Recently, Cisco discovered a critical vulnerability in its Video Surveillance Manager during an internal security review. The vulnerability could allow an attacker to remotely access any target system as a root user and execute arbitrary commands.
Critical Vulnerability Found in Cisco Video Surveillance Manager
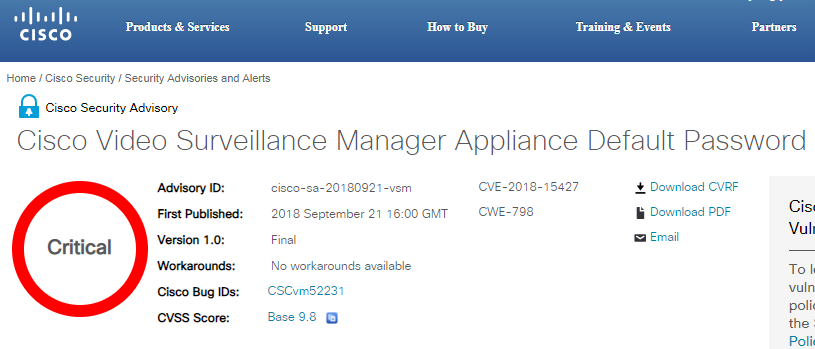
As disclosed by Cisco in a security advisory, a critical vulnerability existed in its Video Surveillance Manager Software that could allow remote attacks. Reportedly, the vulnerability could let an attacker execute arbitrary codes on a targeted system by remote accessing via the root account.
Despite the massive impact, the exploitation path behind it was trivial. As explained in the advisory,
“The vulnerability is due to the presence of undocumented, default, static user credentials for the root account of the affected software on certain systems. An attacker could exploit this vulnerability by using the account to log in to an affected system. A successful exploit could allow the attacker to log in to the affected system and execute arbitrary commands as the root user.”
This VSM Appliance Default Password Vulnerability” (CVE-2018-15427) received a critical severity level with a CVSS base score of 9.8. Regarding why his glitch occurred, Cisco explained,
“This vulnerability exists because the root account of the affected software was not disabled before Cisco installed the software on the vulnerable platforms, and default, static user credentials exist for the account.”
Nonetheless, Cisco did not document the credentials anywhere. Moreover, it also expresses its unawareness regarding any potential malicious exploitation of this flaw.
Cisco Released Patched Software Version
The VSM vulnerability affected software versions 7.10, 7.11, and 7.11.1. That too, if Cisco preinstalled the software running on the Cisco UCS platforms; CPS-UCSM4-1RU-K9, CPS-UCSM4-2RU-K9, KIN-UCSM5-1RU-K9, and KIN-UCSM5-2RU-K9. Whereas, all other versions, such the VSM 7.9 and earlier, or VSM running on VMware ESXi platform remain unaffected by the flaw.
Cisco have released the patched in the Cisco VSM Software version 7.12. Thus, customers can simply switch to the patched VSM version to stay protected from the vulnerability.
The present vulnerability marks the second incident in a row involving video surveillance tools. About a week ago, Tenable discovered zero-day ‘Peekaboo’ vulnerability in the NUOO video surveillance software that allowed remote code execution. NUUO has patched the bug in the latest version 3.9.1 released two days after the vulnerability disclosure.