Researchers have warned Windows users about a new malicious campaign targeting their systems. Posing as a Windows 11 upgrade offer, the fake tool embeds the malware aiming to steal data from target devices. Being new, this malware currently escaped AV detection. Therefore, users must remain vigilant and avoid unofficial Windows 11 resources.
Fake Windows 11 Upgrade Intends To Steal Your Data
According to a recent report from CloudSEK, an Indian cybersecurity firm, a malicious campaign is in the wild, targeting Windows users. The campaign particularly aims at users of old Windows systems as it hides behind a fake Windows 11 upgrade lure.
Briefly, the researchers noticed a new malicious domain, “windows11-upgrade11[.]com,” disseminating a cryptostealer. The site claimed to offer a free Windows 11 system upgrade to attract users.
This domain mimics the legit Microsoft website’s layout to trick users. Hence, an average user might not be able to detect the fraud and may click on the visible “DOWNLOAD NOW” button. (Although noticing the site URL may raise a red flag, most users are not as knowledgeable about noting such things, especially when such sites start appearing in the search results.)
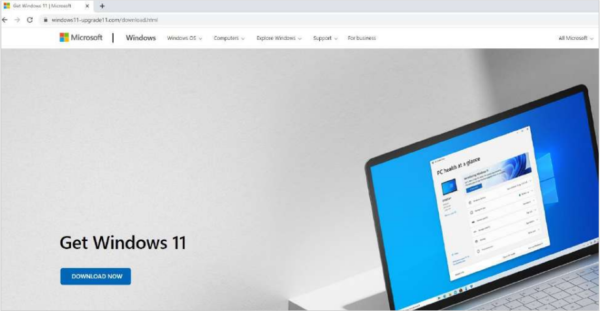
Source: CloudSEK
Clicking the “DOWNLOAD NOW” button downloads a .iso file on the system. (Again, this is similar to how Microsoft offers the Windows setup.) However, the attackers have strived to escape detection by first checking if the incoming request doesn’t come from TOR browser or a VPN.
The malicious .iso file includes the malware loader as an executable (.exe) file. Analyzing the loader revealed that the attackers built this Delphi-based loader using the Inno Setup 6.1.0. free Windows installer.
Executing the malware loader starts the attack by infecting the system with multi-stage malware. The final step involves deploying and running the payload via user32.CallWindowsProcA API.
This payload is also a Delphi-based malware that exhibits the functionalities of a potent stealer. Upon infecting the target system, it steals data from its desktop and web browser. It also steals crypto wallets and stored secrets. The malware stores all the stolen information in the Temp directory, ultimately sending it to the attackers’ C&C server.
Windows Users, Beware!
The recent malware campaign is just another demonstration of how the attackers exploit the average users’ requirements for malicious purposes. Since Microsoft Windows subscription costs are high, people often resort to finding alternative free means to get Windows, neglecting the underlying security risks. Nonetheless, falling victim to any dangerous malware like the one discussed can cause even more damage, including financial ones. Therefore, it’s wise to stick to the official means of getting any software or apps to avoid such threats.
Let us know your thoughts in the comments.

