Nmap is a free and open source tool for network scanning and security auditing. Many systems and network administrators also see it useful for many tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
It’s the most famous port scanning tool. It can integrate with Metasploit quite easily, storing scan output in a database backend for later use. Nmap helps pen testers scan hosts to identify the running services.
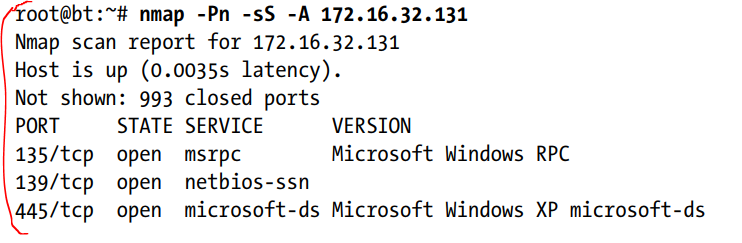
One of the preferred nmap options is “-sS”. The option runs a stealth TCP scan that decides whether a specific TCP-based port is open. Another preferred option is “-Pn”, which instructs Nmap not to use ping to decide whether a system is running; instead, it considers all hosts “alive.” If you’re doing Internet-based penetration tests, you should use this option, because most networks don’t allow Internet Control Message Protocol (ICMP), which is the protocol that ping uses. If you’re performing this scan internally, you can probably ignore this flag.
By using the “-A” option. This option will try advanced service enumeration and banner grabbing, which may give more details about the target system. For example, here’s what we’d see if we were to call nmap with the “-sS” and “-A” options: