Cisco has recently fixed a serious privilege escalation vulnerability in its Webex Meetings app. The vulnerability could allow an attacker to execute arbitrary code. Fortunately, two researchers from Counter Hack discovered the bug in the Webex Meetings Desktop app and reported it to Cisco after which they released the patch before any had a chance to exploit it publicly.
Privilege Escalation Vulnerability Discovered In Webex Meetings Desktop App
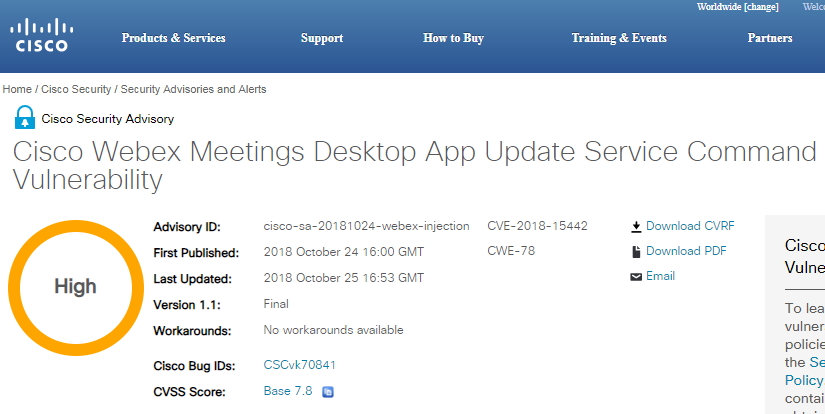
According to a recent security advisory, Cisco has released a patch for a serious security vulnerability in its Webex Meetings Desktop app. The bug could allow a local attacker to execute commands on a system as a privileged user. The flaw existed in the update service of the app.
Describing the flaw, Cisco stated,
“The vulnerability is due to insufficient validation of user-supplied parameters. An attacker could exploit this vulnerability by invoking the update service command with a crafted argument. An exploit could allow the attacker to run arbitrary commands with SYSTEM user privileges.”
Although, an attacker must have local access to the system to exploit this vulnerability, what’s more threatening here is that an attacker could also exploit the bug remotely in certain situations.
According to Cisco,
“…administrators should be aware that in Active Directory deployments, the vulnerability could be exploited remotely by leveraging the operating system remote management tools.”
The Update Command Injection vulnerability CVE-2018-15442 has been classed as a high severity level with a CVSS base score of 7.8.
Patch Released Before Any Exploit
The vulnerability allegedly affected all versions of the Cisco Webex Meetings Desktop App released before v.33.5.6. The bug also affected Cisco Webex Productivity Tools versions between 32.6.0 and 33.0.5 running on Microsoft Windows.
There are no workarounds for the flaw, therefore users must ensure their software is patched. Cisco have fixed the bug in their Webex Meetings Desktop app in 33.5.6 and later. Cisco Webex Productivity Tools 33.0.5 and later contain the fix.
Take your time to comment on this article.