Researchers discovered a critical security vulnerability in the Screencastify Chrome extension that could allow webcam hijacking. An adversary could exploit this bug to sneakily record videos and steal videos alongside any other data from the Google account where the extension would save the video. Users need to remain careful since the bug remains partially unpatched (until writing this story), thus risking the users.
Screencastify Chrome Extension Vulnerability
Screencastify is a screen recording Chrome browser extension that gained popularity for educational and teaching purposes. The extension allows the user to start screen recording and make videos via webcam. The user can then store ad share these videos with others as needed.
While the purpose sounds useful, any vulnerability in this extension can be equally lethal for a user’s online security.
According to a recent post from Palant, a cross-site scripting vulnerability riddled Screencastify Chrome extension, threatening user security.
The usual functionality of Screencastify includes integration with its website for video-editing features and gaining full access to Google Drive to store recorded videos. Besides, numerous firms own the Screencastify subdomains for various functionalities (excluding hosting companies), which may be prone to XSS vulnerabilities.
Thus, out of curiosity, the researcher analyzed Screencastify web pages and found an XSS flaw on the error page. This error page appears when the user tries to submit another video following a previously uploaded one to a Classroom assignment.
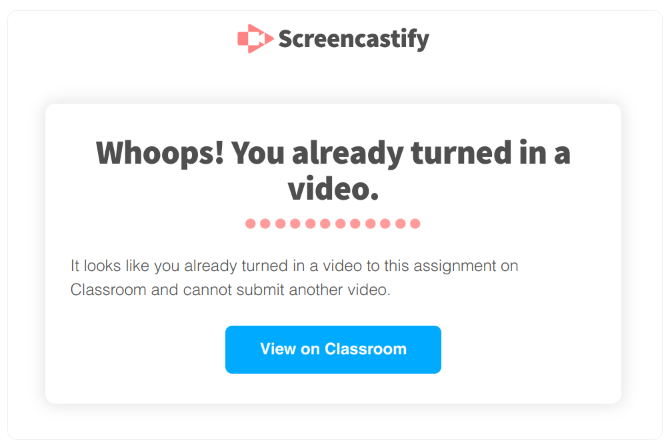
Source: Palant.info
That’s where the problem existed. As stated in the post,
This error page is located under a fixed address, so it can be opened directly rather than triggering the error condition.
Then, while clicking on the “View on Classroom” button should direct a user to a Google Classroom, the vulnerability existed in window.open(this.courseworkLink); where the query parameter this.courseworkLink had no link variation in between. Hence, the page remained vulnerable to clickjacking attacks.
Where does
this.courseworkLinkcome from? It’s a query string parameter. Is there some link validation in between? Nope. So, if the query string parameter is something likejavascript:alert(document.domain), will clicking this button run JavaScript code in the context of the screencastify.com domain? It sure will!
Partial Patch Deployed
An adversary could exploit this vulnerability to retrieve Google OAuth access tokens, access Google Drive contents, and sneakily record videos via webcam.
After discovering the vulnerability, the researcher reached out to the vendors, who acknowledged the bug.
However, the researcher fears that the problem still exists as the vendors have only partially addressed the matter. Until writing this story, Screencastify Version 2.70.0.4517 has arrived with partial fixes, leaving behind a few Screencastify-managed subdomains and one by a single vendor. So, users may expect to receive another update soon with complete fixes. But until then, it’s better to limit using Screencastify to remain safe from potential exploitation.

