden and looking organic on the target page, is placed on a website. The attacker’s code makes the victim’s web browser send cookies to a malicious website. An example of such an attack is when a scammer sends out emails with a special link to a well-known trusted website, or when a website has a testimonial section where someone has placed malicious code that will affect every person who visits the page and reads the comment.
- CSRF attacks
A CSRF (cross-site request forgery) attack is when a malefactor tricks a person into performing a potentially harmful action. For example, when a user visits a comment page and follows a link that is part of a CSRF attack, this action may lead to the loss of credentials.
- Session hijacking
This attack allows a hacker to hijack the user’s active session. When a person opens a website, a session between their computer and this web application is created. For example, a visitor logs into Facebook, and a session begins. The session won’t terminate even if the profile owner closes and then reopens the browser. The end of the session occurs only after clicking on the “Exit” button. In this case, the person needs to log in again to view their page.
Sessions allow users to stay logged in so that they can view various pages and browse the website. Every session generates a cookie with a unique session ID. For example, to log in to Facebook, you need to enter your username and password. Then, a session with a unique identifier is created. Any requests to be made in the application will be authenticated using this identifier. Using malicious code, the fraudster steals the session cookie and its unique number. By recreating the session, the fraudster can use the credit card information to make purchases at the victim’s expense.
Invasion of private life
Most Internet users care about the security of their personal data when it comes to cookies. Many web ad platforms like Facebook, Disqus, Revcontent, and Infolinks are trying to improve user targeting and delivery of relevant ads by collecting more and more data about each client.
According to the Director at the Privacy and Cyber Crime Institute of Ryerson University, 68% of people think that this is a blatant invasion of privacy. As for technological know-how, the majority of the survey respondents (54%) say they understand the function of cookies. Only 40% believe that cookies make people vulnerable. And only a few (13%) think that browsing a website is as anonymous as watching TV.
Conclusion
Is enabling cookies reliable? Yes. Of course, cookies carry some security and privacy risks, but their apparent benefits in providing essential functionality for most modern websites outweigh these risks.
To prevent threats from fraudsters, users should update their browsers, as outdated versions have many security holes. It’s also important to avoid suspicious websites and be careful if your browser warns you of a potential threat. To improve cookie confidentiality, you can set stricter browser settings. Moreover, there are a number of plugins and extensions to manage or automatically delete cookies.
By turning on the incognito mode, a user can surf the Internet without saving cookies. Our computers can be easily protected from any kind of attack with the help of a reliable anti-virus program. And finally, if you are unsure of the legitimacy of the website requesting the cookie, it’s better to leave it.
Cookies are both a complicated and valuable tool for running an online business. They are applied to everything – from conducting analytics to remembering items in your shopping cart. Cookies are not dangerous, but the information they collect about people’s habits is considered personal data. Compliance with such laws as the GDPR and the EU Cookie Law is a hard job, but this is crucial to avoid the worst – client personal information leakage and financial damage.


