Security experts at Trend Micro have found a new Ransomware strain named PyLocky which has been involved in attacks between July and August of this year. The malware poses as Locky Ransomware by issuing a seemingly similar ransom note to affected victims. The Ransomware is written in Python and uses PyInstaller to act as a standalone application.
How does it convert the Python Scripts into the executables?
The PyInstaller converts the Python Scripts into a Standalone executable, this is unique from other ransomware as it has Anti-Machine Learning Capabilities and also uses an open-source script called Inno Setup Installer.
“In late July and throughout August, we observed waves of spam email delivering the PyLocky ransomware. Although it attempts to pass off as Locky in its ransom note, PyLocky is unrelated to Locky.” reads the analysis announced by Trend Micro.
“PyLocky is written in Python, a popular scripting language; and bundled with PyInstaller, a tool used to package Python-based programs as standalone executables.”
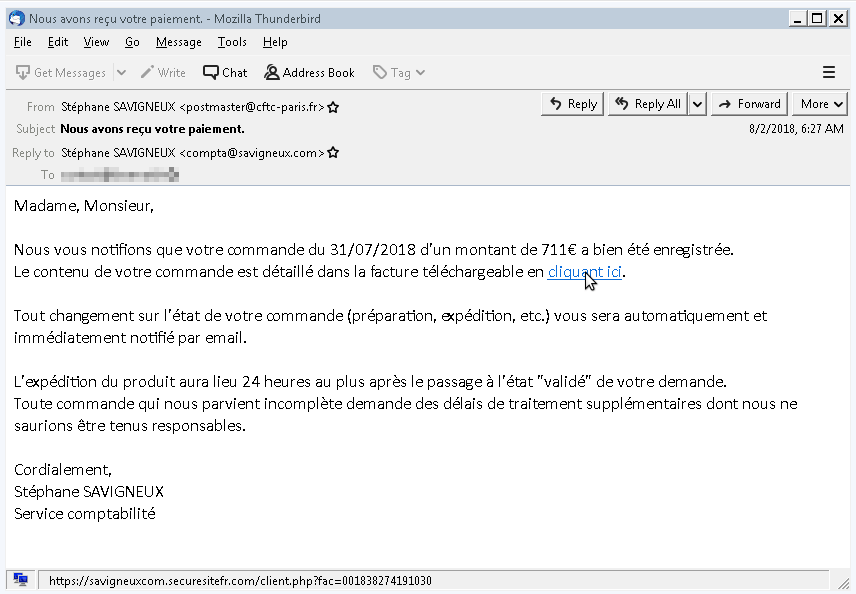
How is the ransomware spreading?
The aim of the ransomware is to bypass static analysis methods using the Inno Setup Installer and PyInstaller which makes it more dangerous. The ransomware was mostly designed to target the population in Europe and France and it is distributed using spam campaigns while the spam messages have started low in volume they have increased over time.
“The malicious URL leads to a ZIP file (Facture_23100.31.07.2018.zip) that contains a signed executable (Facture_23100.31.07.2018.exe). When successfully run, the Facture_23100.31.07.2018.exe will drop malware components — several C++ and Python libraries and the Python 2.7 Core dynamic-link library (DLL) — along with the main ransomware executable (lockyfud.exe, which was created via PyInstaller ) in C:\Users\{user}\AppData\Local\Temp\is-{random}.tmp.” states the report.
PyLocky tries to encrypt the Image, Video, Documents, Sound, Applications, Database and Archive Files before displaying the ransom note. The ransomware is configured to encrypt a hardcoded list of file types, PyLocky also abuses Windows Management Instrumentation (WMI) to check the attributes of the affected system.
How does the Ransomware Work?
The ransomware sleeps for 999,999 seconds approximately 11.5 days before it starts the encryption process in the victim’s computer. The ransomware uses the 3DES (Triple DES) cypher which is already included in the PyCrypto Library which generates a list of files that are encrypted, the ransomware then uses these files to overwrite the original ones. Furthermore the list of affected systems are sent to the Command and Control server which is controlled by the hackers.
Take your time to comment on this article.