What is SSL?
In layman’s terms it is the an algorithm that encrypts a message between a receiver and sender to help avoid the message being read by an attacker should it be intercepted in transmission, for example a website that uses HTTP as opposed to HTTPS offers no protection from an attacker intercepting credentials from the network. For a website to be able to support SSL, it requires an SSL certificate.
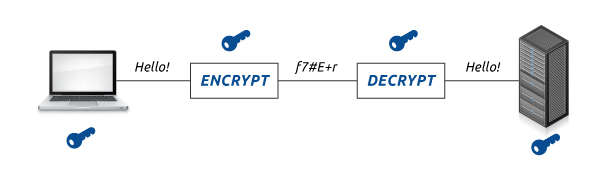
Okay I get the concept, let me see an illustration
So how exactly does an SSL certificate provide protection?
The concept of Secure Sockets Layer is based on the RSA algorithm whereby each SSL Certificate consists of a Public key and a Private key. When sending a secured message the public key is used to encrypt the information and the private key is then used to decrypt the information from the sender. When your browser connects to a secure domain, the server will send a Public key to the browser to perform encryption. The public key is made available for everyone but the private key must be kept secret for integrity. So to reiterate, for a secure communication, the browser encrypts the message using the public key and then sends it to the server. This message is decrypted once the server receives the message using the Private key.
Am i safe then if my site runs over HTTPS?
Not necessarily, there is also the factor of the server SSL/TLS configuration, there are a number of hacking methods and publicly available exploits that target weaknesses in legacy ciphers leaving servers potentially vulnerable to downgrade, brute force attack and even remote data disclosure.
The most famous of exploits discovered that even your granny would have heard of was the one released in April 2014 and given the nickname Heartbleed. This affected OpenSSL 1.0.1 through 1.0.1f and OpenSSL 1.0.2-beta. The vulnerability allowed for a remote (anyone with an Internet connection) attacker to expose sensitive data such as usernames and passwords as well as secret keys, through incorrect memory handling in the TLS heartbeat extension.
Scary stuff, what else?
Well at the time of writing there are a number of cipher weaknesses that could allow an attacker to decrypt SSL traffic, they have also been given comedy names such as:
- BEAST
- POODLE
- CRIME
All of the above target weak SSL ciphers such as RC4, SSLv2, SSLv3, TLS 1.0 TLS 1.1 and so on, also SHA-1 is now widely regarded as deprecated too.
How can an attacker MITM someone who is on the same network if they browse to a HTTPS website?
Well there are a number of Python scripts that are written for these purposes, perhaps the most well known would be SSLstrip, with the latest version aptly named SSLstrip2. This works essentially by using the following methodology:
Victim <== HTTP ==> Attacker <== HTTPS ==> Gmail
The first SSLstrip was mitigated against using HSTS, however of the back of that came SSLstrip2
The video below is a demonstration by the creator showing him using ArpSpoof to redirect traffic through him, and then running SSLstrip2 to perform a HTTP downgrade, this then allows him to read the username and password from the victim as well as email content traversing the network:
I am a website owner, what can I do to check the strength of my SSL configuration?
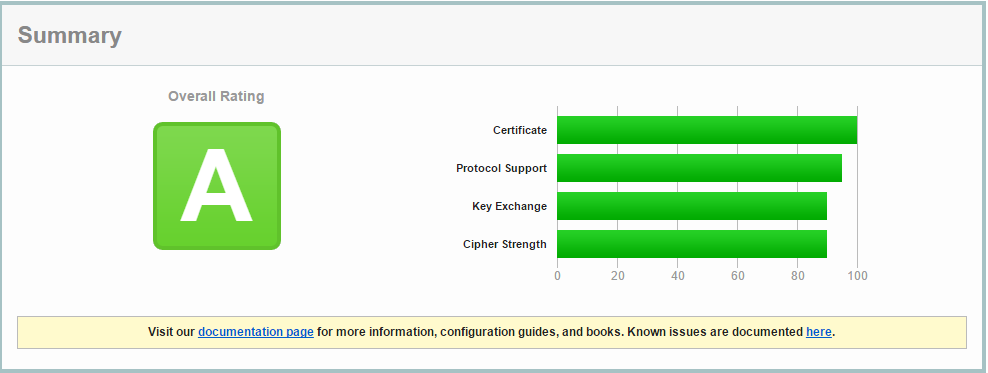
Fortunately there are a number of tools you can use such as SSLscan which is available in Kali by default, however you can also get a very thorough test for free online with the Qualys website, this will give you a rating from A+ to F, you can check for free at the following URL:
https://www.ssllabs.com/ssltest
We got an A ;), room for improvement but not bad
The Qualys tool will give you any recommendations about what you can do to improve, for example ensuring that only TLS 1.2 is the preferred cipher and SSLv2, SSLv3, RC4, TLS 1.0, TLS 1.1 are disabled.
Take your time to comment