Another Android malware has come into the limelight recently. Regretfully, it has already infected 25 millions Android devices predominantly in Asia. Named ‘Agent Smith’, this Android malware has targeted users by replacing legit apps with malicious ones.
Agent Smith Android Malware Campaign
Researchers from Check Point Research have unveiled a malware campaign targeting Android users. Dubbed ‘Agent Smith’, the malware targeted Android devices through various malicious apps. Whereas, to affect the target devices, the attackers tricked users by cloning various legit apps and replacing them with malicious variants.
As stated in their blog post, Agent Smith hides the malicious app’s icon from the launcher and impersonates the existing trusted apps on the target device. Thus, it becomes difficult to catch and remove from the device. The attackers already had a list of some applications that they could replace at the later stages. These includes WhatsApp, Flipkart, Truecaller, MXPlayer, Opera Mini, DoMobile Applock, and others.
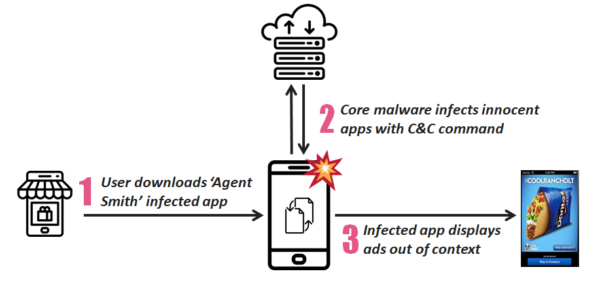
The attackers primarily execute the malware attack in three phases. At first, they trick the user to download a dropper application containing encrypted malware from a third-party app store, such as 9Apps. In the second phase, upon reaching the device, the payload decrypts into the original APK. It then installs the core malware on its own by exploiting known system vulnerabilities. In the third phase, the core malware attacks the applications already present on its target list. As stated in the blog,
The core malware quietly extracts a given innocent application’s APK file, patches it with extra malicious modules and finally abuses a further set of system vulnerabilities to silently swap the innocent version with a malicious one.
Source: Check Point Research
Upon execution, the malware barrages the victim with ads to generate money for the attackers. Nonetheless, the researchers fear this may become more harmful in the future.
Today this malware shows unwanted ads, tomorrow it could steal sensitive information; from private messages to banking credentials and much more.
The researchers have presented a detailed technical analysis of the malware in their report.
Watch Out For These Malicious Apps
As discovered, the Agent Smith Android malware mainly targeted users in the Asian region. Particularly, users in India, Bangladesh, Pakistan, and Indonesia comprise most victims of this campaign. In fact, the campaign caught the attention of the researchers when targeting users in India.
Whereas, the other Asian countries affected by Agent Smith malware include Nepal, Saudi Arabia, Myanmar. To some extent, it also targeted users in other regions, such as the USA, UK, Australia, Hungary, and Nigeria.
Researchers named at least 16 malicious apps executing this campaign. While Google has already taken them down from the Play Store, make sure you do not have any of the following running on your device. In case you do, uninstall the app immediately!
- Color Phone Flash – Call Screen Theme
- Photo Projector
- Rabbit Temple
- Kiss Game – Touch Her Heart
- Girl Cloth Xray Scan Simulator
- Blockman Go: Free Realms & Mini Games
- Cooking Witch
- Ludo Master – New Ludo Game 2019 For Free
- Bio Blast – Infinity Battle: Shoot virus!
- Angry Virus
- Shooting Jet
- Clash of Virus
- Star Range
- Gun Hero – Gunman Game for Free
- Sky Warriors – General Attack
- Crazy Juicer – Hot Knife Hit Game & Juice Blast

