Newly discovered vulnerability “Dirty Pipe” vulnerability most Linux distros, giving root access to the attacker when exploited. Linux users must update their systems to receive the fix.
Linux “Dirty Pipe” Vulnerability Found
According to the details shared in a blog post, security researcher, Max Kellermann, discovered a strange bug affecting Linux systems. Named as “Dirty Pipe,” the vulnerability typically allows overwriting of data in read-only files, thus leading to elevated privileges on Linux. In the worst exploitation scenario, such privileges may also include root access as the attacker could inject malicious codes.
Kellerman compared this vulnerability with the previously known “Dirty Cow” bug that affected Android devices. However, “Dirty Pipe” seems easier to exploit.
Briefly, the vulnerability, CVE-2022-0847, caught the researcher’s attention in 2021, when, following a customer complaint, he observed a corrupt log file on the server that triggered gzip to report a CRC error when trying to compress it.
Upon analyzing the matter for some time, the researcher eventually deduced it to be a kernel vulnerability.
elaborating on it further, the researcher stated exploiting the bug required five steps.
1. Create a pipe.
2. Fill the pipe with arbitrary data (to set thePIPE_BUF_FLAG_CAN_MERGEflag in all ring entries).
3. Drain the pipe (leaving the flag set in allstruct pipe_bufferinstances on thestruct pipe_inode_inforing).
4. Splice data from the target file (opened withO_RDONLY) into the pipe from just before the target offset.
5. Write arbitrary data into the pipe; this data will overwrite the cached file page instead of creating a new anonymousstruct pipe_bufferbecausePIPE_BUF_FLAG_CAN_MERGEis set.
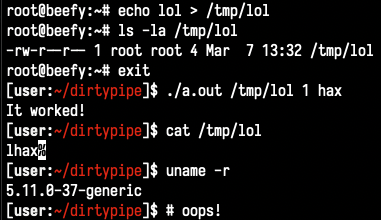
Kellermann has also shared the PoC in his post.
Patch Released
As observed, the bug affects Linux Kernel versions 5.8 and later.
Following his report, the Linux Security Team released bug fixes with Linux 5.16.11, 5.15.25, and 5.10.102 releases.