Note that InfoG 1 is now deprecated, use version 2 instead: https://github.com/Tech-Sec/InfoG.git
InfoG is a Shellscript used to gather information about a target.
It allows the ethical hacker to gather information during the initial phases of a penetration test.
The tool has many features. Some are as follows:
- Check Website info
- Check Phone info
- IP Tracker
- Check Valid E-mail
- Check if site is Up/Down
- Check internet speed
- Check Personal info
- Find IP behind Cloudflare
- Find Subdomains
- Port Scan (Multi-threaded)
- Check CMS
- Check DNS leaking
Let’s Get Started!
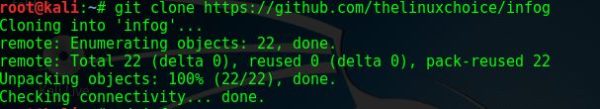
First, we need to install the tool by typing the following command:
git clone https://github.com/Tech-Sec/InfoG.git
Then we change directory to infog by typing the following command:
cd infog
Now, we want to see the content of the directory, so we type the following command:
ls
Your screen should look like that:
![]()
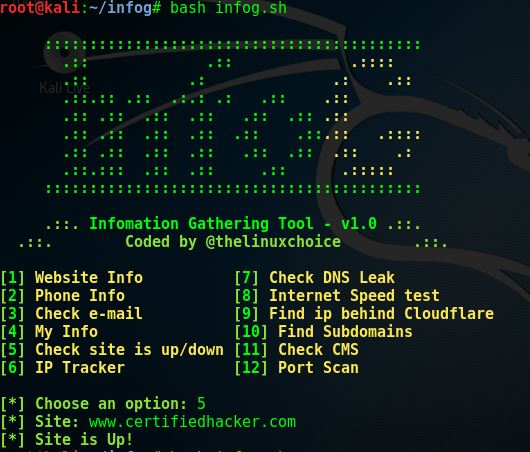
Then we run the tool by typing the following command:
bash infog.sh
The tool will start, and your screen should look like that:
Then, we have a look at the options that are offered by the tool.
You can choose any option of your choice.
As a first test, we are going to check whether the website is up or down. So we type:
5
The tool will prompt us to enter the target website. You can type any website of your choice (where you are authorized to do so).
In our case, we type:
www.certifiedhacker.com
The tool will run the test and will return the results. Your screen should look like that:
The remote host is up. As shown in the above screen shot, the tool printed Site is Up !
Let’s try another test
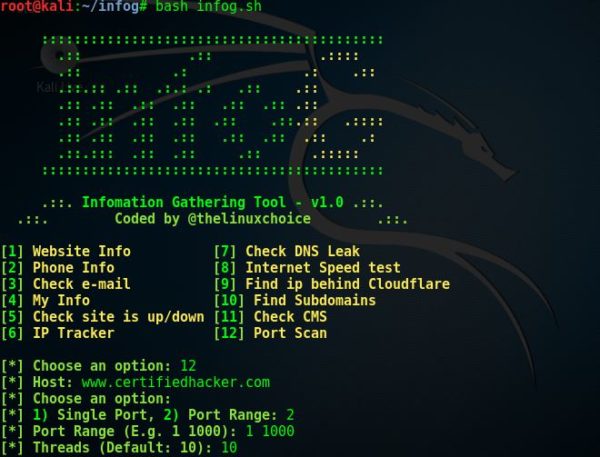
Now, we want to check the open ports of a given website.
Again, we type:
bash infog.sh
then we select option 12 by typing:
12
After selecting the option, the tool will prompt us to enter the host.
So we enter the following:
www.certifiedhacker.com
The tool will ask us if we want to scan a single port or a port range.
We select port range, by typing the following:
2
Then, the tool will prompt us to enter the range of the ports that we would like to scan. In our case, we want to scan from port number 1 to 1000.
So we type:
1-1000
Then the tool prompts us to enter the number of threads. The tool’s default is 10. So we keep it at 10 by typing the following:
10
If you successfully managed to follow the steps, your screen should look like that:
Then our scan will start. And your screen should look like the following screenshots:
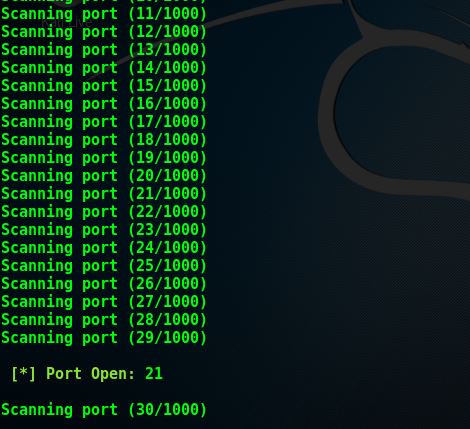
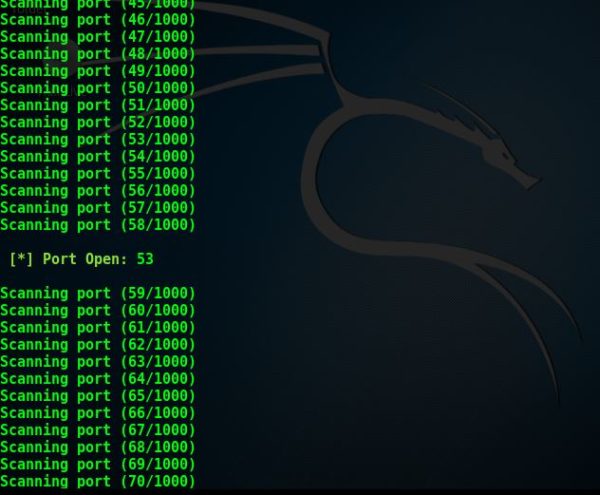
In the above screenshots, the tool is scanning different ports, and it is flagging out the open ones as the scan progresses.
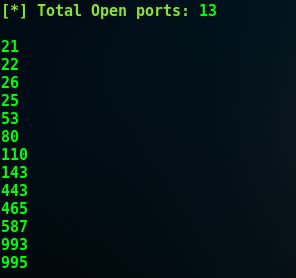
At the end of the scan, the tool will give us a summary of the discovered open ports.
In our case, the scanner printed the following:
There are many other features and options to explore within this tool.
What Bunny Rating Does it Get
This is a useful tool that a penetration tester can add to their toolbox. It also offers cool network related features. I like the DNS leakage feature. CMS feature is also cool. The tool is user friendly. Most of the functionalities work as expected. However, I was not impressed by the results returned when I selected option 1 (gathering information about the target website). In addition, if the website is securely configured not to leak/return information, the tool does not inform us that nothing was returned. As a result, this tool will get 3.5 bunnies out of 5.



![]()
Want to learn more about ethical hacking?
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.