Installing battery saving apps helps to improve the battery life of smartphones. But, what if that app hacks you? A malicious battery-saver app for that installs ad click malware into hacked android devices along with extracting device information has been identified.
Malicious Battery-Saver App Hacked 60,000 Devices
Google Play Store now carries a malicious battery-saver app that snoops personal data from the hacked device. It also installs adware on the infected device to make money.
Researchers at RiskIQ explained about this scam in their blog post last week. According to them, the attack begins after displaying a pop-up ad on the device, saying that the device needs cleanup, otherwise it would slow down and consume more battery.
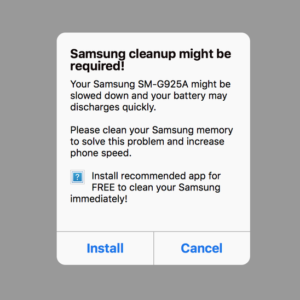
The ad compels the user to trust it by displaying customized content. The source code first detects the device language for specialization. If it finds no specific language, then the ad displays content in English. Next, it scans the device further to trace the model number.
As explained by RiskIQ,
“The pop-up text is customized towards the visitor’s device by parsing the user-agent server-side and embedding the processed brand and model information in the script that renders the pop-up.”
They identified the spam upon noticing a generalized text in the ad, since the source couldn’t detect a model number for desktops.
“The pop-up resulted from a manual visit to the page through a desktop Chrome user-agent. It shows that the user-agent fingerprinting fails on non-mobile visitors, as no model name is contained in browser user-agents. We’re presented with a very generic pop-up when we hit the resource from a desktop browser.”
The ad gives the user the options to ‘Install’ the recommended app or click on ‘Cancel’. However, in either case, the ad redirects the victim to a spammy app on Play Store. This process works for both mobile phones and desktops.
“We’re taken to the Google Play page regardless of whether the code identifies us as a mobile or desktop user-agent, a catch-all approach which could suggest that a relatively unsophisticated group is behind the scam page.
What Are The Risks?
As the researchers said, the scam operators seem a bit unsophisticated if we take a look at the risks associated with this scam. Like most legit apps, this malicious battery-saver app also seeks your permission before installation. You need to allow the app to:
- Access your SMS
- Receive internet data from your device
- Access sensitive data files
- Complete network access
- Pairing with other Bluetooth devices
- Making changes in the system settings
However, the scammers have employed great efforts to make the app look legit, as it literally works like any other power-saving app. It reduces battery consumption, shuts down power consuming applications, and monitors battery status. Thus, a victim could never suspect it to be malware.
Nonetheless, the victim unknowingly installs an ad-clicking bot too that benefit the hackers. Furthermore, the hackers can access the IMEI, contact numbers, brand name, model number, location, and other sensitive data of the infected device.
This isn’t the first report for a malicious Android app. Android users need to be extremely careful while downloading any third-party apps to avoid falling a prey to such hacks.
Let us know your thoughts in the comments section.

