A serious cross-site scripting vulnerability could have affected thousands of websites upon an exploit. The XSS vulnerability existed in WordPress plugin WP Statistics. A potential attacker could take complete control of a website by exploiting the flaw under specific circumstances.
WP Statistics XSS Vulnerability
Researchers from Sucuri have found a serious XSS security flaw in the WP Statistics WordPress plugin. The flaw could allow an attacker take over a website under certain conditions.
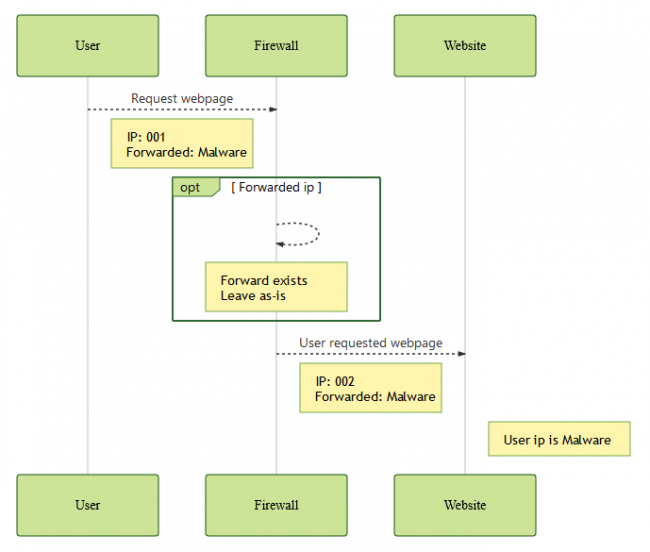
As stated in their blog post, the vulnerability existed in the way a website using the plugin detects a visitor’s IP address. Particularly, for websites using a firewall, an attacker may exploit this vulnerability.
As explained, with default configurations, a visitor’s IP address passes through the firewall to the website. At this stage, the firewall can behave in various ways to pass the visitor’s IP address to the website. The passed IP address can either remain ‘as-is’, is modified by the firewall, or the firewall may modify the IP address, but retain the original IP address in the header without modification.
In the latter case, an adversary may deliberately forward a malicious IP address due to the flaw in the plugin. As stated by the researchers,
The plugin’s vulnerability is based on the scenario where it doesn’t sanitize or validate the user’s IP.
However, a successful exploit also depends on the plugin settings.
The vulnerability can only be exploited when the plugin uses a header to identify the IP address of the visitor.
The firewall configuration should also favor one of the two requirements for a successful exploit.
Either one of the following two conditions must also be met for the exploit: The firewall must be bypassable. OR The firewall must leave the header as-is, if it exists.
Source: Sucuri
Developers Patched The Flaw
After the researchers found the vulnerability, they contacted the developers on June 26, 2019. Then, following their communication, the developers released a fix with updated plugin version on July 1, 2019.
The vulnerability affected WP Statistics plugin versions prior to 12.6.7. The users of this plugin must ensure keeping their websites updated with the latest plugin version (12.6.7) to stay protected from possible exploits.
Take your time to comment on this article.

