Emotets’ banking trojan has now evolved, it would seem it now has taken on new tactics in the form of hijacking users old email chains and then responding from a spoofed address to portray legitimacy, this additional tactic can heighten a hackers chances when stealing financial information once a victim has been lured into clicking on said malicious content. Targeted emails appears to affect both private and public sectors, including government, particularly those that provide financial and banking services.
Emotet is a known banking trojan, discovered five years ago, first in Europe and the USA. It injects itself into a user’s device via malspam links or attachments, with the intent to steal financial data. It targets banking emails and can sometimes deploy further attacks once inside a device. You can find more news on Emotet in previously written articles such as the following: URLhaus taken down over 100,000 malware websites in 10 months.
This campaign targeted mainly Chile and used living off the land techniques (LotL) to bypass Virus Total detections. This up and coming tactic uses already installed tools on a users’ device to remain undetected for as long as possible.
Emotet’s new tactic
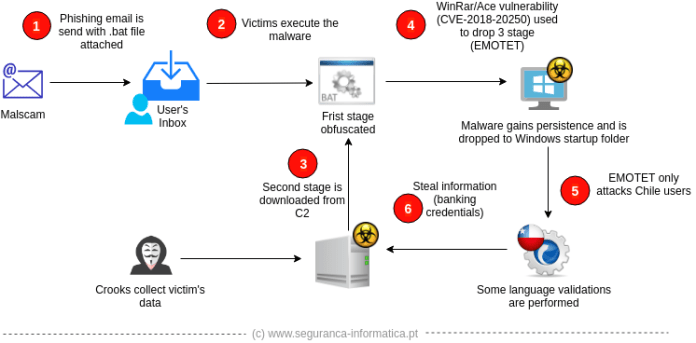
The attachment, labelled “__Denuncia_Activa_CL.PDF.bat,” hides the source code which then downloads from the command and control server. After, it downloads another script. This script exploits the WinRar/Ace vulnerability (CVE-2018-20250) to place the malware into Windows start-up. This prompts device reboot and allows the malware to remain persistent in the system after reboot. The virus is set to attack Spanish/Chilean users, detected by the device’s language preference and geographical location. Alongside Chile, users affected include residents of the USA and Germany. Researchers at Seguranca Informatica, also discovered that the users were from Spanish banks such as the Banco de Chile, Banco Security and Santander.
Emotet continues to pose a big threat to cyberspace as researchers rank its threat level higher than Lockibot and GandCrab ransomware. Users should exercise caution when clicking on email attachments and links, especially chains restarted after a long period of time.

