A new technique has been discovered by a developer named Jens “atom” Steube that allows him to easily retrieve the Pairwise Master Key Identifier (PMKID) from a user’s router if it uses WPA/WPA2 security standards.
The above method can be used to crack the WiFi password of a router that is running the latest IEEE standard frequency. Older methods require the capture of the full authentication handshake wheras this new exploit only requires a single frame which can be easily obtained from the Access Point.
This attack was found accidentally while looking for new ways to attack the new WPA3 security standard. WPA3 would be much harder to attack because of its modern key verification protocol called “Simultaneous Authentication of Equals” (SAE).
What’s the difference this and existing handshake attacks?
The main distinction from existing attacks is that in this attack, a capture of a full EAPOL 4-way handshake is not required. The new attack is made on the RSN IE (Robust Security Network Information Element) of a single EAPOL frame.
The new method also reduces the time taken by the script to crack the password
“In fact, many users don’t have the technical knowledge to change the PSK on their routers,” Steube told BleepingComputer. “They continue to use the manufacturer generated PSK and this makes attacking WPA feasible on a large group of WPA users.”
How does it work?
The hack extracts the RSN IE (Robust Security Network Information Element) from a single EAPOL frame. The RSN IE is the optional field that acts as the container to the Pairwise Master Key identifier (PMKID) which is created by the router when a user tries to connect to the WiFi network.
The PMK plays an important part in the 4-way handshake that is used to authenticate both the client and router known Pre-Shared Key (PSK) or the wireless password of the network.
“The PMKID is computed by using HMAC-SHA1 where the key is the PMK and the data part is the concatenation of a fixed string label “PMK Name”, the access point’s MAC address and the station’s MAC address,” stated Steube’s post on this new method.
An overview of the technical Details
A Wireshark screenshot shows that the RSN IE is an optional field that can be found in 802.11 management frames. One of the RSN capabilities is the PMKID.
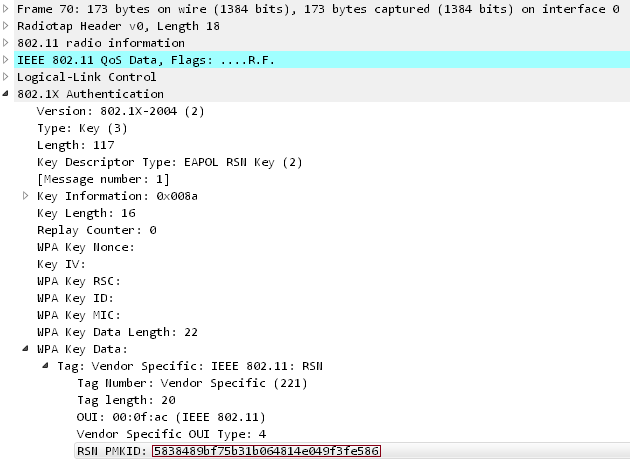
The PMKID uses HMAC-SHA1 where the key is the PMK and the data part is the concatenation of a fixed string label “PMK Name”, the access point’s MAC address and the station’s MAC address as shown below:
PMKID = HMAC-SHA1-128(PMK, “PMK Name” | MAC_AP | MAC_STA)
Read the full technical details HERE
What tools will I need to reproduce this?
In order to make use of this new attack you will need the following tools:
How many routers are affected by this issue?
At Present, we don’t know for which vendors or for how many routers this hack will work, however many experts believe it will work against all 802.11i/p/q/r networks with roaming functions enabled… essentially most modern routers.
Learn more about WiFi Security
If you would like learn all about WiFi ethical hacking from the ground up, we have a 7.5 hour online course with a totally bonkers discount. Get it HERE.

