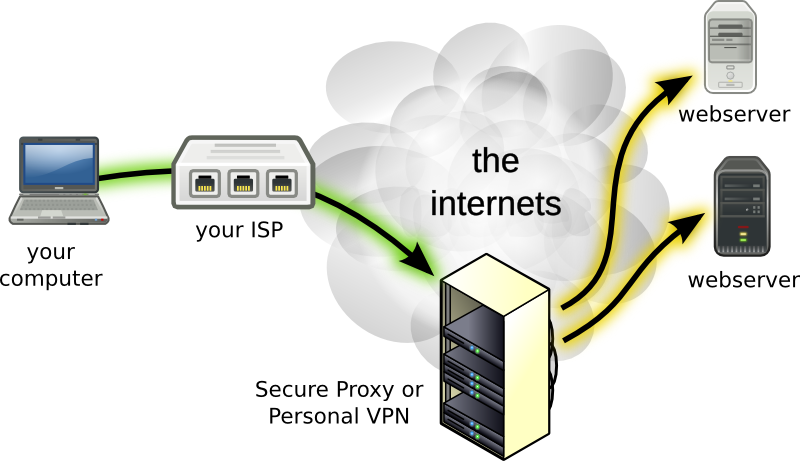
A virtual private network (VPN) protocol is used to build a secure tunnel for communications over an untrusted network. That network can be the Internet or a private network. The VPN can connect two networks or two different systems. VPNs are also effective in giving security for legacy apps that rely against vulnerable communication protocols or methodologies, particularly when communicating across a network.
Point-to-Point Tunneling Protocol (PPTP) is an improvement of PPP that generates encrypted tunnels between communication endpoints. PPTP is used on virtual private networks, but it is usually replaced by the Layer 2 Tunneling Protocol (L2TP), which uses IPSec to implement traffic encryption for VPNs. L2TP was created by combining elements of PPTP and L2F (Layer 2 Forwarding), a VPN protocol from Cisco.
IP Security (IPSec) is a standards-based mechanism for implementing encryption for point-to-point TCP/IP traffic. IPSec has two main elements: Authentication Header (AH) and Encapsulating Security Payload (ESP). Authentication Header provides authentication, integrity, and non-repudiation. ESP provides encryption to secure the confidentiality of transferred data, but it can also make limited authentication.
IPSec is usually used in a VPN in either transport or tunnel mode. In transport mode, the data of the IP packet is encrypted but the packet header is not. In the tunnel mode, the complete packet is encrypted and a new header is appended to the packet to direct transmission through the tunnel.