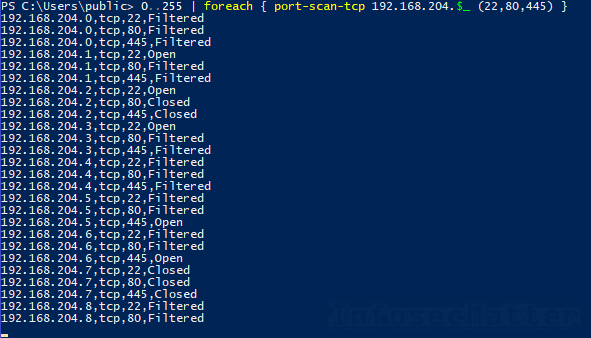
Here we have a compilation of tools by InfoSecMatter that is used for scanning open or closed TCP/UDP ports. It is written entirely in PowerShell and is a great addition to your arsenal when trying to evade AV/WD. Make space on your utility belt for this one because after testing this scanner I am quite impressed with the outcome.
The GitHub repo states that this tool can detect open, closed and filtered ports on both TCP and UDP. Single host scanning, network range or a specific list of hosts from a file. You can also adjust the timeout limit for port scanning. Technically this tool is comprised of 2 different scanners, one for TCP and one for UDP but you can utilize both with one command by creating a separate PowerShell script. It also has a windows login brute force script as well as a SMB bruteforce script as well making this tool one of the best I have used in a while for Pentesting.
Scanner Usage
Using this tool is simple and effective during a pentest, simply download the zip folder from the GitHub repo and copy it to a flash drive. If you have physical access to a machine on the network the next part will be easy, if not you need to figure out a way to spawn a shell and get permissions to run PowerShell commands, but someone else can help you with that. For me it was easy because I already have access to a network.
Next step is to transfer the scripts to a folder that has write privilege. For testing I created a user a simple domain user and went to an unsuspecting work station. I logged in with the user and transfered the files to the C\Users\Public directory then opened PowerShell. After running the scanner I was able to detect open ports on 80, 3389 and 445
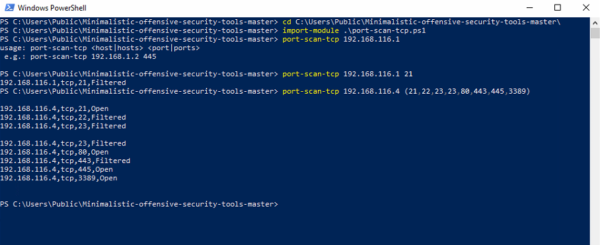
Scanner in action
after checking in the user folder for a list of people that had logged in to the machine I was using, I was able to piece together a short list of usernames to run the AD brute force tool. I ran a check against the default and was able to find 5/11 users who still had the default password.
Conclusion
This scanner and all of its features call for a 4/5 bunnies. During testing I was able to evade our enterprise AV. I know this network, but a good pentester will do their homework before attempting this in a live scenario. Stay tuned for more bangers.




Want to learn more about ethical hacking?
We have a networking hacking course that is of a similar level to OSCP, get an exclusive discount here
Help support LHN by buying a T-shirt or a mug?
Check out our selection here
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.